没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论

Configuring the SELinux Policy
Stephen Smalley
NSA
sds@epoch.ncsc.mil
This work supported by NSA contract MDA904-01-C-0926 (SELinux)
Initial: February 2002, Last revised: Feb 2005
NAI Labs Report #02-007
Table of Contents
1. Introduction............................................................................................................................................2
2. Architectural Concepts and Definitions...............................................................................................2
2.1. Flask Concepts ............................................................................................................................2
2.2. Flask Definitions .........................................................................................................................4
3. Security Model .......................................................................................................................................4
3.1. TE Model ....................................................................................................................................5
3.2. RBAC Model...............................................................................................................................6
3.3. User Identity Model ....................................................................................................................6
4. Policy Language and the Example Policy Configuration...................................................................7
4.1. TE and RBAC Configuration Overview......................................................................................7
4.2. TE Statements .............................................................................................................................8
4.3. RBAC Statements......................................................................................................................17
4.4. User Declarations......................................................................................................................19
4.5. Constraint Definitions ...............................................................................................................20
4.6. Security Context Specifications ................................................................................................21
4.7. File Contexts Configuration ......................................................................................................24
5. Building and Applying the Policy.......................................................................................................25
5.1. Compiling and Loading the Policy ...........................................................................................25
5.2. Applying the File Contexts Configuration ................................................................................26
6. Configuration Files for Security-Aware Applications ......................................................................26
6.1. Default_Contexts.......................................................................................................................26
6.2. Default_Type.............................................................................................................................27
6.3. Initrc_Context ...........................................................................................................................27
7. Customizing the Policy ........................................................................................................................27
7.1. Adding Users.............................................................................................................................28
7.2. Adding Permissions ..................................................................................................................28
7.3. Adding Programs to an Existing Domain .................................................................................29
7.4. Creating a New Domain............................................................................................................30
7.5. Creating a New Type.................................................................................................................31
7.6. Creating a New Role .................................................................................................................32
1

Configuring the SELinux Policy
References.................................................................................................................................................32
1. Introduction
NSA Security-Enhanced Linux (SELinux) is an implementation of a flexible and fine-grained mandatory
access control (MAC) architecture called Flask in the Linux kernel[LoscoccoFreenix2001]. SELinux can
enforce an administratively-defined security policy over all processes and objects in the system, basing
decisions on labels containing a variety of security-relevant information. The architecture provides
flexibility by cleanly separating the policy decision-making logic from the policy enforcement logic. The
policy decision-making logic is encapsulated within a single component known as the security server
with a general security interface. A wide range of security models can be implemented as security
servers without requiring any changes to any other component of the system.
To demonstrate the architecture, SELinux provides an example security server that implements a
combination of Type Enforcement (TE)[BoebertNCSC1985], Role-Based Access Control
(RBAC)[FerraioloNCSC1992], and optionally Multi-Level Security (MLS). These security models
provide significant flexibility through a set of policy configuration files. An example security policy
configuration was developed to demonstrate how SELinux can be used to meet certain security goals and
to provide a starting point for users [SmalleyNAITR2001][LoscoccoOLS2001].
This technical report describes how to configure the SELinux security policy for the example security
server. Section 2 explains concepts defined by the Flask architecture that are important to configuring the
policy. Section 3 describes the security model implemented by the example security server. The policy
language and the example policy configuration are described in Section 4. Section 5 explains how the
policy is built and applied to the system. Configuration files for security-aware applications are discussed
in Section 6. Section 7 describes how to customize the policy for various purposes.
* Note: This report predates the transition from using the original NSA example policy configuration to using the reference policy,
and the transition from monolithic policy to modular/managed policy. Thus, while some of the discussion herein is still applicable,
much has changed in modern SELinux systems.
2. Architectural Concepts and Definitions
The Flask operating system security architecture provides flexible support for mandatory access control
(MAC) policies[SpencerUsenixSec1999]. The SELinux implementation of the Flask architecture is
described in [LoscoccoFreenix2001]. This section discusses concepts defined by the Flask architecture
that are important to configuring the SELinux policy. It then discusses definitions specified by the Flask
architecture that are used by both the policy enforcing code and by the policy configuration.
