没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论

Citation: Richter, M.; Bertram, M.;
Seidensticker, J.; Tschache, A. A
Mathematical Perspective on
Post-Quantum Cryptography.
Mathematics 2022, 10, 2579. https://
doi.org/10.3390/math10152579
Academic Editor: Angel
Martín-del-Rey
Received: 27 June 2022
Accepted: 21 July 2022
Published: 25 July 2022
Publisher’s Note: MDPI stays neutral
with regard to jurisdictional claims in
published maps and institutional affil-
iations.
Copyright: © 2022 by the authors.
Licensee MDPI, Basel, Switzerland.
This article is an open access article
distributed under the terms and
conditions of the Creative Commons
Attribution (CC BY) license (https://
creativecommons.org/licenses/by/
4.0/).
mathematics
Article
A Mathematical Perspective on Post-Quantum Cryptography
Maximilian Richter
1,
* , Magdalena Bertram
1
, Jasper Seidensticker
1
and Alexander Tschache
2
1
Secure Systems Engineering, Fraunhofer AISEC, 14199 Berlin, Germany;
magdalena.bertram@aisec.fraunhofer.de (M.B.); jasper.seidensticker@aisec.fraunhofer.de (J.S.)
2
Volkswagen AG, 38440 Wolfsburg, Germany; alexander.tschache@volkswagen.de
* Correspondence: maximilian.richter@aisec.fraunhofer.de
Abstract:
In 2016, the National Institute of Standards and Technology (NIST) announced an open
competition with the goal of finding and standardizing suitable algorithms for quantum-resistant
cryptography. This study presents a detailed, mathematically oriented overview of the round-three
finalists of NIST’s post-quantum cryptography standardization consisting of the lattice-based key
encapsulation mechanisms (KEMs) CRYSTALS-Kyber, NTRU and SABER; the code-based KEM
Classic McEliece; the lattice-based signature schemes CRYSTALS-Dilithium and FALCON; and the
multivariate-based signature scheme Rainbow. The above-cited algorithm descriptions are precise
technical specifications intended for cryptographic experts. Nevertheless, the documents are not
well-suited for a general interested mathematical audience. Therefore, the main focus is put on the
algorithms’ corresponding algebraic foundations, in particular LWE problems, NTRU lattices, linear
codes and multivariate equation systems with the aim of fostering a broader understanding of the
mathematical concepts behind post-quantum cryptography.
Keywords:
post-quantum cryptography; lattices; learning with errors; linear codes; multivariate
cryptography; Kyber; Saber; Dilithium; NTRU; Falcon; Classic McEliece; Rainbow; NIST
MSC: 11T71
1. Introduction
In recent years, significant progress in researching and building quantum computers
has been made. The existence of such computers threatens the security of many modern
cryptographic systems. This affects, in particular, asymmetric cryptography, i.e., KEMs
and digital signatures. By leveraging Shor’s quantum algorithm to find the period of a
function in a large group, a quantum computer can solve a distinct set of mathematical
problems. In particular, this includes integer factorization and the discrete logarithm, which
are the basis for a wide range of cryptographic schemes. Therefore, a fully fledged quantum
computer would be able to efficiently break the security of many modern cryptosystems.
To defend against this threat, the need for novel mathematical problems which are resistant
to Shor’s algorithm arises. Such problems are thereby promising candidates to withstand
the superior computing possibilities of quantum computers.
In 2016, NIST announced an open competition with the goal of finding and standard-
izing suitable algorithms for quantum-resistant cryptography. The standardization effort
by NIST is aimed at KEMs and digital signatures [
1
]. This process is currently in its third
round of candidate selection (April 2022).
At this point, the submitted algorithms are complex technical specifications without a
presentation of the underlying mathematical fundamentals and therefore do not allow an
easy access to these novel post-quantum algorithm approaches. As some of these algorithms
will probably become widely used in industrial areas very soon, it is vital to foster a broad
understanding of these mathematical concepts. In this document, we therefore address
the described lack of educational presentation. As we do not intend to give a detailed
Mathematics 2022, 10, 2579. https://doi.org/10.3390/math10152579 https://www.mdpi.com/journal/mathematics

Mathematics 2022, 10, 2579 2 of 33
comparison of the presented methods and their performance in practice, we would like to
refer to the post-quantum database PQDB [
2
]. This website is an internal project within
Fraunhofer AISEC and aims to provide an up-to-date overview of implementation details
and performance measurements of post-quantum secure cryptographic schemes according
to available research.
