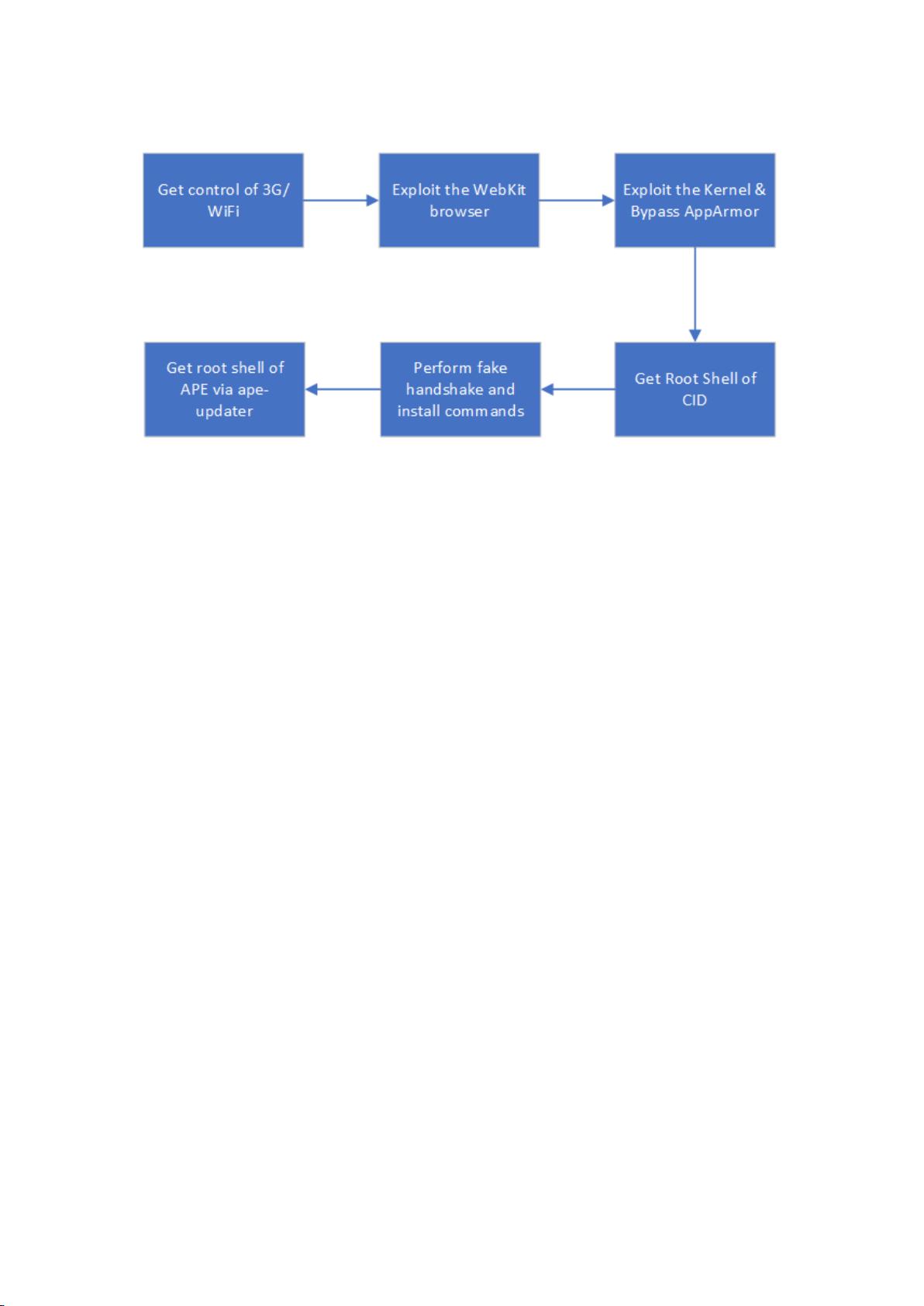
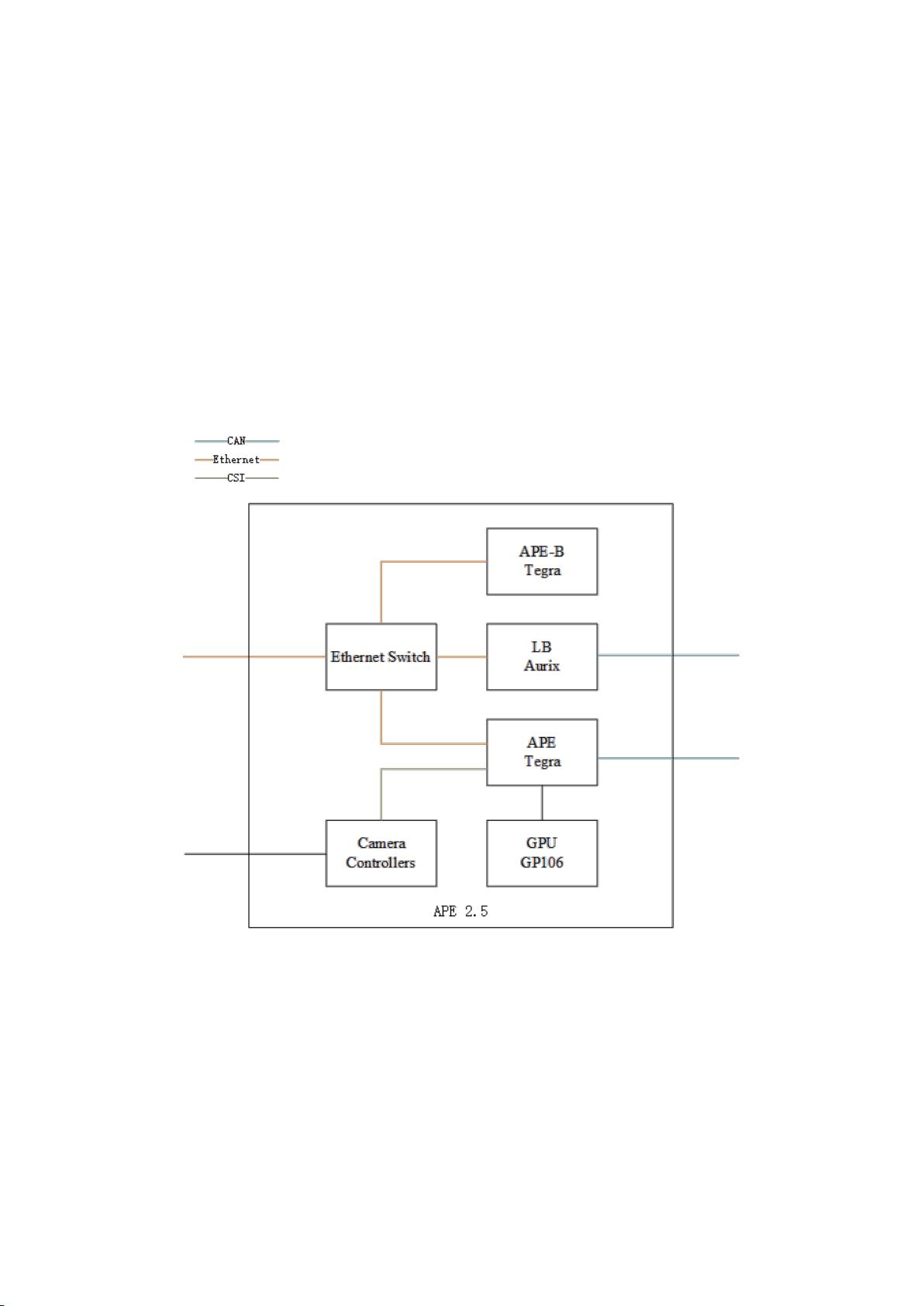
Keen Security Lab has maintained the security research work on Tesla vehicle and shared our research results on Black Hat USA 2017[1] and 2018[2] in a row. Based on the ROOT privilege of the APE (Tesla Autopilot ECU, software version 18.6.1), we did some further interesting research work on this module. We analyzed the CAN messaging functions of APE, and successfully got remote control of the steering system in a contact-less way. We used an improved optimization algorithm to generate adversarial examples of the features (autowipers and lane recognition) which make decisions purely based on camera data, and successfully achieved the adversarial example attack in the physical world. In addition, we also found a potential high-risk design weakness of the lane recognition when the vehicle is in Autosteer mode.



