
Abstract—Encryption is used to securely transmit data in
open networks. Each type of data has its own features, therefore
different techniques should be used to protect confidential
image data from unauthorized access. Most of the available
encryption algorithms are mainly used for textual data and may
not be suitable for multimedia data such as images. In this
paper, we introduce a block-based transformation algorithm
based on the combination of image transformation and a well
known encryption and decryption algorithm called Blowfish.
The original image was divided into blocks, which were
rearranged into a transformed image using a transformation
algorithm presented here, and then the transformed image was
encrypted using the Blowfish algorithm. The results showed
that the correlation between image elements was significantly
decreased by using the proposed technique. The results also
show that increasing the number of blocks by using smaller
block sizes resulted in a lower correlation and higher entropy.
Index Terms—Image correlation, Image encryption, Image
entropy, Permutation.
I. INTRODUCTION
The rapid growth of computer networks allowed large files,
such as digital images, to be easily transmitted over the
internet [1]. Data encryption is widely used to ensure security
however, most of the available encryption algorithms are
used for text data. Due to large data size and real time
constrains, algorithms that are good for textual data may not
be suitable for multimedia data [2]-[4].
In most of the natural images, the values of the
neighboring pixels are strongly correlated (i.e. the value of
any given pixel can be reasonably predicted from the values
of its neighbors) [5]-[7]. In order to dissipate the high
correlation among pixels and increase the entropy value, we
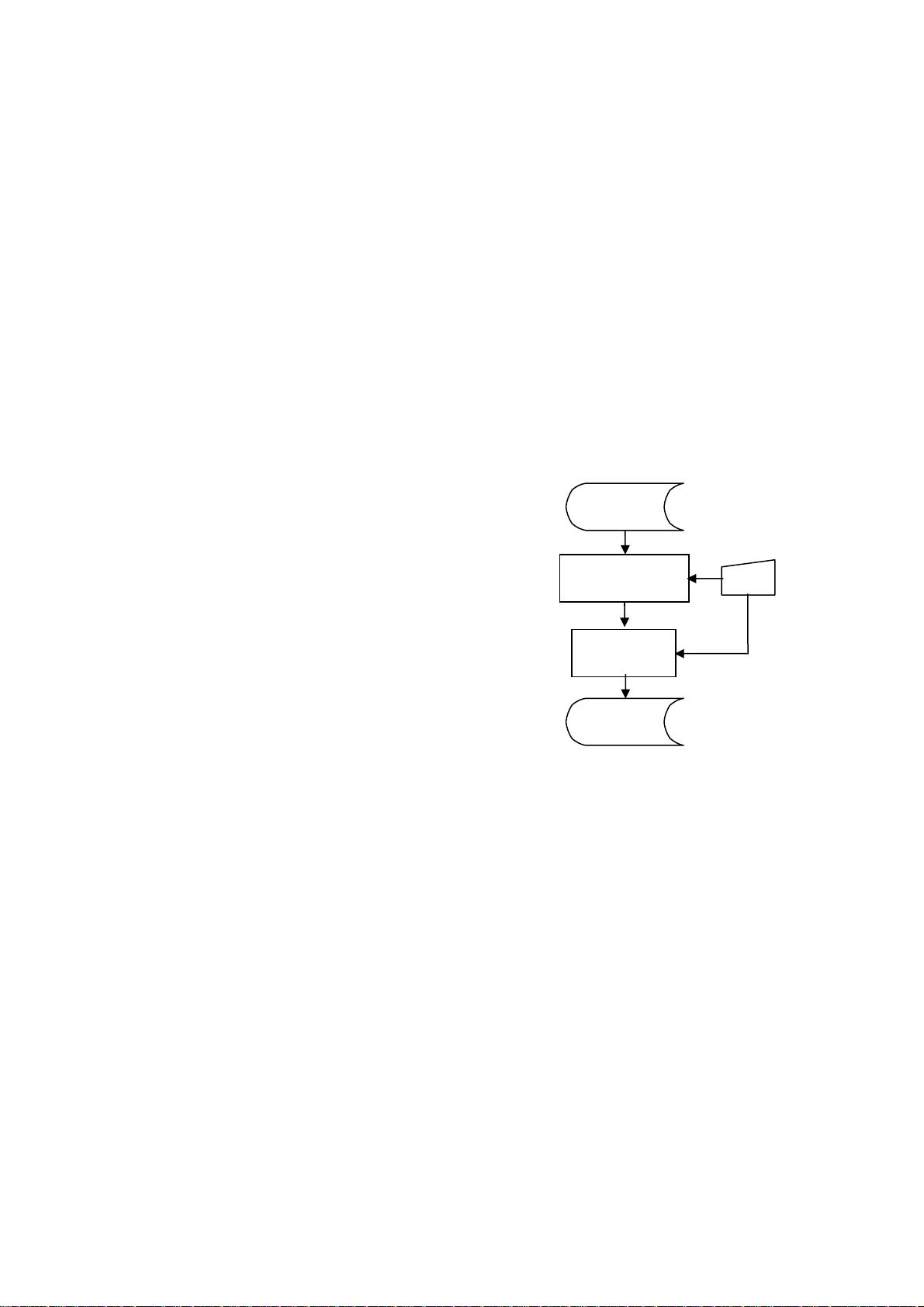
propose a transformation algorithm that divides the image
into blocks and then shuffles their positions before it passes
them to the Blowfish encryption algorithm. By using the
correlation and entropy as a measure of security, this process
results in a lower correlation and a higher entropy value when
compared to using the Blowfish algorithm alone, and thus
improving the security level of the encrypted images. There
are two main keys to increase the entropy; the variable secret
key of the transformation process and the variable secret key
of the Blowfish algorithm.
Manuscript received 25 Jul 2007. Mohammad Ali Moh'd Bani Younes
and Aman Jantan are with the Department of Computer Science, Universiti
Sains Malaysia, and E-mail: mali.cod04@student.usm.my,
aman@cs.usm.my.
The variable secret key of the transformation process
determines the seed, which is used to build the secret
