没有合适的资源?快使用搜索试试~ 我知道了~
资源详情
资源评论
资源推荐

Payment Card Industry (PCI)
Data Security Standard
Requirements and Security Assessment Procedures
Version 2.0
October 2010

PCI DSS Requirements and Security Assessment Procedures, Version 2.0 October 2010
Copyright 2010 PCI Security Standards Council LLC Page 2
Document Changes
Date
Version
Description
Pages
October
2008
1.2
To introduce PCI DSS v1.2 as ―PCI DSS Requirements and Security Assessment Procedures,‖ eliminating
redundancy between documents, and make both general and specific changes from PCI DSS Security
Audit Procedures v1.1. For complete information, see PCI Data Security Standard Summary of Changes
from PCI DSS Version 1.1 to 1.2.
July
2009
1.2.1
Add sentence that was incorrectly deleted between PCI DSS v1.1 and v1.2.
5
Correct ―then‖ to ―than‖ in testing procedures 6.3.7.a and 6.3.7.b.
32
Remove grayed-out marking for ―in place‖ and ―not in place‖ columns in testing procedure 6.5.b.
33
For Compensating Controls Worksheet – Completed Example, correct wording at top of page to say ―Use
this worksheet to define compensating controls for any requirement noted as ‗in place‘ via compensating
controls.‖
64
October
2010
2.0
Update and implement changes from v1.2.1. For details, please see ―PCI DSS - Summary of Changes from
PCI DSS Version 1.2.1 to 2.0.‖

PCI DSS Requirements and Security Assessment Procedures, Version 2.0 October 2010
Copyright 2010 PCI Security Standards Council LLC Page 3
Table of Contents
Document Changes ........................................................................................................................................................................... 2
Introduction and PCI Data Security Standard Overview ................................................................................................................. 5
PCI DSS Applicability Information .................................................................................................................................................... 7
Relationship between PCI DSS and PA-DSS .................................................................................................................................... 9
Scope of Assessment for Compliance with PCI DSS Requirements ............................................................................................ 10
Network Segmentation .................................................................................................................................................................. 10
Wireless ........................................................................................................................................................................................ 11
Third Parties/Outsourcing .............................................................................................................................................................. 11
Sampling of Business Facilities/System Components.................................................................................................................... 12
Compensating Controls ................................................................................................................................................................. 13
Instructions and Content for Report on Compliance .................................................................................................................... 14
Report Content and Format ........................................................................................................................................................... 14
Revalidation of Open Items ........................................................................................................................................................... 17
PCI DSS Compliance – Completion Steps .................................................................................................................................... 18
Detailed PCI DSS Requirements and Security Assessment Procedures ..................................................................................... 19
Build and Maintain a Secure Network .......................................................................................................................................... 20
Requirement 1: Install and maintain a firewall configuration to protect cardholder data ............................................................ 20
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters ............................. 24
Protect Cardholder Data ................................................................................................................................................................ 28
Requirement 3: Protect stored cardholder data ......................................................................................................................... 28
Requirement 4: Encrypt transmission of cardholder data across open, public networks ........................................................... 35
Maintain a Vulnerability Management Program ........................................................................................................................... 37
Requirement 5: Use and regularly update anti-virus software or programs ............................................................................... 37
Requirement 6: Develop and maintain secure systems and applications .................................................................................. 38
Implement Strong Access Control Measures .............................................................................................................................. 44
Requirement 7: Restrict access to cardholder data by business need to know ......................................................................... 44
Requirement 8: Assign a unique ID to each person with computer access ............................................................................... 46
Requirement 9: Restrict physical access to cardholder data ..................................................................................................... 51
Regularly Monitor and Test Networks .......................................................................................................................................... 55
Requirement 10: Track and monitor all access to network resources and cardholder data ....................................................... 55