In the following sections, the round-three finalists of NIST’s competition are presented,
and their mathematical details and properties are outlined. For a quick access to any of
these algorithms, we have structured the document in separate parts containing distinct
mathematical concepts, which thereby offer independent readability. These concepts
correspond to the algorithms’ respective algebraic foundations, which are LWE problems
as well as NTRU lattices in Section 2, linear codes in Section 3 and multivariate equation
systems in Section 4.
2. Lattice-Based Cryptography
2.1. Lattice Fundamentals
The cryptographic interest in lattices mainly arises from the fact that a given lattice
L
can have widely different bases. While a good basis can simplify some computational
tasks significantly, a bad basis can make them almost impossible. In this section, we will
give a short introduction to the fundamental mathematics and the two most important
computational problems of lattices.
2.1.1. Lattices
Definition 1
(lattice, basis)
.
Let
B = {b
1
,
b
2
, ...,
b
m
}
be a set of linearly independent vectors of
R
n
. Then, the set of all integer linear combinations
L(B) =
(
∑
i
a
i
b
i
| a
i
∈ Z
)
⊂ R
n
is called a
lattice
in
R
n
generated by
B
. We furthermore refer to
{b
1
,
b
2
, ...,
b
m
}
as a
basis
of the
lattice L.
An example of a lattice with corresponding basis is shown in Figure 1. We can
equivalently generate L via a matrix B containing the basis vectors as column vectors.
Figure 1. A 2-dimensional lattice.
Definition 2
(lattice, rank, dimension, full-rank lattice)
.
Let
{b
1
,
b
2
, ...,
b
m
}
be a set of linearly
independent vectors of R
n
. Let B be the n × m matrix with column vectors b
1
, ..., b
m
. Then:
L(B) = {Bx | x ∈ Z
m
}
is called
lattice
in
R
n
generated by
B
. We call
m
the
rank
and
n
the
dimension
of the lattice.
For m equals n, the lattice is called the full-rank lattice.
Mathematics 2022, 10, 2579 3 of 33
Observe that the basis underlying a lattice
L
is not unique. Observe that the lattice
generated by the vectors
0
1
,
1
0
is Z
2
, the set of all integer points. Z
2
is also generated by the vectors
2
1
,
1
1
.
Figure 2 also illustrates this fact. On the other hand,
n
linearly independent vectors in