2.1. Flask Concepts
Every subject (process) and object (e.g. file, socket, IPC object, etc) in the system is assigned a collection
of security attributes, known as a security context. A security context contains all of the security
attributes associated with a particular subject or object that are relevant to the security policy. The
content and format of a security context depends on the particular security model, so a security context is
only interpreted by the security server. In order to better encapsulate security contexts and to provide
2

Configuring the SELinux Policy
greater efficiency, the policy enforcement code of SELinux typically handles security identifiers (SIDs)
rather than security contexts. A SID is an integer that is mapped by the security server to a security
context at runtime. SIDs are nonpersistent and local identifiers, and must be translated to security
contexts for labeling persistent objects such as files or for labeled networking. A small set of SID values
are reserved for system initialization or predefined objects; these SID values are referred to as initial
SIDs. Kernel SIDs are not exported to userspace; the kernel only returns security contexts to userspace.
However, userspace policy enforcers may have their own SID mappings maintained by the userspace
AVC that is included in libselinux.
When a security decision is required, the policy enforcement code passes a pair of SIDs (typically the
SID of a subject and the SID of an object, but sometimes a pair of subject SIDs or a pair of object SIDs),
and an object security class to the security server. The object security class indicates the kind of object,
e.g. a process, a regular file, a directory, a TCP socket, etc. The security server looks up the security
contexts for the SIDs. It then bases its decision on the attributes within the security contexts and the
object security class. The security server provides two major kinds of security decisions to the policy
enforcement code: labeling decisions and access decisions.
Labeling decisions, also referred to as transition decisions, specify the default security attributes to use
for a new subject or a new object. A process transition decision is requested when a program is executed
based on the current SID of the process and the SID of the program. An object transition decision is
requested when a new object is created based on the SID of the creating process and the SID of a related
object, e.g. the parent directory for file creations. These default labeling decisions can be overridden by
security-aware applications using the SELinux API. In either case, the use of the new label must be
approved by an access decision or the operation will fail.
The policy enforcement code is responsible for binding the labels to subjects and objects in the system.
For transient objects such as processes and sockets, a SID can be associated with the corresponding
kernel object. However, persistent files and directories require additional support to provide persistent
labeling. Security contexts are stored persistently for files and directories using extended attributes,
specifically the security.selinux attribute.
When converting an existing system to using SELinux, the extended attribute values for all files are
typically initialized by a utility called setfiles from a file contexts configuration that specifies security
contexts for files based on pathname regular expressions. If the Linux distribution already includes
SELinux support, then the extended attributes will typically be set at install time by the corresponding
package manager for the distribution, which may also be enhanced to use the file contexts configuration
to determine the appropriate security context. Subsequently, the mapping is maintained dynamically by
the policy enforcing code to reflect create, delete, and relabel operations.
The file contexts configuration is logically separate from the policy configuration. The file contexts
configuration is not part of the kernel policy and is only used by userspace programs when initializing or
resetting the extended attributes to their install-time values. The extended attribute values are then used at
runtime by the policy enforcing code. The policy configuration is used by the security server and is
needed to obtain security decisions. The policy configuration specifies security decisions based entirely
on security attributes, whereas the file contexts configuration specifies security contexts for files based on
pathnames. Using the pathname is only suitable for initial installation of the file; subsequently, the
security attributes of the file should be tracked during runtime based on policy.
Access decisions specify whether or not a permission is granted for a given pair of SIDs and class. Each
object class has a set of associated permissions defined to control operations on objects with that class.
These permission sets are represented by a bitmap called an access vector. When an access decision is
3
Configuring the SELinux Policy
requested, the security server returns an allowed access vector containing the decisions for all of the
permissions defined for the object class. These access vectors are cached by a component of the Flask
architecture called the Access Vector Cache (AVC) for subsequent use by the policy enforcement code.
The AVC component provides an interface to the security server to support cache management for policy
changes.
In addition to providing an allowed access vector, the security server provides two access vectors related
to auditing. An auditallow decision indicates whether a permission check should be audited when it is
granted. For example, if a permission is associated with a highly sensitive operation, it may be desirable
to audit every use of that operation. An auditdeny decision indicates whether a permission check should
be audited when it is denied.
