SQL Injection Tutorial.zip_SQLInjectionTutorial_findl4v_luckyr3n

2.虚拟产品一经售出概不退款(资源遇到问题,请及时私信上传者)
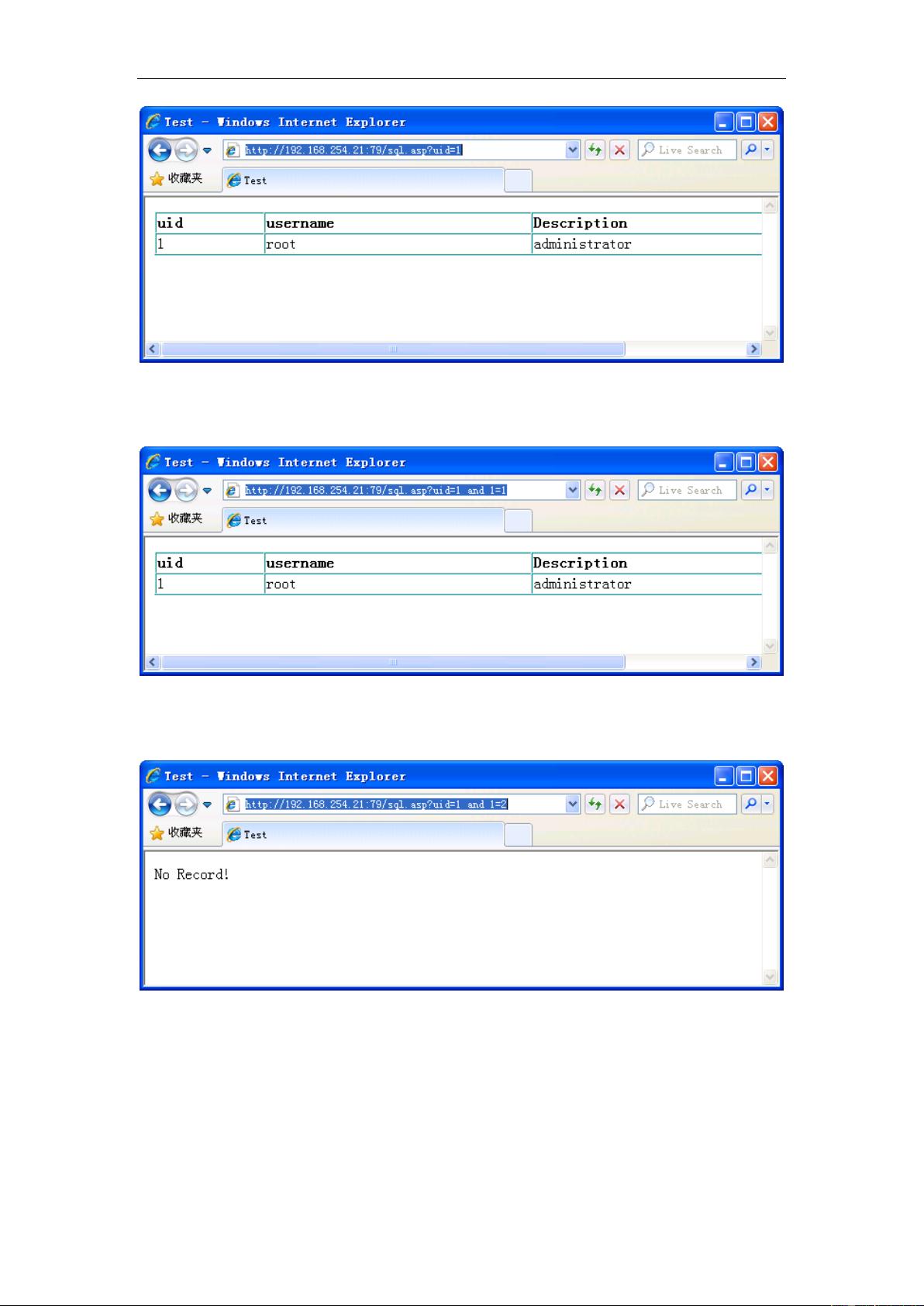
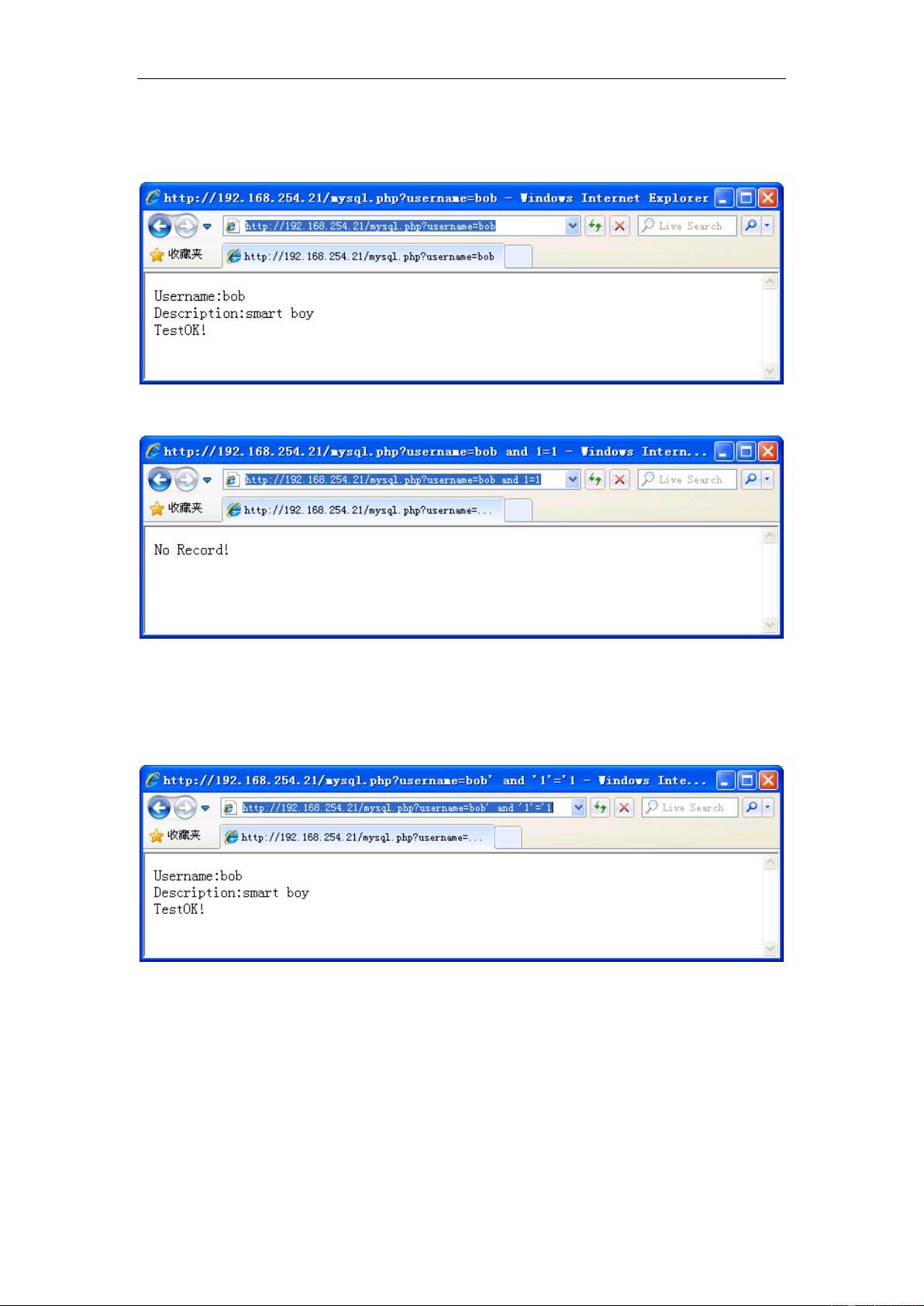
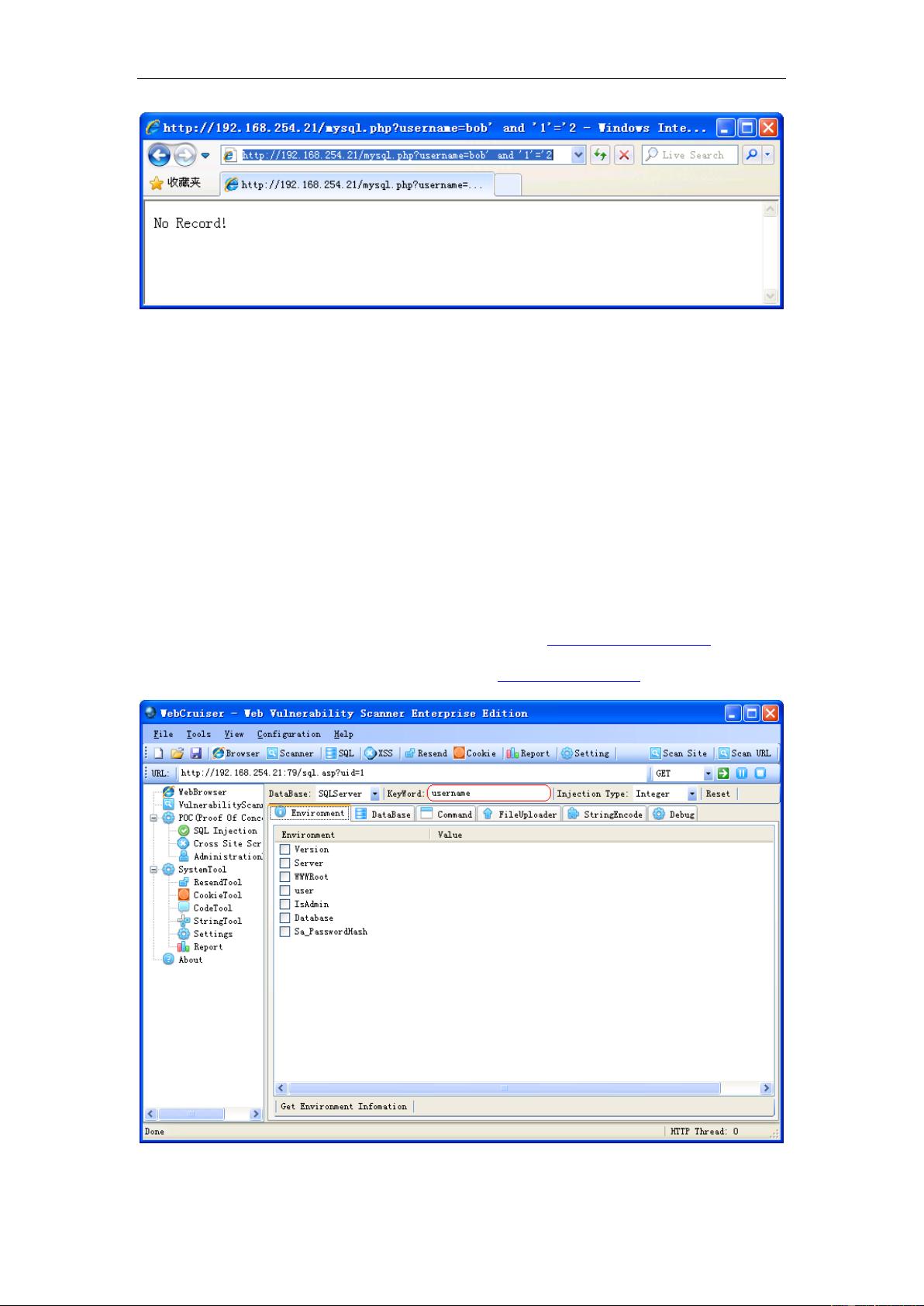
SQL注入(SQL Injection)是一种常见的网络安全威胁,针对使用SQL数据库的应用程序。此教程"SQL Injection Tutorial"由findl4v和luckyr3n提供,旨在帮助读者理解这一攻击手段,学习如何防护以及进行安全编码。 SQL注入攻击发生在攻击者能够通过输入恶意SQL代码来操纵应用程序的SQL查询时。攻击者可以通过不正当的输入,如在登录表单中输入SQL命令,而不是预期的用户名和密码,从而获取敏感数据、修改数据、甚至完全控制数据库服务器。 