没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
Strong user authentication and device validation are essential for trusted digital interactions. Both are necessary to protect against inappropriate access to sensitive and confidential information and valued systems. Both are required to protect the integrity of the information, prevent corruption of the files, and ensure the integrity of those systems
资源推荐
资源详情
资源评论

Copyright© 2005 Trusted Computing Group—Other names and brands are properties of their respective owners.
1
Trusted Platform Modules Strengthen User and Platform Authenticity
January 2005
Computing and communications products with embedded Trusted Platform Modules (TPMs)
advance the ability of businesses, institutions, government agencies, and consumers to conduct
trustworthy electronic transactions. TPMs are special-purpose integrated circuits (ICs) built into a
variety of platforms to enable strong user authentication and machine attestation—essential to
prevent inappropriate access to confidential and sensitive information and to protect against
compromised networks. Trusted Platform Modules utilize open standards and technologies to
ensure interoperability of diverse products in mixed-vendor environments.
Trustworthy Transactions
Businesses of all sizes, institutions, government agencies, and consumers rely on millions of
digital transactions everyday. The volume and the importance of these transactions are rapidly
increasing. Wired and wireless systems used in digital interactions are woven into the very fabric
of business and everyday life around the world. Being able to trust the identities of the
participants, the authenticity of the contents, and the integrity of the systems involved in digital
events is crucial. Robust security is essential for trusted communications; but it is surprising how
many organizations rely on weak security solutions, believing they are engaged in trustworthy
processes when they are not. It has been estimated that more than half of all desktop, laptop, and
notebook PCs lack today’s available software security features. To address the risks caused by
inadequate security, integrated security hardware in the platform can not only strengthen the
software solutions, but also assure that every platform comes with strong protection built in.
When the integrity of the services isn’t reliable and cannot be proved, the consequence may be
catastrophic. Victims of stolen personal, confidential, or sensitive information lose much more
than data. Unauthorized changes to system parameters generate unintended expenses for
system rebuilding and may jeopardize the future of an enterprise. If that’s not bad enough,
consider that corruption of important records—or even the perception of compromised integrity—
may have severe legal consequences with criminal and civil penalties.
Intruders hack into networks with increasing frequency. Malicious corruption of records and
inadequately protected systems regularly compromise legitimate transactions. Lost and stolen
laptops can be a gold mine of critical information and a free pass to the network. Even cell
phones and PDAs are under attack. Hardware-based, embedded security subsystems based on
TPM chips provide reliable protections against these issues and enable truly cost-effective
implementation and enforcement of strong security policies to ensure trustworthy transactions.
Strong User Authentication and Device Validation
Strong user authentication and device validation are essential for trusted digital interactions. Both
are necessary to protect against inappropriate access to sensitive and confidential information
and valued systems. Both are required to protect the integrity of the information, prevent
corruption of the files, and ensure the integrity of those systems. Ultimately, it comes down to two
basic questions:
Who are you and how do I know this is true?
Copyright© 2005 Trusted Computing Group—Other names and brands are properties of their respective owners.
2
Can I trust this interaction and how do I know this is true?
Who are you and how do I know this is true? All of the parties engaged in an important electronic
transaction need to know that who they claim to be is really true. They could be corporate officers
making 10K filings, doctors exchanging patient records, government clerks providing copies of
birth certificates or deeds, businesses ordering critical parts, or consumers shopping on-line. The
need to demonstrate their own authenticity and verify the reputed authenticity of the other party
has never been more important. Software-only login and sign-on schemes provide only weak
security. TPM-capable systems use both hardware and software to ensure spoof-proof user
authentication to assure that the authenticity of the parties in digital transactions can be trusted.
Can I trust this interaction and how do I know this is true? It is also essential in trusted digital
interactions to know that the systems, software, and records involved are what they claim to be.