2.2. Flask Definitions
A small set of configuration files are shared between the SELinux kernel module and the example policy
configuration. These files define the Flask security classes, initial SIDs, and access vector permissions.
This information is not specific to any particular security model, and should rarely change. Changes to
these files require recompilation of the module and policy, and will typically require updates to the
module and policy to use the new values. These files do not need to be modified to configure the security
model implemented by the example security server.
The meaning of the security classes and access vector permissions in the original SELinux
implementation was described in [LoscoccoNSATR2001] and [LoscoccoFreenix2001]. Changes made
for the LSM-based SELinux implementation are described in [SmalleyModuleTR2001].
The source for these files is located in the policy/flask subdirectory of the policy sources. These files
are installed into /etc/selinux/(targeted|strict)/src/policy/flask and are used when the
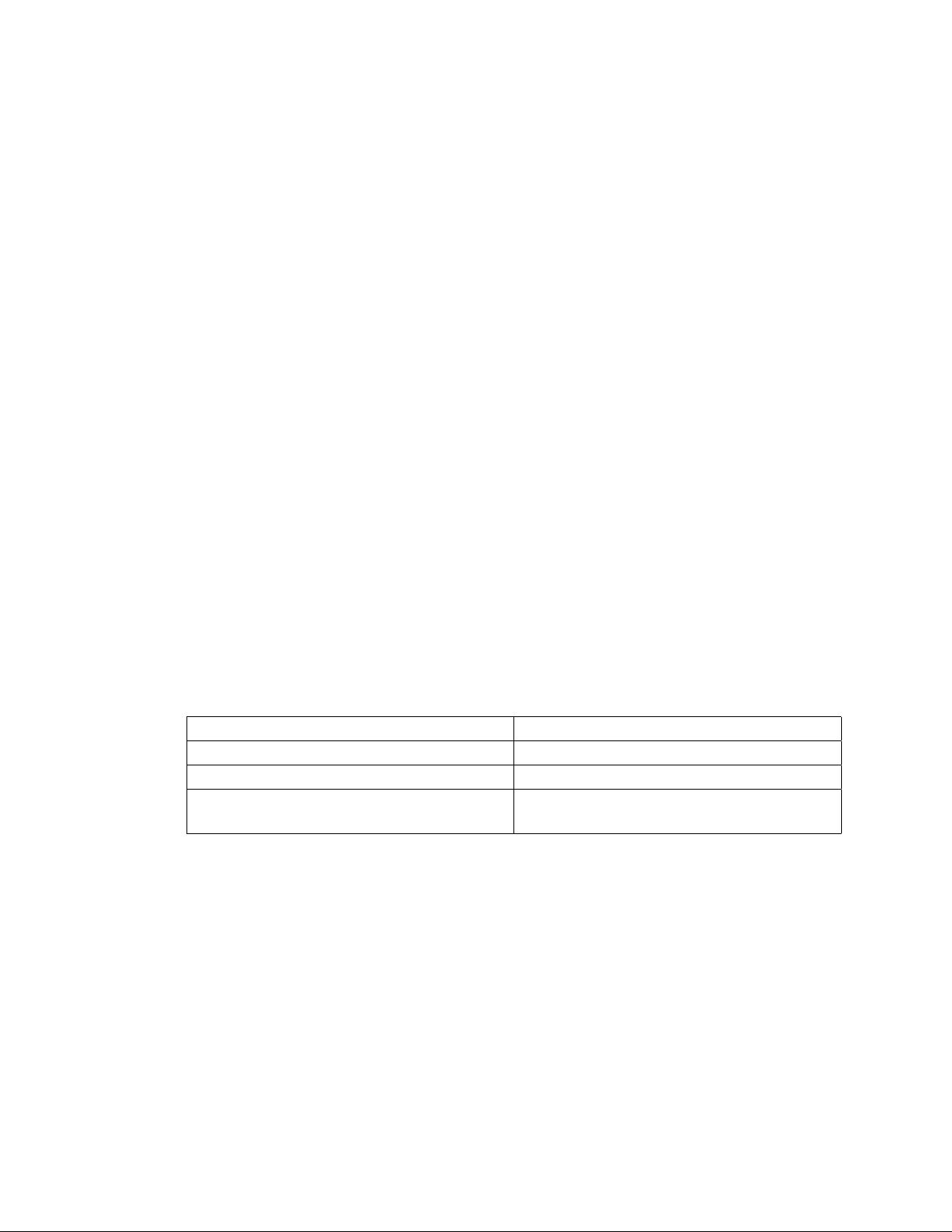
policy configuration is compiled. The Flask configuration files are listed in Table 1.
