Here, transient signal detection model is generalised and solved for
the problem of burst signal detection.
In wireless telecommunication networks, burst transmission is
usually employed in two different scenarios: first when a
contention-based channel access is used in the network (e.g. in
IEEE 802.11 [29]) and second when a time division multiple
access (TDMA) scheme is implemented (e.g. in GSM standard
[30]). Many researches have been done on design of a receiver for
TDMA signals in a cooperative environment. For example, the
structure of receiver in satellite telecommunications is investigated
in [31]; frame and burst acquisition in TDMA satellite
communication networks via unique word pattern is considered in
[32]; data detection for burst mode signal via polynomial
interpolation is proposed in [33]. In [34], energy ratio detector
(ERD) is employed for recognition of bursts. However, like all the
other methods, it is assumed that the structure of the received
signal is known to the receiver.
We define burst detection as a problem in which the aim is to
find the start and the end of all bursts (i.e. data packets) in an
eavesdropped signal. In other words, burst detection can be seen as
a generalised transient detection problem where there is more than
one transient in the received signal. Besides, the lengths of
transients are assumed to be unknown. Despite the importance of
this problem, to the best of authors' knowledge, no solid published
research is available for blind burst detection in non-cooperative
environments. In burst detection context, there are only some
rudimentary published researches. For example, in [35],
fluctuations of autocorrelation function are used to detect burst
signals. The idea is that the autocorrelation function has higher
values when the received signal includes burst compared to when
only noise is present. However, neither Monte–Carlo simulations
nor any performance criterion are presented.
Here, autocorrelation detector (ACD), ED, ERD, and maximum
to minimum eigenvalue detector (MMED) are modified and
generalised for solving the problem of burst detection. The
performance of these methods is measured in different scenarios
via Monte–Carlo simulation. Despite the acceptable accuracy of
the detectors, for the special case of downlink TDMA burst
transmission, the performance of detection methods is improved by
proposing a blind synchronisation algorithm based on the
regularity of the bursts in downlink TDMA structure. The proposed
synchronisation algorithm is an iterative algorithm which is applied
on the initial detection. The results of simulations demonstrate that
the synchronisation algorithm can improve the results of initial
detection of ED, MMED, ACD, and ERD. It should be noted again
that the problem investigated here is different from the cooperative
(i.e. non-blind) TDMA synchronisation in which the TDMA
structure and synchronisation patterns are known to the receiver
[31–33, 36–38]. In fact, in cooperative communications, some
additional bits or specific patterns are generally embedded in the
bursts to help the authorised receiver for synchronisation.
The rest of this paper is organised as follows. In Section 2,
signal model is presented. In Sections 3, ACD, ED, ERD, and
MMED are generalised and developed for burst detection. In
Section 4, a blind synchronisation algorithm is proposed for
downlink TDMA signals based on the regularity of bursts in
downlink TDMA structure. Simulation results are presented in
Section5. Finally, the paper is concluded in Section 6.
2 Signal model
Consider a wireless communication network which employs a
burst-mode data transmission scheme. In such network, each user
transmits its packets by means of some bursts. The bursts are
distributed according to either a predefined rule (e.g. TDMA) or a
contention-based channel access method. Assume that the received
(i.e. eavesdropped) signal is sampled at a specific sampling rate.
So, in burst i, n
B
(i) noisy signal samples are received. Usually, a
guard time is considered after each burst in order to prevent
transmitted bursts from different users overlapping due to different
path delays. Assume that the length of guard for burst i is n
G
(i)
samples. Also, assume that N
s
samples are received (i.e.
eavesdropped) and there exist M
s
bursts in these observations (M
s
depends on N
s
). So, the received signal samples can be modelled as
r( j) =
s(j) + n(j) for
∑
i = 1
M
s
n
B
(i) samples
n(j) for N
s
−
∑
i = 1
M
s
n
B
(i) samples
,
(1)
where n( j) ( j = 1, 2, . . . , N
s
) are samples of independent complex
additive Gaussian noise with known variance σ
n
2
per real
dimension. Moreover, the values of s(j) ( j = 1, 2, . . . , N
s
) are the
samples of received bursts. Note that, in this model which is the
generalised form of the model proposed in [26] for transient signal
detection, bursts samples are aggregated into a single stream s(j). If
M
s
= 1 and the samples of n
B
(1) are considered to be consecutively
transmitted, transient signal model is obtained.
