没有合适的资源?快使用搜索试试~ 我知道了~
社交网络安全攻击的模式。All of this has created the perfect storm for attackers. They now have a platform that if they can compromise, it will provide access to millions of victims. It also allows them to hide their tracks within legitimate traffic streams. Oh yeah, we can’t forget that it becomes more difficult to shut down a social network than it does a single user. So, we have to rely on the social networks to protect themselves from attacks, thus protecting us.
资源推荐
资源详情
资源评论

CHAPTER
1
1
INFORMATION IN THIS CHAPTER
• BringingtheSocialNetworkstoTheirKnees
• SavingtheSocialNetworksandOurselves
Social Networking
Infrastructure Attacks
Social networks today host millions of users. The services offered by social networks
vary from basic communications to applications that can help you on a daily basis.
Keep in mind that the traffic on these sites is considered legitimate traffic.
All of this has created the perfect storm for attackers. They now have a platform
that if they can compromise, it will provide access to millions of victims. It also
allows them to hide their tracks within legitimate traffic streams. Oh yeah, we can’t
forget that it becomes more difficult to shut down a social network than it does a
single user. So, we have to rely on the social networks to protect themselves from
attacks, thus protecting us.
BRINGING THE SOCIAL NETWORKS TO THEIR KNEES
It was just a normal day in August 2009. You got up for work, drank your coffee or
whatever your caffeine fix is, took Rover for a walk, and got ready for work, nothing
out of the ordinary. The same type of morning you’ve had for the past 15 years. Then,
you decided, “Let’s check my Twitter account.” You go to the Web site to log in, and
you are presented with a page like Figure 1.1.
“Twitter is down!!!!!!!!!” you scream. You think, “How can this happen? Is it the
end of the world?” The truth is that it isn’t the end of the world, and actually all that
has happened is Twitter, Facebook, and a handful of other social networking sites all
fell victim to a cyber attack.
People have grown to rely on social networks for everyday life. They are not only
checking and posting to these accounts from their home PCs but also posting from
their work PCs and their cell phones. However, it is not only people are relying on
these networks but corporations have taken an interest as well. Corporations are now

CHAPTER 1 Social Networking Infrastructure Attacks2
using these social networks for marketing, recruiting, and sales. Oh yeah, let’s not
forget that some companies are now using social networks such as Twitter to send
mass distribution messages such as declaring an emergency.
In other words, when a social network is brought down or compromised, people
and companies are going to be affected and potentially lose money. What better of a
situation is there for an attacker wanting to wreak havoc?
What Happened to the Social Networks?
So, what caused some of the social networks to be brought down? During the early
morning hours of August 6, 2009, Twitter, Facebook, LiveJournal, Google’s Blogger,
and YouTube were attacked by a distributed denial-of-service (DDoS) attack. Twitter
encountered interrupted service for approximately 3 h, while Facebook users noticed
longer periods of time in loading Web pages.
Twitter experienced an entire outage during the time period. Users from across
the world complained about not being able to send their Tweets. With over 44 million
registered users, having any amount of downtime would cause serious problems.
Companies that experience network outages realize severe financial losses. These
losses are due to lost revenue from purchases, advertising, and productivity to name
a few. In the case of Twitter, it wasn’t the only company that lost revenue due to lack
of productivity.
FIGURE 1.1
Twitter Is Down!!!!

Bringing the Social Networks to Their Knees
3
Twitter has become a part of the world’s communication network; in other words,
everyone is Tweeting. AT&T uses Twitter to communicate network outages for
Internet service providers (ISPs). The Center for Disease Control (CDC) has inte-
grated Twitter as a means for managing alerts. The US State Department even asked
Twitter to reschedule their maintenance window during the protests over the disputed
election in Iran. Numerous other companies and people use Twitter as their primary
source of news updates. So, bringing down Twitter would have an effect on the pro-
ductivity of these companies as well.
Here is the twist to this story; the DDoS attack was launched against Twitter,
Facebook, LiveJournal, Google’s Blogger, and YouTube to silence a single user.
That’s right; they didn’t care about affecting everyone; they were just concerned with
a single user. The attack was both a personal and political attack against a Georgian
blogger that had accounts on all of these sites.
Come to find out, the account Cyxymu was owned by a Georgian Economics
professor. It is speculated that the attack occurred in response to the professor’s con-
tinued criticism of Russia’s conduct in the year-long war with Georgia.