Table 1. Architecture Configuration Files
Filename Description
security_classes Declares the security classes.
initial_sids Declares initial SIDs.
access_vectors Defines the access vector permissions for each
class.
3. Security Model
The example security server implements a security model that is a combination of a Type Enforcement
(TE) model, a Role-Based Access Control (RBAC) model, and optionally a Multi-Level Security (MLS)
model. The TE model provides fine-grained control over processes and objects in the system, and the
RBAC model provides a higher level of abstraction to simplify user management. The optional MLS
model is not (yet) documented in this report. This section describes the TE and RBAC models, and then
4

Configuring the SELinux Policy
discusses the concept of user identity in SELinux.
3.1. TE Model
A traditional TE model binds a security attribute called a domain to each process, and it binds a security
attribute called a type to each object. The traditional TE model treats all processes in the same domain
identically and it treats all objects that have the same type identically. Hence, domains and types can be
viewed as security equivalence classes. A pair of access matrices specify how domains can access types
and how domains can interact with other domains. Each user is authorized to operate in certain domains.
A TE model supports strong controls over program execution and domain transitions. A program, like
any other object, is assigned a type, and the TE access matrix specifies what types can be executed by
each domain. Furthermore, the TE access matrix specifies what types can be executed to initially enter a
domain. Hence, a domain can be associated with a particular entrypoint program and optionally with
particular helper programs and/or shared libraries. This characteristic of TE is useful in associating
permissions with a particular set of code based on its function and trustworthiness and in protecting
against the execution of malicious code.
The SELinux TE model differs from the traditional TE model in that it uses a single type attribute in the
security context for both processes and objects. A domain is simply a type that can be associated with a
process. A single type can be used both as the domain of a process and as the type of a related object, e.g.
the /proc/PID entries for a process. A single access matrix specifies how types can access or interact with
other types in terms of the permissions defined by the Flask architecture. Although the example TE
configuration often uses the term domain when referring to the type of a process, the SELinux TE model
does not internally distinguish domains from types.
The SELinux TE model also differs from the traditional TE model in that it uses the security class
information provided by the Flask architecture. A SELinux TE transition or access decision is based on a
type pair and on the security class. Hence, the policy can treat objects that have the same type but
different security classes differently. For example, the policy can distinguish a TCP socket created by a
domain from a raw IP socket created by the same domain.
A third difference between the SELinux TE model and the traditional TE model is that the SELinux TE
model does not directly associate users with domains. Instead, SELinux uses the RBAC model to provide
an additional layer of abstraction between users and domains. This approach is discussed further in the
next subsection.
A TE transition rule for a process specifies the new domain based on the current domain of the process
and the type of the program. A TE transition rule for an object specifies the new type based on the
domain of the creating process, the type of the related object, and the object security class. If no
matching rule is found in the TE configuration, then the SELinux TE model provides a default behavior
appropriate for the class of object. For a process, the domain of the process is left unchanged across the
program execution. For an object, the type of the related object (e.g. the parent directory for files) is used
for the new object.
A TE access vector rule specifies an access vector based on the type pair and object security class. Rules
can be specified for each kind of access vector, including the allowed, auditallow, and auditdeny vectors.
These access vector rules define the TE access matrix. If no matching rule is found in the TE
configuration, then the SELinux TE model defines a default behavior for each kind of access vector.
Permissions are denied unless there is an explicit allow rule. No permissions are audited when granted
5
剩余32页未读,继续阅读
资源评论

瑜珈山神
- 粉丝: 52
- 资源: 7
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功