1545-5971 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI 10.1109/TDSC.2016.2634161, IEEE
Transactions on Dependable and Secure Computing
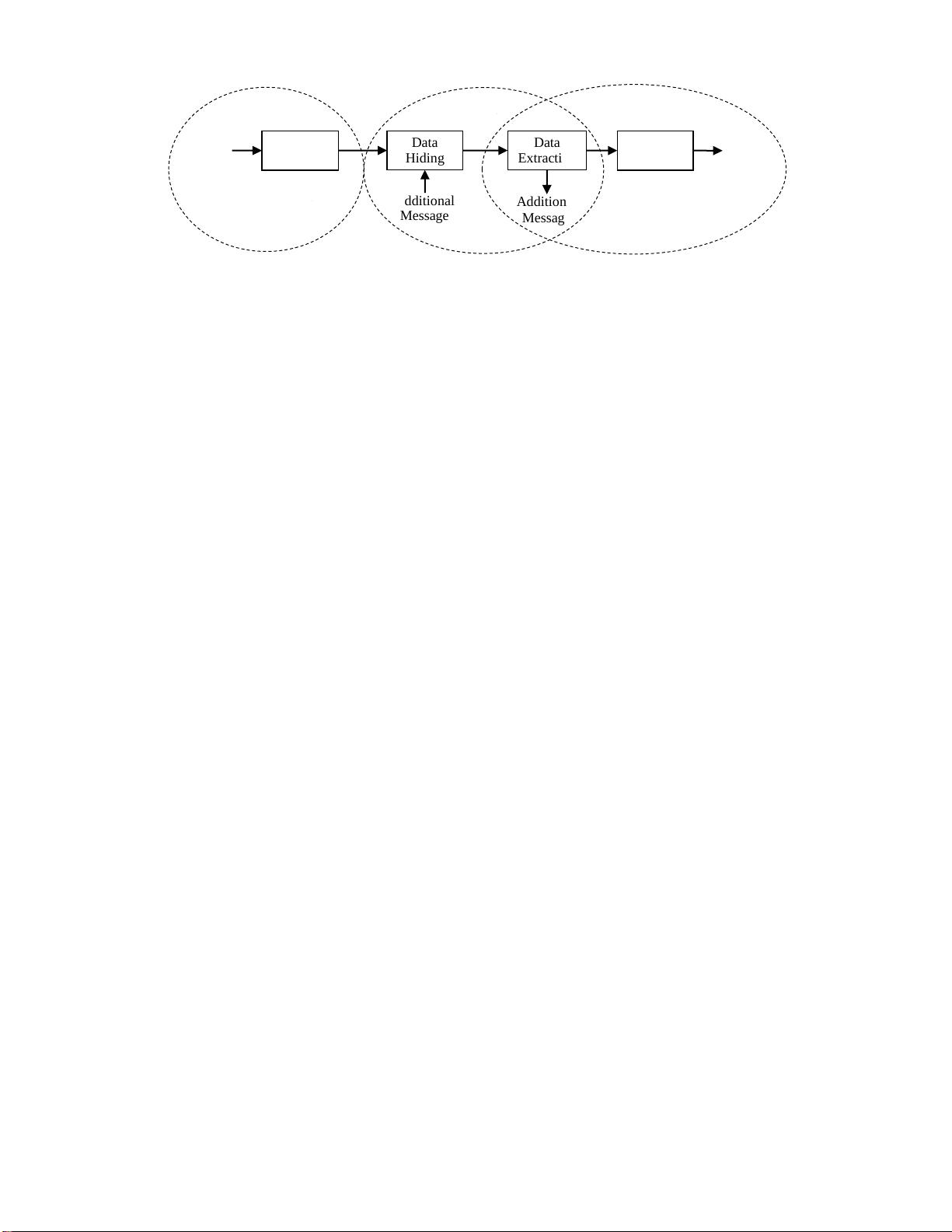
Fig. 2 General framework of RDH-EI
Emerging works on RDH-EI are reviewed in Section II.