transformation table with a variable number of blocks. If the
key is changed, another seed will be generated, and then a
different secret transformation table is obtained.
The variable secret key of the Blowfish algorithm is used
to encrypt the transformed image. This encryption process
decreases the mutual information among the encrypted image
variables (i.e. high contrast) and thus increasing the entropy
value. In this paper we propose a block-based transformation
algorithm in order to increase the security level of the
encrypted images. The rest of this paper is organized as
follows. Section II gives a background about the current
image encryption schemes. In Section III, the description of
the proposed block-based transformation algorithm is
presented. Section IV and V present the experimental results
and discussion, while section VI presents a comparison
between the proposed algorithm and those of other systems.
Finally, section VII concludes the paper.
II. BACKGROUND
Encryption is the process of transforming the information
to insure its security. With the huge growth of computer
networks and the latest advances in digital technologies, a
huge amount of digital data is being exchanged over various
types of networks. It is often true that a large part of this
information is either confidential or private. As a result,
different security techniques have been used to provide the
required protection [8].
The security of digital images has become more and more
important due to the rapid evolution of the Internet in the
digital world today. The security of digital images has
attracted more attention recently, and many different image
encryption methods have been proposed to enhance the
security of these images [9].
Image encryption techniques try to convert an image to
another one that is hard to understand [9]. On the other hand,
image decryption retrieves the original image from the
encrypted one. There are various image encryption systems
to encrypt and decrypt data, and there is no single encryption
algorithm satisfies the different image types.
Most of the algorithms specifically designed to encrypt
digital images are proposed in the mid-1990s. There are two
major groups of image encryption algorithms: (a) non-chaos
selective methods and (b) Chaos-based selective or
non-selective methods. Most of these algorithms are
Image Encryption Using Block-Based
Transformation Algorithm
Mohammad Ali Bani Younes and Aman Jantan
IAENG International Journal of Computer Science, 35:1, IJCS_35_1_03
______________________________________________________________________________________
(Advance online publication: 19 February 2008)


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功