A
Who would have ever thought that one person voicing his or her opinion could cause
an attack on an entire site? This just goes to show the power social networks have.
This seems like a good time for us to take a look at DDoS attacks and the auton-
omy behind them.
Distributed Denial-of-Service Attacks
All of this talk of DDoS – what the heck is it? Before understanding DDoS, one
must first understand the denial-of-service (DoS) attack. Looks like it may be time
to take a trek down the technical jargon path. A DoS attack is defined as an attack
coming from one Internet Protocol (IP) address to monopolize a computer resource,
so intended users are unable to utilize the resources. DoS attacks typically attempt to
do one of the following:
• Consumption of computational resources, such as bandwidth, disk space, or
processor time
• Disruptionofcongurationinformation,suchasroutinginformation
• Disruption of state information, such as unsolicited resetting of Transmission
Control Protocol (TCP) sessions
• Disruptionofphysicalnetworkcomponents
• Obstructingthecommunicationmediabetweentheintendedusersandthevictim,
so they can no longer communicate adequately
A DDoS is nothing more than a more powerful version of a DoS. Instead of
the attack originating from a single source, multiple sources are used to simulta-
neously launch the attack. Launching this type of attack bombards the target with
requests, thus overloading the resource. Also, by launching from multiple locations,
it becomes more difficult to track down the attacker.
A
www.pcworld.com/article/169809
CHAPTER 1 Social Networking Infrastructure Attacks4
If you haven’t dealt with these types of attacks, you may be a little confused at
this point. So, we will take a look at an analogy of the two types of attacks.
Let’s go old school and talk about prank calls. In these two examples, we will
use a kid who is mad at his or her teacher. For our analogy, we will call the kid
“Johnny”:
Analogy 1
Johnny is mad at his teacher for giving him detention. So, when Johnny gets home,
he starts calling his teacher. When he or she answers, Johnny just hangs up and
immediately calls back. By continuing to do this, Johnny ties up the teacher’s phone
line. Getting tired of answering the call, the teacher just implements call block, and
the attack is over.
Analogy 2
Johnny is extremely mad at his teacher this time. He or she had the nerve to give
him detention for a week. So, Johnny decides it is time to get even. Instead of
him calling the teacher this time, he decides to go cyber. Johnny crafts an e-mail
claiming that the recipient has received a trip. However, in order to receive the trip,
they must call this number, the teacher’s number, between 3:00 and 4:00 p.m. on
Tuesday. Johnny then blasts the e-mail out as spam. During Johnny’s specified time,
the teacher starts receiving thousands of calls from different numbers. Call block
will not help this time.
In the first analogy, the teacher experienced a DoS attack. It was from a single
source, and it wasn’t hard to figure out where it was coming from. However, in the
second analogy, the teacher experienced a DDoS attack. The attack originated from
multiple sources, which makes it harder to determine where the attack is coming
from and also harder to protect against.
Johnny is a bad boy!! These were the simplest of attacks. DDoS attacks have
been used to bring down the communications of large companies. This seems like
the perfect time to dive deeper into these attacks and take a look at the autonomy of
a DDoS attack.