In both predefined and contention-based channel access
methods, the number of transmitted bursts may be less than the
maximum available bursts. For example, in TDMA channel access
method, a user may or may not have a packet to send in its pre-
allocated time slots. For TDMA, we define channel occupancy rate
(COR) as follows
COR =
Δ
lim
N
s
→ ∞
∑
i = 1
M
s
n
B
(i) + n
G
(i)
N
s
.
(2)
Usually, in TDMA channel access method, the length of all bursts
(and likewise the length of all guards) are assumed to be equal. In
other words,
n
B
(i) = n
B
and
n
G
(i) = n
G
for
i = 1, 2, . . . , M
s
.
The aim of the blind receiver is to obtain the values of
n
B
(i); i = 1, 2, …, M
s
and the exact position of the bursts in the
received samples
r( j); j = 1, 2, …, N
s
. In other words, a blind
receiver should estimate the start and the end of all bursts (i.e. data
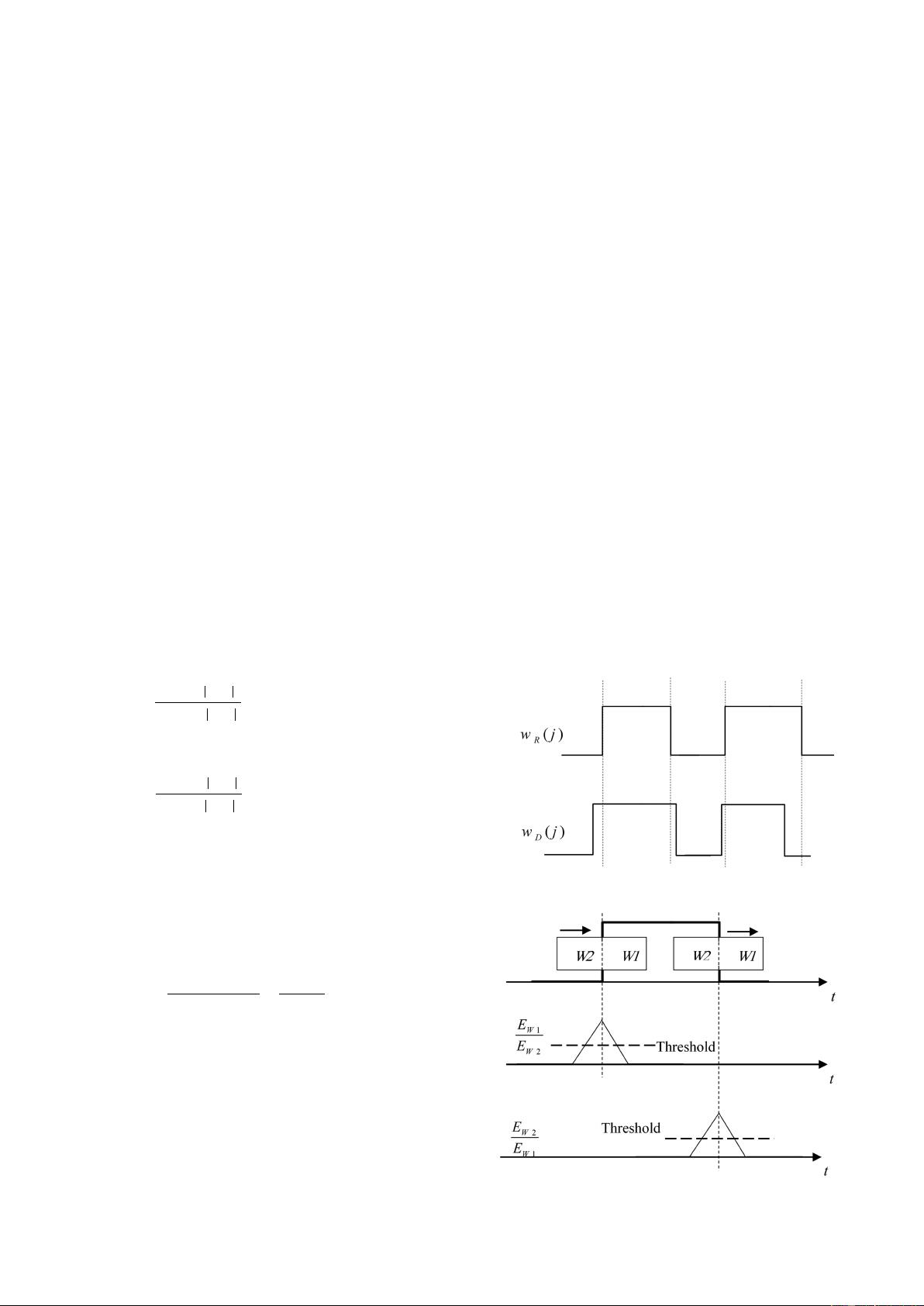
packets) in an eavesdropped signal. By using a binary function
(denoted by
w
R
(j); j = 1, 2, …, N
s
), the position of bursts can be
defined as follows: for the samples corresponding to the bursts, the
value of w
R
(j) is 1; and for the samples corresponding to the guard
times (i.e. noise-only samples), the value of
w
R
(j) is 0. If we define
dummy signal samples corresponding to
N
s
− ∑
i = 1
M
s
n
B
(i)
noise-
only samples in (1), we can rewrite (1) as
r( j) = w
R
(j)s(j) + n( j); j = 1, 2, . . . , N
s
,
(3)
where
w
R
(j) =
1 for
∑