Z
n
are not necessarily a basis of
Z
n
. As an example, observe that the modified vectors from
the example above
2
0
,
1
1
do not form a basis of Z
2
.
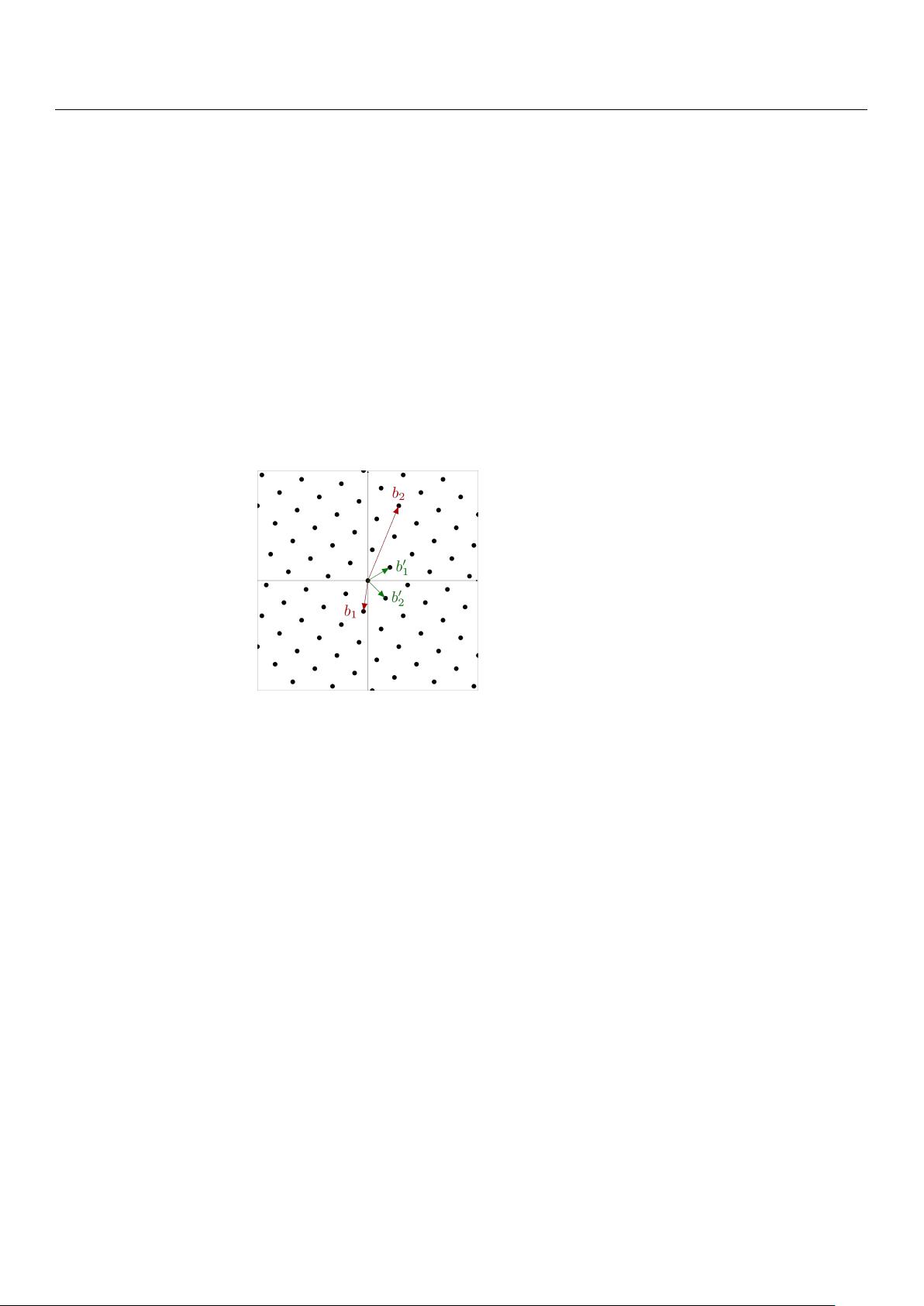
Figure 2. Two-dimensional lattice with a reduced (good) basis {b
0
1
, b
0
2
} and a bad basis {b
1
, b
2
}.
2.1.2. Computational Lattice Problems
The particular structure of lattices allows them to have special mathematical properties.
The following computations can be efficiently evaluated using linear algebra algorithms:
•
Let
g
1
, ...,
g
k
∈ R
n
be a set of vectors generating the lattice
L
. Calculate a basis
b
1
, ..., b
m
∈ R
n
of L.
• Let L be a lattice. Evaluate whether a given vector c is an element of L.
Other computational lattice problems appear to be generally hard and are - as indicated
in the introduction - even believed to be resistant against Shor’s algorithm. Therefore, they
are interesting candidates for usage in post-quantum-cryptography. These problems are
presented in the following.
Shortest Vector Problem
Let
L
be a lattice with some basis
B ∈ R
n×m
and
k · k
some norm. Let
λ(L)
be the
length of the shortest nonzero vector in
L
. The task of finding
l ∈ L
such that
klk = λ(L)
,
i.e., finding any shortest vector of
L
, is called the
shortest vector problem (SVP)
. Figure 3
illustrates such a shortest vector in a lattice.

Mathematics 2022, 10, 2579 4 of 33
Figure 3. Two-dimensional lattice with basis {b
1
, b
2
} and shortest vector `.
2.1.3. Closest Vector Problem
Let
L
be a lattice with some basis
B ∈ R
n×m
and
k · k
some norm. Given
q ∈ R
n
,
the task of finding
l ∈ L
such that
kl − qk
is minimal, i.e., find the lattice vector
l
closest to
a given arbitrary vector, is called the
closest vector problem (CVP)
. Figure 4 illustrates a
random point with its corresponding closest lattice vector.
Figure 4. Two-dimensional lattice with ` as closest vector to point q.
2.2. Cryptography Based on Learning with Errors (LWE)
2.2.1. LWE Fundamentals
Learning with Errors
Let
Z
q
= Z/qZ
be the ring of integers modulo
q
. We can naturally form a linear
equation system
A · s = b ,
where A ∈ Z
n×m
q
, s ∈ Z
m
q
, b ∈ Z
n
q
. For example, consider the following system:
A =
10 3 5 1
4 1 1 2
.
.
.
.
.
.
.
.
.
.