PCI DSS Requirements and Security Assessment Procedures, Version 2.0 October 2010
Copyright 2010 PCI Security Standards Council LLC Page 4
Requirement 11: Regularly test security systems and processes. ............................................................................................ 59
Maintain an Information Security Policy ...................................................................................................................................... 64
Requirement 12: Maintain a policy that addresses information security for all personnel. .............................................................. 64
Appendix A: Additional PCI DSS Requirements for Shared Hosting Providers ................................................................... 70
Appendix B: Compensating Controls ...................................................................................................................................... 72
Appendix C: Compensating Controls Worksheet ................................................................................................................... 73
Compensating Controls Worksheet – Completed Example........................................................................................................ 74
Appendix D: Segmentation and Sampling of Business Facilities/System Components ..................................................... 75
PCI DSS Requirements and Security Assessment Procedures, Version 2.0 October 2010
Copyright 2010 PCI Security Standards Council LLC Page 5
Introduction and PCI Data Security Standard Overview
The Payment Card Industry (PCI) Data Security Standard (DSS) was developed to encourage and enhance cardholder data security and facilitate
the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements
designed to protect cardholder data. PCI DSS applies to all entities involved in payment card processing – including merchants, processors,
acquirers, issuers, and service providers, as well as all other entities that store, process or transmit cardholder data. PCI DSS comprises a
minimum set of requirements for protecting cardholder data, and may be enhanced by additional controls and practices to further mitigate risks.
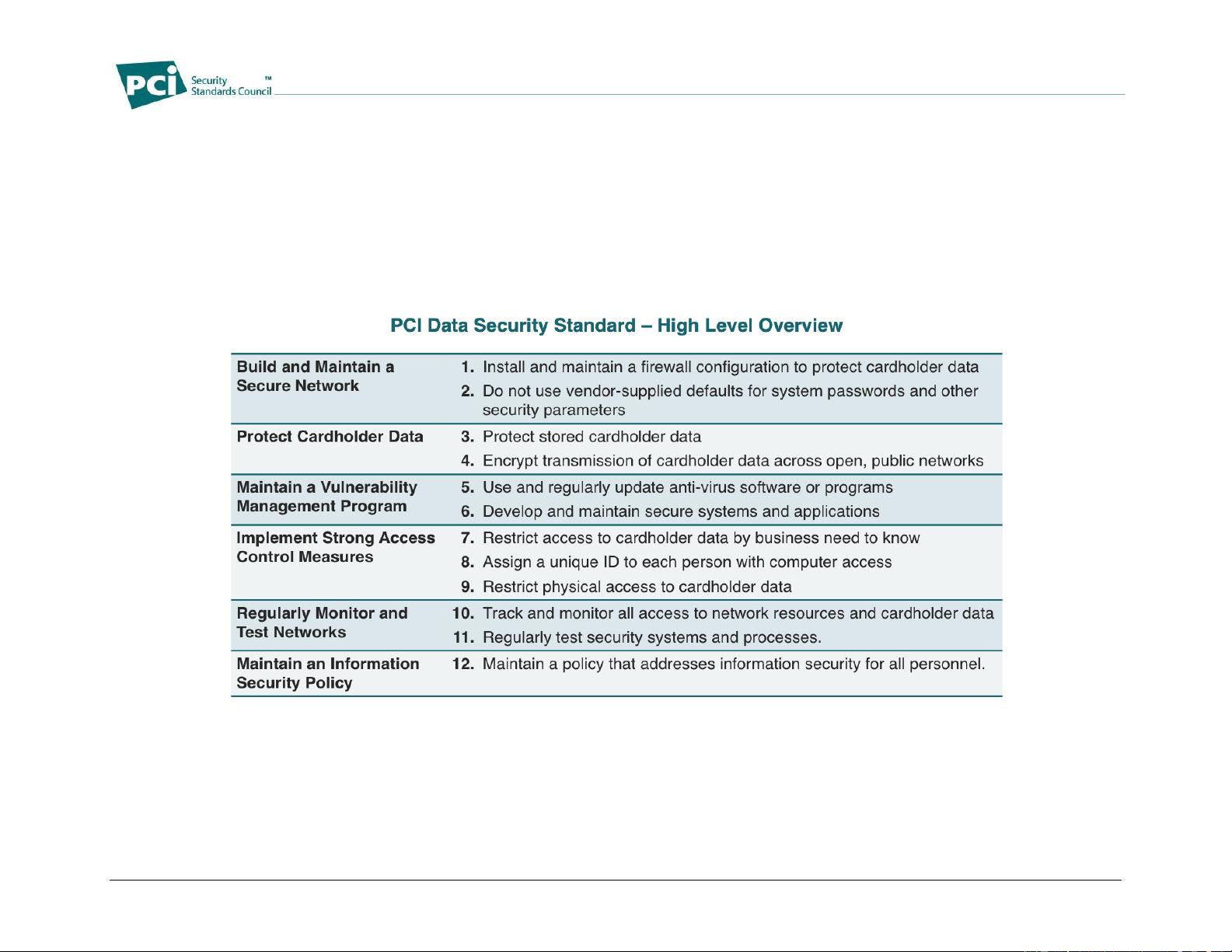
Below is a high-level overview of the 12 PCI DSS requirements.
This document, PCI Data Security Standard Requirements and Security Assessment Procedures, combines the 12 PCI DSS requirements and
corresponding testing procedures into a security assessment tool. It is designed for use during PCI DSS compliance assessments as part of an
entity’s validation process. The following sections provide detailed guidelines and best practices to assist entities prepare for, conduct, and report
the results of a PCI DSS assessment. The PCI DSS Requirements and Testing Procedures begin on page 19.
剩余74页未读,继续阅读
aiachris2k1
- 粉丝: 0
- 资源: 1
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功
评论0