没有合适的资源?快使用搜索试试~ 我知道了~
Gartner发布2024年安全运营成熟度曲线:改变安全运营策略、能力和效果的23项技术发展趋势
需积分: 5 2 下载量 148 浏览量
2024-08-01
09:42:00
上传
评论
收藏 1.27MB PDF 举报
温馨提示
安全运营技术和服务通过识别威胁、漏洞和暴露来保护 IT/OT 系统、云工作负载、应用程序和其他数字资产免受攻击。此技术成熟度曲线可帮助安全和风险管理领导者制定战略并提供安全运营能力和功能。 混合和远程工作实践不断发展,安全运营中心 (SOC) 团队支持这些转型。生成式人工智能 (GenAI) 正在撼动网络安全行业,安全运营需要走在前列,利用 GenAI 来改善结果,但也要面对潜在的新攻击。为了跟上不断变化的形势,安全和风险管理 (SRM) 领导者必须制定以业务风险为中心的安全运营策略,而不仅仅是采用新方法来更好地完成相同的工作。
资源推荐
资源详情
资源评论

Gartner, Inc. | G00810451 Page 1 of 81
Hype Cycle for Security Operations, 2024
29 July 2024 - ID G00810451 - 92 min read
By Analyst(s): Jonathan Nunez, Andrew Davies
Initiatives: Security Operations; Meet Daily Cybersecurity Needs
Security operations technology and services defend IT/OT
systems, cloud workloads, applications and other digital assets
from attack by identifying threats, vulnerability and exposures.
This Hype Cycle helps security and risk management leaders
strategize and deliver SecOps capability and functions.
SRM leaders continue to sharpen their threat detection and response efforts. This year’s
Hype Cycle features significant movement for identity threat detection and response
(ITDR), extended detection and response (XDR) and co-managed monitoring services.
SRM leaders are called to action to fortify digital identities and identity infrastructure
using ITDR products and services. Those that have already implemented these
technologies should look to integrate ITDR outcomes into the SOC for improved threat
detection (see 5 Initiatives to Move Toward Security Operations Excellence).
A substantial subset of organizations face challenges with organizing their threat
detection, investigation and response (TDIR) function. Security information and event
management (SIEM) is a mature technology, and recent market shake-ups have created
uncertainty (see Quick Answer: How to React to Recent SIEM M&A Announcements).
Smaller organizations aim at preconfigured technologies that accelerate time to value,
using a predefined set of analytics, prebuilt automation and some out-of-the-box response
capabilities. XDR providers promise to deliver that, and are adding AI assistants to make it
even easier for anyone to get information from the tools.
Enterprises look for partners that can help them handle greater customizability. Co-
managed monitoring services providers offer more flexibility in terms of technologies and
service augmentation, allowing customers to directly contribute to operational
performance and outcomes. Managed detection and response (MDR) providers add
managed incident response for organizations that cannot — or are not willing to —
support this function internally.
This research note is restricted to the personal use of liuyang17@qianxin.com.

Gartner, Inc. | G00810451 Page 2 of 81
Continuous Threat Exposure Management
A number of new profiles appear on this Hype Cycle this year, reflecting evolving
vulnerability and exposure management approaches, more aligned with the continuous
threat exposure management (CTEM) framework:
CTEM is a program helping organizations to improve their maturity when they govern and
operationalize the five recommended phases of exposure management: scoping,
discovery, prioritization, validation and mobilization.
Threat exposure management entered the Hype Cycle last year. Its profile represents a
broader domain, encompassing innovations in processes such as the CTEM approach.
Exposure assessment platforms and adversarial exposure validation solutions are
examples of technology platforms that could be used to execute against threat exposure
management programs. Organizations should employ proper governance and
repeatability to make their threat exposure management programs continuous (see Top
Strategic Technology Trends for 2024: Continuous Threat Exposure Management).
Exposure assessment platforms aim to consolidate vulnerability assessment and
vulnerability prioritization technologies all in one platform. This affords the end user
greater simplicity and potentially greater efficacy in discovering their relevant attack
surfaces, optimizing exposure prioritization and providing greater flexibility in
mobilization.
Adversarial exposure validation technologies offer offensive security technologies
simulating threat actor tactics, techniques and procedures to validate the existence of
exploitable exposures and test security control effectiveness. Within this profile, Gartner
has consolidated breach attack simulation and autonomous penetration testing and red
teaming.
Evaluating the Hype Cycle
Some key recommendations for evaluating this year’s Hype Cycle:
Threat exposure management
■
Exposure assessment platforms
■
Adversarial exposure validation
■
This research note is restricted to the personal use of liuyang17@qianxin.com.

