
A Survey on Hardware-based Security Mechanisms for Internet of Things 3
money, where they do not need to decrypt the public or private keys for stealing cards information [
117
,
172
]. For
instance, in the earlier months of 2017, a number of individuals and businesses around the world were aected by two
huge ransomware attacks, followed by a variant called "Wanacry" which aected 300,000 computers. Petya is another
version of the Ransomware attack, which exploited the existence of a third party software to spread and grow itself
in the networks [
67
,
139
,
181
]. The prevalence of this malware started from Ukraine, where 12,500 computers were
aected. According to Microsoft, this malware has been outspread by using a third-party application [
67
]. Dyn cyber
attack in 2016 that caused distributed denial of service (DDoS) for several Internet platforms and services in Europe
and North America was also a result of insucient security at the IoT nodes [
47
]. These attacks have even penetrated
into remote health monitoring systems. An article published in the Journal of the American College of Cardiology in
February 2018, conrms that cardiac devices can be attacked by hackers leading to severe consequences or even death
in some cases [8].
There are several factors contributing to the immense security vulnerability of IoTs including the limited energy
available at IoT nodes, their low computational capability, the huge number of available nodes in the network as well as
the heterogeneous nature of the network [
137
]. These characteristics, in particular, the number of connected devices,
often result in inecient performance of conventional security mechanisms. By 2020, it is expected that about 31 billion
IoT devices will be connected to the Internet, which drastically increases the need for advanced security mechanisms
for IoT. These devices need to communicate with each other to transmit the data they collected or received from other
devices and intelligently respond and react to the received information. Therefore, it is crucial that information is
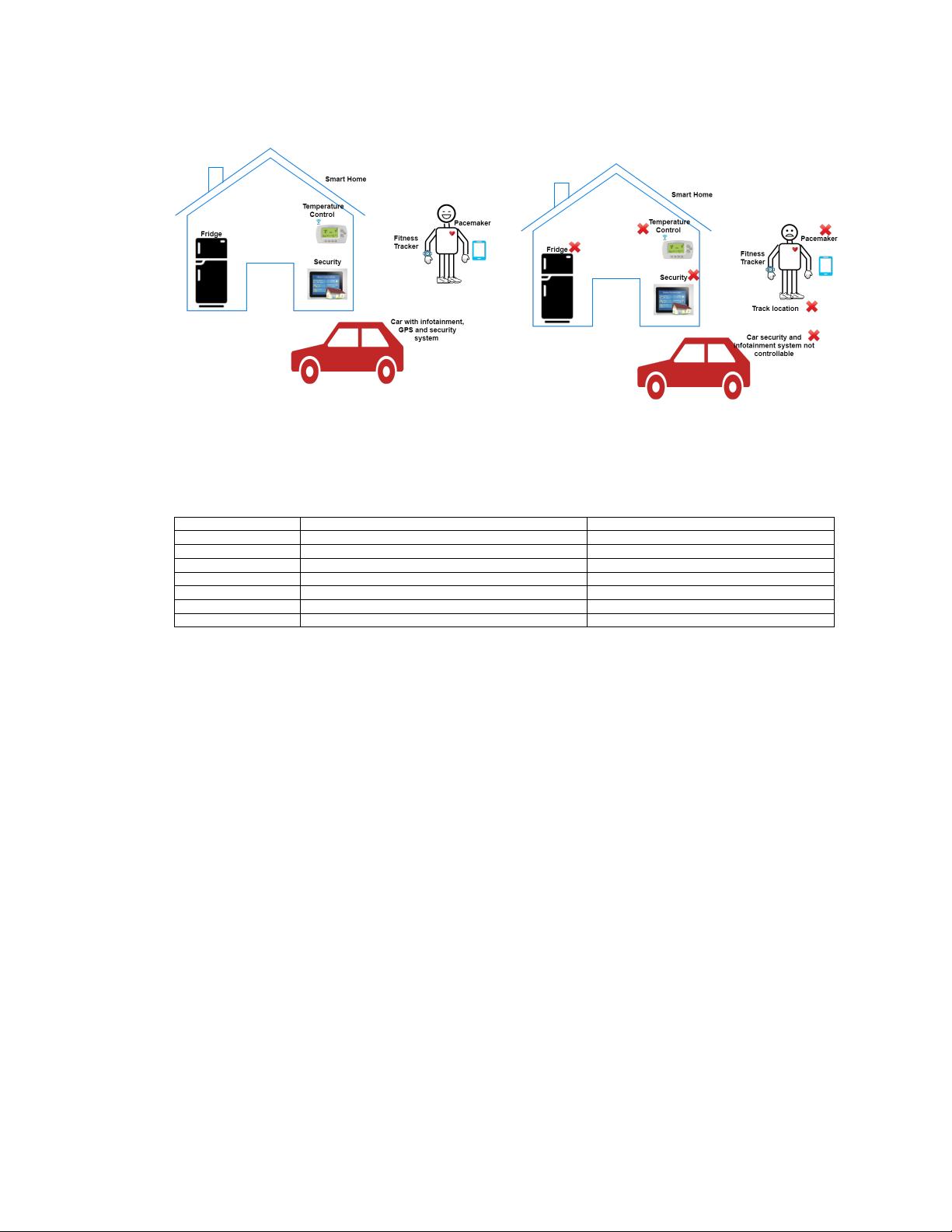
received from and sent to an authenticated user. Figure 2a shows a few examples of IoT devices connected to the
Internet, which can be controlled using the users’ cellphones or smart watches. If these devices are hacked, it can
interrupt the users’ daily life. For example, the user may not be able to use his/her car or even the hacker can induce
a heart attack for the users with implanted pacemakers. Figure 2b shows an example of an attack on an IoT device
that allows remote control over a smart home, a car navigation system and a remote heart monitoring system for a
patient with a pacemaker. The goal of the attacker is to interrupt the communications between dierent IoT nodes and
to manipulate the data being sent, by extracting the cryptographic key. In such scenarios, tamper detection circuits are
needed to prevent the attacks, but these are infeasible in low-power IoT nodes.
The security challenges in IoTs can be broadly classied into identication, authentication, encryption, condentially,
jamming, cloning, hijacking, and privacy. Encryption has been widely used by several mechanisms in order to send
their messages without the risk of being understood by the hackers. Encrypting messages does not allow the hackers to
have access to the messages and eliminates the risk of data manipulation. Hence, cryptographic methods play a crucial
role in the security of IoT systems. Well-known cryptographic mechanisms include Public Key Infrastructure (PKI),
Advanced Encryption Etandard (AES), Data Encryption Standard (DES), and Elliptic Curve Cryptography (ECC) rely on
cryptographic keys [
46
,
143
]. In PKI-based systems, there are two sets of keys for each user, private and public keys.
The private keys need to be kept secret while the public keys can be known by everyone. If one key is used to encrypt a
message, the other key needs to be used in order to decrypt the message. These secret (private) cryptographic keys are
expected to be robust, reliable and reproducible and they are usually stored in the Non-Volatile Memory (NVM) of the
devices. However, the NVMs are highly susceptible to physical attacks.
The cryptographic keys are sensitive information and therefore, several mechanisms have been developed to protect
these keys. White Box Cryptography (WBC) is a software based solution to protect these keys and allow secure
distribution of valuable information [
76
]. WBC requires high processing power and memory and is only applicable to
symmetric cryptographic methods; therefore, it will not be a competing candidate for the security of IoT networks. In
Manuscript submitted to ACM





 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功