While most of the related works are applicable to
uncompressed images, this paper focuses on RDH in
encrypted JPEG bitstream, the most popular image format,
aiming at providing an RDH-EI approach with separable
extraction capability, high embedding capacity, and secure
encryption. We first propose an encryption scheme for
enciphering JPEG bitstreams. Based on JPEG encryption, a
reversible data hiding method is developed for service
providers to embed additional bits. Finally, we propose an
iterative algorithm to recover the original image. In this work,
lossless recovery is required. Although JPEG encoding itself is
lossy, users always hope not to introduce further degradation
to a JPEG image while uploading. That is why lossless
recovery is required.
Compared with our previous work of RDH-EI for JPEG
bitstreams [12], the present method has three contributions.
First, data extraction and image recovery can be separated,
while both features in [12] must be realized jointly. Second, a
rearrangement and enciphering algorithm is proposed to avoid
leaking of image contents, making the present method securer
than the previous JPEG encryption algorithm proposed in [12].
Third, an algorithm for compression and iterative recovery is
proposed to reversibly hide data into an encrypted bitstream.
As a result, a larger embedding payload is achieved. The rest
of the paper is organized as follows. Previous works related to
RDH-EI are surveyed in Section II. The proposed system is
developed in Section III. Section IV provides experimental
results and analyses. The paper is concluded in Section VIII.
II. RELATED WORKS
Generally, an RDH-EI framework has three parties, content
owner, data hider and recipient, as shown in Fig. 2. To
preserve privacy, the content owner encrypts an original image
using an encryption key, and uploads the encrypted copy to a
remote server. On the server side, the data hider embeds
additional messages into the encrypted image using an
embedding key to generate a marked version. The recipient
can losslessly recover the original image using the encryption
key after downloading the marked version. There are two
different cases: both the data hider and recipient can extract
the hidden message; and only the recipient can extract the
message, hence two types of technique: separable RDH-EI
and joint RDH-EI.
A. Separable RDH-EI
The word separable means separating data extraction from
image recovery, i.e., additional messages can be extracted
directly from the marked encrypted image without revealing
the image content. Only those who have the embedding key
can extract the messages from a marked encrypted image.
A separable RDH-EI method was first proposed in [13].
The data hider permutes and divides the encrypted pixels into
segments, and compresses several LSB-planes of each
segment to fewer bits using a pseudo-randomly generated
matrix. As a result, spare room in each segment is created to
accommodate additional messages. On the recipient side,
LSBs of each segment are estimated using the MSBs of the
neighboring pixels. After comparing the estimated bits with
the extracted vectors, the recipient can recover the original
contents. Since the additional message can be extracted
directly from LSBs of the encrypted images, data extraction
and image recovery are therefore separable. This method was
improved in [14] by selecting appropriate bitplanes in the
encrypted image, leading to a higher embedding capacity. In
[15], distributed source coding (DSC) is used to achieve
separable RDH-EI. The data hider compresses some selected
bits in the encrypted image to create room for the additional
hidden message. In this method, the Slepian-Wolf encoder
based on low density parity check (LDPC) is used. With the
DSC based embedding, a much higher capacity is obtained.
With a different idea, [16] creates room for embedded data
in a plaintext image by embedding LSBs of some pixels into
other pixels using traditional RDH for plaintext images. The
pre-processed image is then encrypted by the content owner to
construct an encrypted image. Positions of these evacuated
LSBs in the encrypted image are used to accommodate
additional messages. A large payload, up to 0.5 bit-per-pixel,
can be achieved. Similarly, another method based on
estimation was proposed in [17], in which a large portion of
pixels are used to estimate the rest before encryption. Final
version of the encrypted image is formulated by concatenating
the encrypted estimating errors with the encrypted pixels. On
the server side, additional bits are embedded into the
encrypted image by modifying the estimation errors. In [18],
an RDH-EI method based on patch-level sparse representation
was proposed to explore correlations between neighboring
pixels. After self-embedding encoded residual errors and a
learned dictionary into the original image, the data hider can
embed more secret messages into the encrypted image.
Another RDH-EI approach was realized using histogram shift
and spatial permutation [19]. The method simultaneously
prepares room before image encryption and hides data into the
encrypted image using histogram modification based RDH.
The separable methods proposed in [16]~[21] have high


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功