Gartner, Inc. | G00810451 Page 3 of 81
Innovation Trigger
This year’s Innovation Trigger is a call to action for SRM leaders to play a larger role in
transformational security initiatives and be more influential in optimizing existing security
investments. While transformational initiatives like cybersecurity mesh architecture
(CSMA) and CTEM are on the horizon for some, we recommend making incremental shifts
early on the journey, leveraging technology and service consolidation and automation
opportunities, reducing time to value and administrative overhead.
Greater emphasis is being put on achieving a higher degree of threat detection
performance and faster incident response. To do this, more data is often required to
broaden visibility, enabling detections across technology and business domains. However,
staffing and budget limitations are key impediments preventing organizations from
meeting these objectives. Gartner recommends considering technologies that can reduce
data management costs, like those noted in the telemetry pipelines profile, as well as
scaling operational efficiency by leveraging cybersecurity AI assistants.
Peak of Inflated Expectations
Enterprises are aiming to gain visibility of expanding attack surfaces (CPS security, threat
exposure management, cyber asset attack surface management) and test the resilience of
technology domains (penetration testing as a service). Refining their requirements before
going to market can help to avoid unrealistic expectations promoted by vendor marketing
teams. Market capabilities expand and contract; stay aligned with your requirements to
avoid false hype.
Trough of Disillusionment
Consider the objectives and initial steps of transformational initiatives like CSMA to
anticipate long-term evolutions of the security operation function.
■
Initiate tactical or more profound threat exposure management initiatives based on
your current vulnerability management program maturity.
■
Apply rigorous governance of SecOps requirements to fight the marketing noise
around unproven capabilities.
■
Test provider technology and service delivery for assurances of performance
outcomes.
■
Evaluate AI cybersecurity assistants for operational efficiency gains and skills
augmentation.
■
This research note is restricted to the personal use of liuyang17@qianxin.com.

Gartner, Inc. | G00810451 Page 4 of 81
SRM leaders are reevaluating the value they’re getting from technologies in the trough,
often having to reinforce their justification for budgets. For example:
SRM leaders must look for assurances that their services and products are delivering the
expected value.
Slope of Enlightenment
Several innovations this year have shown significant improvements in capabilities
offered, market maturity and customer adoption:
Evaluate these technologies and services to bridge gaps in maturation, whether to
improve threat detection or to operationalize threat intelligence.
Plateau of Productivity
Endpoint detection and response (EDR) and SIEM have reached market maturity with
wide-scale adoption and their benefits well-demonstrated. SRM leaders should look to
these technologies as risk-reducing and incorporate their capabilities into the wider
SecOps ecosystem.
Enterprises were overpromised outcomes (digital forensics and incident response)
■
Enterprises were unprepared to consume and operationalize service output (digital
risk protection services, external attack surface management, ITDR)
■
Enterprises’ adopted technologies that have not kept pace with changing
requirements (security orchestration, automation and response [SOAR], XDR).
■
Co-managed monitoring services
■
Managed detection and response services
■
Network detection and response
■
Threat intelligence products and services
■
This research note is restricted to the personal use of liuyang17@qianxin.com.
Gartner, Inc. | G00810451 Page 5 of 81
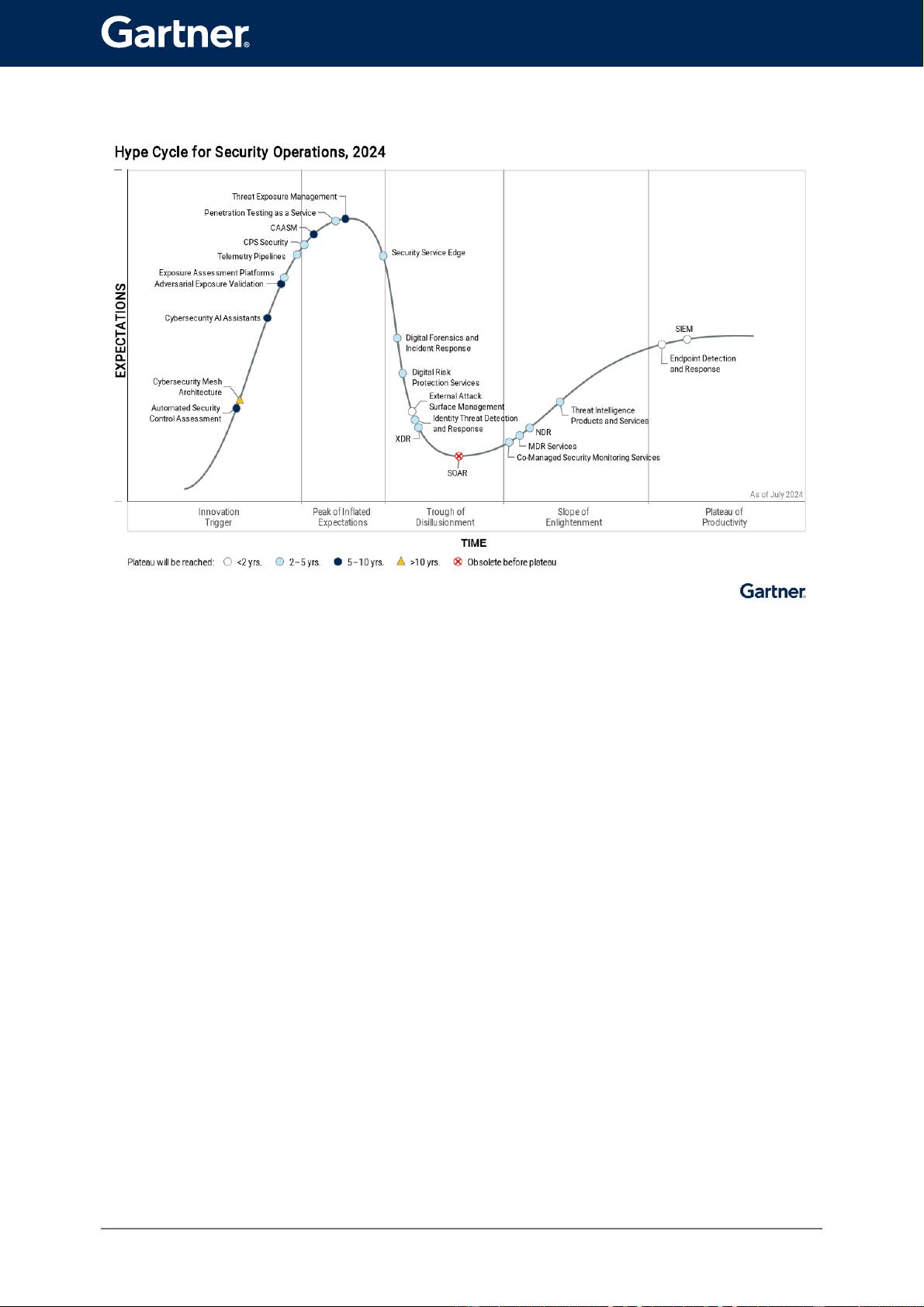
Figure 1: Hype Cycle for Security Operations, 2024
The Hype Cycle
Addressing the complexities of managing organizational exposures continues to be a
dominant theme in this year’s Hype Cycle as the threat landscape has become more
volatile and complex (see How to Respond to the Threat Landscape in a Volatile, Complex
and Ambiguous World). Despite increased volatility and complexity, attackers are
successfully targeting and exploiting vulnerabilities and security weaknesses that have
long been seen as problematic and requiring action. SRM leaders are still, however,
challenged with obtaining visibility into organizational attack surfaces and the
prioritization of those findings.
The Priority Matrix
Organizations that evaluate the risks across the business before investing in any security
operations service and capability will be more easily able to identify what to purchase and
how much to spend. This will allow organizations to get the best risk reduction and
respond effectively to issues that may be damaging to productivity or the brand — or both.
This research note is restricted to the personal use of liuyang17@qianxin.com.
剩余85页未读,继续阅读
资源评论