What if an on-line banking transaction is corrupted—wrong bank, wrong account, or the decimal
point goes awry? What if confidential records are intercepted or misdirected and don’t get to a
patient’s medical center or the SEC? Or, maybe, it is the right server, but the path leads to the
wrong file or the file was corrupted after it was created? The integrity of the networks and
resources must be ensured and it must be verifiable that they are used as intended.
It must also be assured that important records that were properly created and transmitted are
also stored intact and uncorrupted. They must be retrievable at a later date exactly as they were
created. Corrupted Social Security records, corporate 10K SEC filings, and medical records are
but a few examples whose consequences can be devastating. In the United States, recent
legislation imposes new requirements for safeguarding various types of sensitive data.
TPM-capable systems can play a strong role in assuring compliance with provisions of the Health
Insurance Portability and Accountability Act (HIPAA) of 1996 to protect medical records, as well
as Graham-Leech-Bliley, Sarbanes-Oxley and similar regulations that impose privacy and validity
requirements on corporate communications. Similar laws exist in other countries as well.
TPM-Capable Solutions Reduce Risk and Increase Reliability
Inadequate security has been tolerated because the risks were perceived as low and the
solutions were perceived as cumbersome, expensive, and proprietary. These risks are no longer
low and TPM-capable products provide easy to use, inexpensive solutions based on open
standards. The trade-off between weak security versus unmanageable and proprietary security
solutions is no longer an issue when network administrators can implement robust security
policies based on open standards and protocols and deploy TPM-capable systems and software
from many vendors.
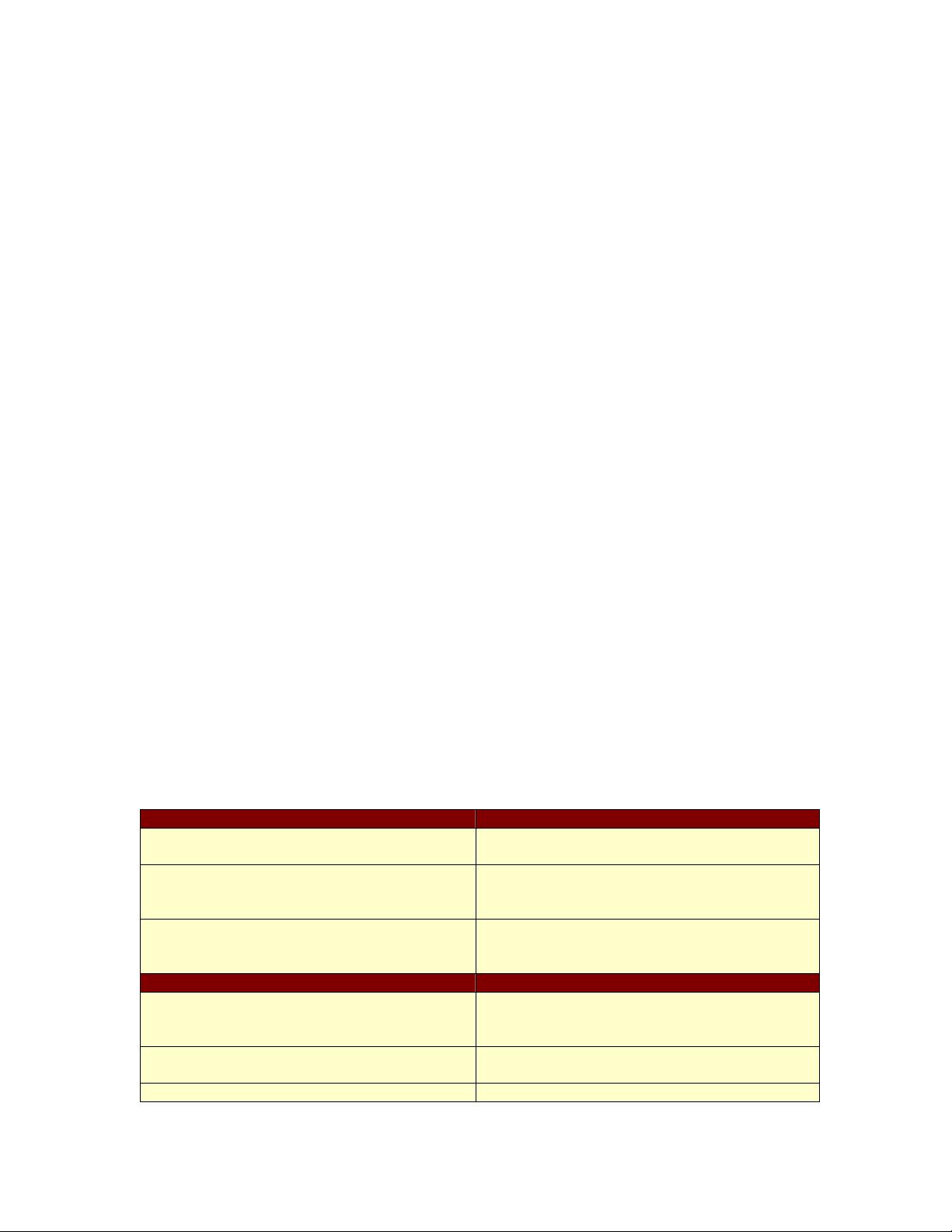