i = 1
M
s
n
B
(i) burst samples
0 for N
s
−
∑
i = 1
M
s
n
B
(i) noise − only samples
.
(4)
We call
w
R
(j) the reference burst position indicator. Let us denote
the estimation of the blind receiver about
w
R
(j) by
w
D
(j). In ideal
receiver,
w
D
(j) = w
R
(j) for
j = 1, 2, . . . , N
s
. However, in practical
situations,
w
D
(j) and
w
R
(j) may not be identical functions (see
Fig. 1). We propose to use Dice similarity coefficient [39] for
evaluating the accuracy of the blind burst detector. Since w
D
(j) and
w
R
(j) are binary functions, we can write Dice similarity coefficient
between w
D
(j) and
w
R
(j) as
D(w
R
, w
D
) =
∑
j = 1
N
s
1 − w
R
(j) 1 − w
D
(j)
N
s
+
∑
j = 0
N
s
− 1
w
R
(j)w
D
(j)
N
s
.
(5)
It is obvious that in the case of error-free estimation, we have
D(w
R
, w
D
) = 1
. We can express Dice similarity coefficient in
percentage if we multiply both sides of (5) by 100.
864 IET Commun., 2019, Vol. 13 Iss. 7, pp. 863-872
© The Institution of Engineering and Technology 2019
Authorized licensed use limited to: BEIJING INSTITUTE OF TECHNOLOGY. Downloaded on September 02,2020 at 05:32:37 UTC from IEEE Xplore. Restrictions apply.

 ERD_滑动窗口_信号检测_突发通信_突发检测_非合作信号_源码.zip (2个子文件)
ERD_滑动窗口_信号检测_突发通信_突发检测_非合作信号_源码.zip (2个子文件)  non-cooperative burst detection.pdf 3.05MB
non-cooperative burst detection.pdf 3.05MB ERD.m 5KB
ERD.m 5KB




 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功

- 1
- 2
- 3
- 4
- 5
前往页