lurenjia404
- 粉丝: 5448
- 资源: 176
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 该存储库包含MATLAB中的官方代码,用于探索和可视化HUMBI数据集,该数据集在论文HUMBI A Large Mu.zip
- 该软件在论文IR Tools A MATLAB package of iterative regularization.zip
- 该库包含一个用于跨声速导弹系统飞行动态仿真的MATLABSimulink仿真软件.zip
- 该目录包含基于施普林格教科书的课程的讲座文件和Julia和Matlab中的项目代码:FX Giraldo在Tensor.zip
- 感知统一的颜色映射从多个来源编译的MATLAB.zip
- 该项目是关于建立一个8行8位6T SRAM存储器阵列,一个用于访问SRAM阵列的3to8解码器,使用Cadence V.zip
- 该算法在CVPR 2019论文中MATLAB实现,通过凸优化快速抑制单图像反射.zip
- 冈萨雷斯数字图像处理matlab版第二版.zip
- 高阶空间脉冲响应渲染HOSIRR算法的MATLAB实现,是在扬声器上再现双声rir的替代方法.zip
- 冈萨雷斯数字图像处理第三版课后习题答案数字图像处理matlab版源代码及图片 DIP.zip
- 各种机器人相关项目,各种编程语言MATLAB LabVIEW C和技术VREP ROS LEGO Mindstorms.zip
- Java课程设计-标准化试题训练系统源码+题库+文档说明(高分项目)
- ACDCAC型电力电子变压器(pet) MATLAB simulink仿真模型 输入级采用三相pwm整流电路,电压电流双闭环控制策略,中间级双有源桥结构,高频变压器,输出级三相逆变电路 输入电压
- chromedriver-linux64-117.0.5927.0.zip
- 模态ShackHartmann波前传感器工具箱MATLAB.zip
- 模式识别工具箱的MATLAB.zip
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功