User Authentication without TPM User Authentication with TPM
Inadequate user ID and password
protection makes “spoofing” very easy
Strong protections eliminate “spoofing”;
verifies integrity of user log-in credentials
Multiple log-in IDs and passwords cause
users to be careless; store secrets without
protecting them; use weak protections
On-chip, protected storage of secrets
reduces user burden; enables secure single
sign-on; ensures strong protections
Storage of IDs and passwords in easily
copied files; use of one set of secrets for
access to all systems
Secure storage of IDs and passwords;
multiple log-in secrets secured by the TPM
Platform Attestation without TPM Platform Attestation with TPM
Easy to change settings and parameters
for unauthorized access and malicious
damage
Secure access prevents unauthorized
access; secure hash comparison validates
settings
Altered settings allow inappropriate access
to valued networks and sensitive data
Validated settings ensure system integrity
and prevent inappropriate access
Untrustworthy systems result in unreliable
Trustworthy systems result in reliable and
剩余7页未读,继续阅读
资源评论

ymeish
- 粉丝: 0
- 资源: 19
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- jython包构建burp python环境
- C# 获取公网IP实例源码
- 火焰报警实验通过火焰传感器实现报警功能
- 数字图像处理-基于python 期末考试复习总结
- 烟雾传感器检测实验掌握烟雾传感器的使用方法
- 智思Ai系统2.4.9版本去授权开源版可商用
- C# 简单计时器实例源码
- Matlab实现CPO-HKELM冠豪猪算法优化混合核极限学习机多变量回归预测(含完整的程序,GUI设计和代码详解)
- Matlab实现BO-CNN-LSTM-Mutilhead-Attention贝叶斯优化卷积神经网络-长短期记忆网络融合多头注意力机制多特征分类预测(含完整的程序,GUI设计和代码详解)
- Matlab实现OOA-HKELM鱼鹰算法优化混合核极限学习机多变量回归预测(含完整的程序,GUI设计和代码详解)
- Matlab实现BO-CNN-BiLSTM-Mutilhead-Attention贝叶斯优化卷积神经网络-双向长短期记忆网络融合多头注意力机制多特征分类预测(含完整的程序,GUI设计和代码详解)
- C#控制笔记本摄像头,实现拍照
- MATLAB实现GWO-Elman灰狼优化循环神经网络多输入多输出预测(含完整的程序,GUI设计和代码详解)
- 人生时间流逝器1.0.0
- Matlab实现CPO-BiTCN-BiGRU冠豪猪算法优化双向时间卷积门控循环单元多变量回归预测(含完整的程序,GUI设计和代码详解)
- Matlab实现BO-CNN-GRU-Mutilhead-Attention贝叶斯优化卷积神经网络-门控循环单元融合多头注意力机制多特征分类预测(含完整的程序,GUI设计和代码详解)
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功