本教程的PDF文件很可能是对以下内容的详尽阐述: 1. **SQL注入基础知识**:解释SQL的基本概念,以及它是如何被用来构建查询和操作数据库的。 2. **攻击类型**:介绍不同类型的SQL注入,如错误基于的注入、盲注、堆叠查询注入等,以及它们的工作原理。 3. **漏洞识别**:讨论可能导致SQL注入的常见编程错误,如不安全的动态SQL、不适当的输入验证、明文SQL查询等。 4. **攻击示例**:提供实际的攻击案例,展示攻击者如何利用这些漏洞,以及攻击可能产生的后果。 5. **防御策略**:介绍预防SQL注入的最佳实践,如使用预编译语句、参数化查询、输入验证、少用动态SQL、限制数据库权限等。 6. **漏洞检测和修复**:讲解如何检测已存在的SQL注入漏洞,以及如何修复这些问题。 7. **安全编码**:强调在开发阶段应遵循的安全编码原则,以减少引入新漏洞的可能性。 8. **工具和技术**:可能会提及一些用于检测SQL注入的自动化工具,以及相关的安全框架和技术。 9. **最佳实践**:提供在设计和实现数据库应用程序时应遵循的安全准则,以确保长期的系统安全。 10. **案例研究**:可能包含真实世界中的SQL注入攻击案例分析,帮助读者更好地理解和应对这类威胁。 通过这个教程,读者不仅能够理解SQL注入的原理,还能学会如何在实践中应用这些知识,提高自己开发的安全性。对于任何涉及数据库开发和管理的个人或团队来说,这都是一份非常有价值的参考资料。
 SQL Injection Tutorial.zip (1个子文件)
SQL Injection Tutorial.zip (1个子文件)  SQL Injection Tutorial.pdf 744KB
SQL Injection Tutorial.pdf 744KB- 1


- 粉丝: 68
- 资源: 1万+
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 【岗位说明】校长岗位说明书.docx
- 【岗位说明】培训机构老师日常工作职责.docx
- 【岗位说明】培训机构咨询师工作岗位职责.docx
- 【岗位说明】幼儿园各岗位职责01.docx
- 【岗位说明】幼儿园各岗位职责分工.docx
- 【岗位说明】执行管理园长岗位职责说明书.docx
- 【岗位说明】XX药房岗位职责.doc
- 【岗位说明】XX制药厂岗位说明书大全设备部员工岗位职责.doc
- 【岗位说明】XX制药厂岗位说明书大全QC员岗位责任.doc
- 【岗位说明】XX制药厂岗位说明书大全制药厂厂长岗位职责.doc
- 【岗位说明】XX制药厂岗位说明书大全制药厂副厂长岗位职责.doc
- 【岗位说明】XX制药厂岗位说明书大全生产班组长岗位职责.doc
- 【岗位说明】护士岗位说明书.doc
- 【岗位说明】保健食品岗位职责.doc
- 【岗位说明】副主任药师岗位说明书.doc
- 【岗位说明】理疗师岗位职责.doc


 信息提交成功
信息提交成功