International Journal of Computer Science and Electrical Engineering (IJCSEE) ISSN No. 2315-4209, Vol-1 Iss-1, 2012
38
Packet Monitoring Approach to Prevent DDoS
Attack in Cloud Computing
Vikas Chouhan & Sateesh Kumar Peddoju
Electronics & Computer Engineering Department,Indian Institute of Technology Roorkee, Roorkee-247667, India
Abstract - In cloud environment, cloud servers providing requested cloud services, sometimes may crash after receiving huge
amount of requests. This is exactly what happens in a denial of service (DoS) attack. It prevents the authentic clients from getting
service. DoS attack is accompanied by IP Spoofing so as to hide the source of flooding and to make every request look different.
In this paper, we present an approach for packet monitoring in Cloud Environment to prevent DDoS attacks. This new approach of
Hop Count Filtering provides a network independent and readily available solution to prevent DoS attack in Cloud environment.
Also, this method decreases the unavailability of cloud services to legitimate clients, reduces number of updates and saves
computation time. The presented approach is simulated in CloudSim toolkit environment and corresponding results are then
produced.
Keywords - Cloud Computing, TTL, IP, Hop Count, Denial-of-Service.
I. INTRODUCTION
Cloud computing can be defined as a new style of
computing in which dynamically scalable and often
virtualized resources are provided as a services over the
Internet. Advantages of the cloud computing technology
include cost savings, high availability, and easy
scalability [1].
DoS attacks do not wish to modify data or gain
illegal access, but instead they target to crash the servers
and whole networks, disrupting legitimate users’
communication. DoS attacks can be launched from
either a single source or multiple sources. Multiple-
source DoS attacks are called distributed denial-of-
service (DDoS) attacks [2].
When the operating system notices the high
workload on the flooded service, it will start to provide
more computational power to cope with the additional
workload. The attacker can flood a single, system based
address in order to perform a full loss of availability on
the intended service [3, 4].
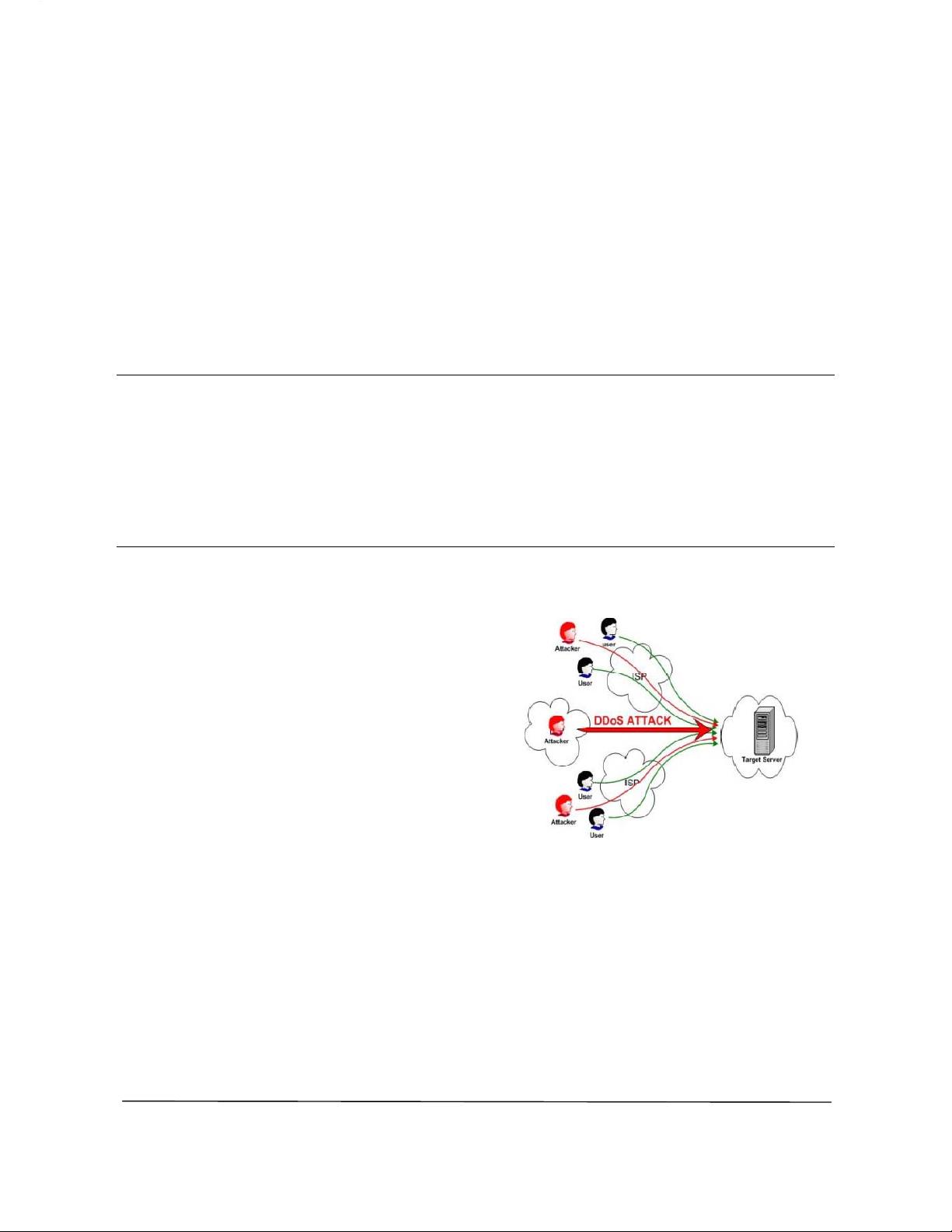
These attacks are a type of Flooding Attack [2, 5],
which basically consist of an attacker sending a large
number of nonsense requests to a certain service, which
is providing various services under cloud. As each of
these requests has to be handled by the service
implementation in order to determine its invalidity, this
causes a certain amount of workload per attack request,
which in the case of a flood of requests usually would
cause a Denial of Service to the server hardware [2].
Fig. 1 : DDoS attack [2]
II. HOP-COUNT
COMPUTATION
Since hop-count information is not directly stored
in the IP header, one has to compute it based on the
Time-to-live (TTL) field. TTL is an 8-bit field in the IP
header, originally introduced to specify the maximum
lifetime of each packet in the Internet. Each intermediate
router decrements the TTL value of an in-transit IP
packet by one before forwarding it to the next-hop
[6, 7].


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜 信息提交成功
信息提交成功