Autonomy of a DDoS Attack
DDoS attacks are scary attacks. They are easy to perform and difficult to determine
who launched the attack. Basically, anyone with a computer and a little know-how
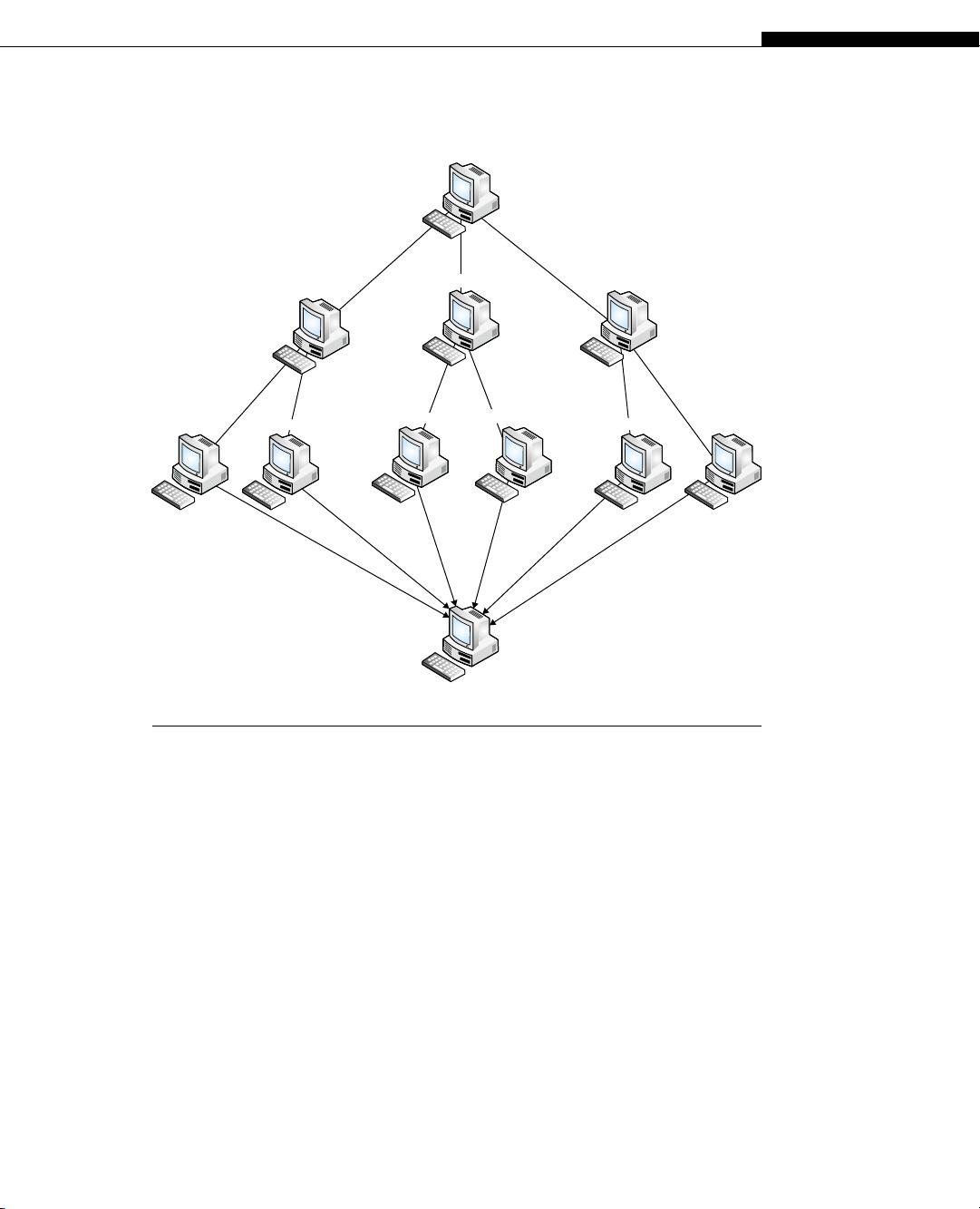
could launch a DDoS attack. Figure 1.2 illustrates a basic DDoS attack.
NOTE
Youhaveprobablyheardpeopletalkaboutreceivingspam.Whenyourstheardthatyou
mayhavethought,“Spamiscannedmeat,right?”Spamisaprocessedmeat;however,that
isnotwhatwearetalkingabout.Wearetalkingaboutelectronicspam.Spamistheabuse
ofelectronicmessagingsystemstosendunsolicitedbulkmessagesindiscriminately.
Bringing the Social Networks to Their Knees
5
We will take a trip back in time and look at how DDoS attacks originally
operated. Original DDoS attacks would occur by a person determining he or she
didn’t like a company or a person. This was the target selection process.
Next, the attacker would need to determine the type of DDoS attack he or she
wanted to launch. Table 1.1 below lists some of the more common DDoS attack
types.
Once the attackers have determined the attack type, they will need to recruit
accomplices to assist them with the attack. Below are some common methods of
recruiting accomplices:
• Callpeople
• E-mailpeople
• Posttousergroups
• CreateaWebpage
FIGURE 1.2
Basic Structure of DDoS
Attacker
Attacker
Attacker
Attacker
Attacker
AttackerAttacker
Attacker
Victim
Attacker
Attacker
剩余129页未读,继续阅读
资源评论

0大白0
- 粉丝: 3
- 资源: 3
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功