剩余39页未读,继续阅读

- 粉丝: 1
- 资源: 5
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 基于django以及xadmin的在线教育平台。全部资料+详细文档+高分项目.zip
- 基于mysql+django的学生成绩管理系统全部资料+详细文档+高分项目.zip
- 基于Python+Django+MySQL+Redis的商城练手项目(天天生鲜商城项目)全部资料+详细文档+高分项目.zip
- 基于Flask的信息发布,管理系统详细文档+全部资料+高分项目.zip
- 基于Python和Django的后台管理框架!全部资料+详细文档+高分项目.zip
- 基于python2.7.13+django+mysql编写 前端使用layui框架 web扫描器,主要提供子域名扫描,端口扫描,目录扫描,插件扫描的项目功能。还
- 基于Flask开发内网云盘,简单易上手详细文档+全部资料+高分项目.zip
- 基于flask框架的观影清单项目详细文档+全部资料+高分项目.zip
- 基于tensorflow的水果识别小程序,前端采用uni-app框架,后端采用django框架部署在阿里云服务器上。全部资料+详细文档+高分项目.zip
- 基于Flask框架的BBS网站,支持发帖,私信,人脸识别,情绪分类。详细文档+全部资料+高分项目.zip
- 基于Python flask的聚合api详细文档+全部资料+高分项目.zip
- 基于flask框架的数据分析网站详细文档+全部资料+高分项目.zip
- 基于Flask微电影网站详细文档+全部资料+高分项目.zip
- 基于使用 Flask 和 Bootstrap 构建的轻量博客,基于 Git 存储博客内容。支持自动更新、全文检索、Docker 部署详细文档+全部资料+高分项目.zip
- 基于Python Flask框架编写的Web应用作业提交系统,用于收集班级作业详细文档+全部资料+高分项目.zip
- 基于React+flask搭建的跳蚤市场,实现登录注册,图片裁剪,上架下架物品,搜索、收藏物品,聊天等功能详细文档+全部资料+高分项目.zip


 信息提交成功
信息提交成功