
1
A MINI PROJECT ON
IMPROVED METHOD TO INCREASE
THE AES SYSTEM SPEED
SUBMITTED BY
ZEBA ZAREEN
(12071D5718)

2
INDEX
TOPIC PAGE NO
I.INTRODUCTION 1-25
1.1 Introduction 5
1.2 Cryptography 6
1.3 Encryption 11
1.4 Decryption 11
1.5 Cipher 11
1.6 Background of AES 18
1.7 Different methods to encrypt/decrypt data 22
1.7.1 DES 22
1.7.2 Triple DES 23
1.7.3 TWO FISH 24
1.7.4 MARS 25
1.7.5 RC6 25
1.7.6 SERPENT 25
1.8 Substitution-permutation network 26
II. WORKING OF AES 28-46
2.1 Brief overview of AES 28
2.2 AES Algorithm phases 29
2.3 AES data patterns 32

3
2.4 Rounds 33
2.4.1 Stages of rounds in AES method 33
2.5 The encryption scheme 38
2.6 Overview of AES Encryption
Using flow diagram 41
2.7 Optimization of cipher 43
2.8 AES algorithm initialization 45
2.9 Algorithm process 46
III. APPLICATIONS 47
IV. CONCLUSION 48
V. SOURCE CODE 49-70
VI. SIMULATION RESULTS 71

4
LIST OF FIGURES
TOPIC PAGE NO
2.1 Internet or private data network 7
2.2 Classification of ciphers 13
2.3 Steps to encrypt data using Triple DES 23
2.4 Substitution and Permutation Network 27
2.5 Block diagram of AES 29
2.6 Block diagram of AES Algorithm 31
2.7 Block diagram of stages of a Round 33
2.8 Block diagram of AES Encryption Process 40
2.9 Flow diagram of AES encryption 42
2.10 AES Forward Cipher Flow-Graph 45
5
I. INTRODUCTION
1.1 INTRODUCTION
Network security is becoming more and more important as people spend more and
more time connected in a network .Security attacks include unauthorized reading of
message of file, traffic analysis, modification of messages or files and denial of
service. An effective network security strategy requires identifying threats and then
choosing the most effective set of tools to combat them. Network security is looming
on the horizon as a potentially massive problem. Most security problems are
intentionally caused by malicious people trying to gain some benefit , get attention or
to harm someone. Few most common perpetrators are listed:
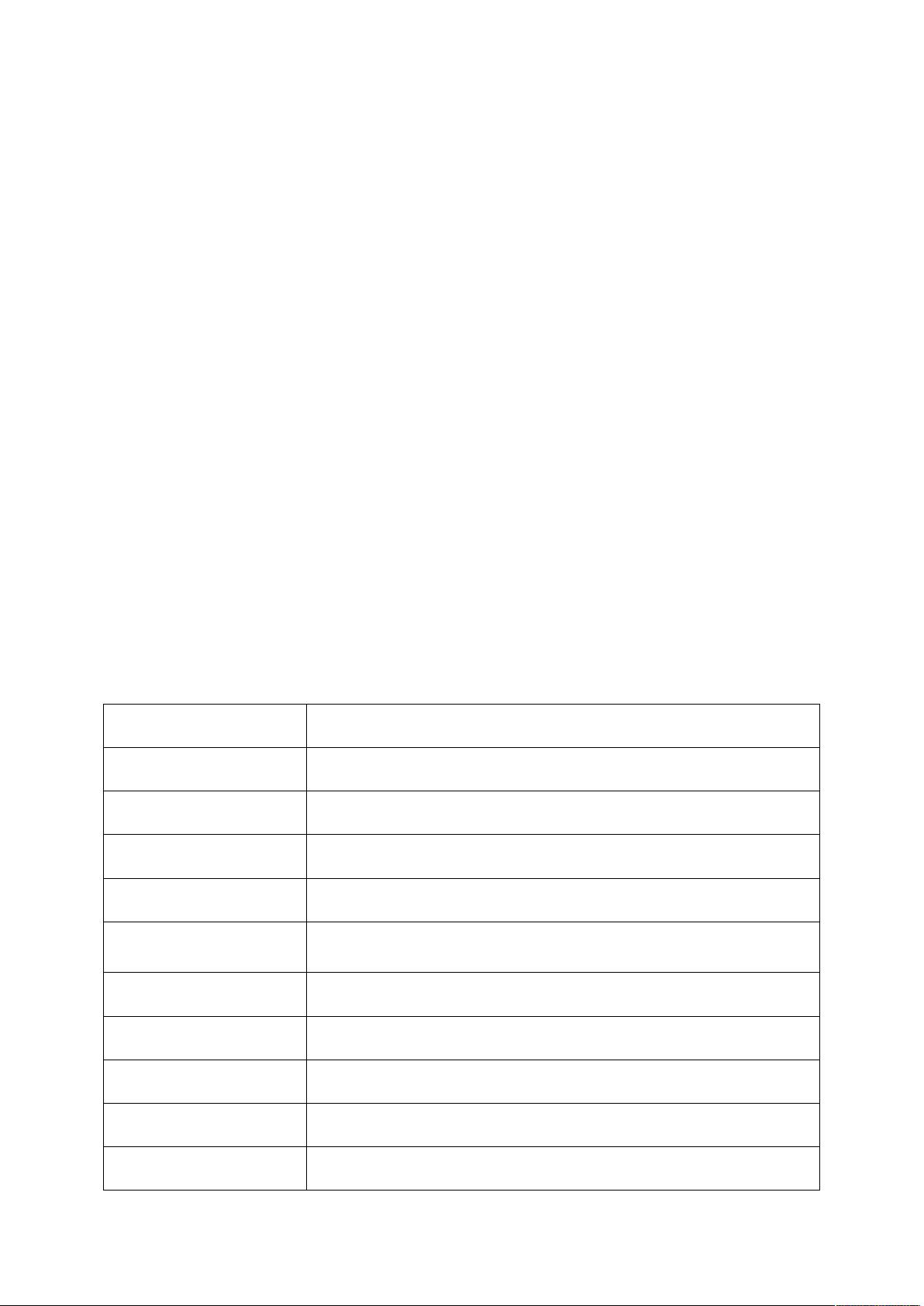
Table 1.1: Some people who cause security problems and why
It should be clear from the list that making a network secure involves a lot more than
just keeping it free of programming errors. It involves out smarting often intelligent,
dedicated and sometimes well-funded adversaries .
Network security problems can be divided roughly into four closely interwined areas:
secrecy, authentication ,nonrepudiation and integrity control.
ADVERSARY
GOAL
Student
To have fun snooping on peoples email
Cracker
To test out some ones secure system;steal data
Sales representive
To claim to represent all of Europe
Businessman
To discover a competetors strategic marketing plan
Ex-employee
To get revenge for being fired
Accountant
To embezzle money from a company
Stock broker
To deny a promise made to customer by email
Con man
To steal credit card numbers for sale
Spy
To learn an enemy military or industrial secrets
Terrorist
To steal warfare secrets