.
.
3 1 1 5
, b =
10
3
.
.
.
8

Mathematics 2022, 10, 2579 5 of 33
Then, the associated equations look like:
10 · s
1
+ 3 · s
2
+ 5 · s
3
+ 1 · s
4
= 10
4 · s
1
+ 1 · s
2
+ 1 · s
3
+ 2 · s
4
= 3
.
.
.
3 · s
1
+ 1 · s
2
+ 1 · s
3
+ 5 · s
4
= 8
Solving this equation system can be efficiently realized using the Gaussian algorithm.
However, adding even only small error values e ∈ Z
n
q
to the equation system yields:
A · s + e = b ,
which renders solving the equation system and retrieving the solution vector
s
surprisingly
hard. This fact is founded in the relation to the hard lattice problems described above,
which is presented in a nutshell below.
Decisional LWE
The LWE problem can also be rephrased as a decision problem, usually abbreviated
dLWE. Given an LWE sample
(A
,
b)
as defined above (
s
and
e
are kept secret), the task
is to guess whether the values of
b
have been calculated as
A · s + e
with small error
values
e
, or whether they have been chosen arbitrarily. Both variants are equivalently hard.
The reduction from LWE to dLWE has been proven by Regev ([
3
], Lemma 4.2), the inverse
reduction from dLWE to LWE is trivial.
Linking LWE to Computational Lattice Problems
Consider an LWE problem of the form:
A · s + e = b ,
where
A ∈ Z
n×m
q
,
b ∈ Z
n
q
and small vectors
s ∈ Z
m
q
,
e ∈ Z
n
q
. It is straightforward to solve
a concrete LWE instance by solving the closest vector problem. Observe that the closest
vector to b is almost always the lattice vector A · s with distance e.
To give an intuition of the relationship between learning with errors and the shortest
vector problem, consider the following lattice:
L = {x ∈ Z
m+n+1
| (A || I
n
|| (−b)) · x = 0 mod q} ,
where the ’
||
’ operator denotes concatenation and
I
n
denotes the
n × n
identity matrix. It
can be observed that the column vector (s, e, 1) is an element of L by verifying that
A I
n
−b
·
s
e
1
= A · s + e − b = b − b = 0 mod q
holds. It can be shown that the vector
(s
,
e
, 1
)
is actually a shortest vector in
L
and therefore
is an SVP solution for
L
. This means retrieving the vector
(s
,
e
, 1
)
directly yields the secret
s
as well as the error vector e and therefore solves the LWE system.
LWE-Based Encryption Schemes
This section aims to serve as a high-level introduction to LWE-based encryption
schemes, so that their basic idea can be easily understood. The following simplified
example will only be used to transmit a message consisting of a single bit, but it can be
trivially extended to transmit a bitstring of any desired length.
Consider an LWE instance
A · s + e = b
, where
A ∈ Z
n×m
q
is chosen uniformly random
and
s ∈ Z
m
q
and
e ∈ Z
n
q
are chosen from an error distribution, i.e., their values are rather
剩余32页未读,继续阅读
资源评论

nfgo
- 粉丝: 766
- 资源: 80
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 高校毕业论文管理系统小程序--论文-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.zip
- 儿童预防接种预约微信小程序+springboot-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- MATLAB 5G上行物理层链路级仿真平台程序 您看到的介绍及图片即为本程序实现的功能,程序经过我自己电脑的测试,确保能实现相应的功能 有详细的说明文档,能帮助您迅速上手 支持调制方式:QPSK、
- 电影院订票选座小程序+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于springboot汽车维修管理系统微信小程序springboot-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 电影院订票选座系统设计及实现+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于vue的青少年科普教学系统平台springboot-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于java的餐厅点餐系统微信小程序ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 房屋租赁管理系统的设计与实现+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于微信平台的报刊订阅小程序的设计与实现ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 个人健康数据管理系统的设计与实现+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于微信的垃圾分类小程序springboot-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 高校体育场管理系统+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- 基于大学生社团活动管理的微信小程序的设计与实现ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
- (1)混合储能,,储能并网,混合储能能量管理,可模型问题,蓄电池与超级电容混合储能并网matlab simulink仿真模型 混合储能采用低通滤波器进行功率分配,可有效抑制系统功率波动,实现母线电压
- 会议发布与预约系统的设计与开发+ssm-微信小程序毕业项目,适合计算机毕-设、实训项目、大作业学习.rar
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功