
IEEE Wireless Communications • February 2014
33
1536-1284/14/$25.00 © 2014 IEEE
MOBILE SOCIAL NETWORKS
INTRODUCTION
As reported by ComScore [1], social networking
sites such as Facebook and Twitter have reached
84 percent of the world’s online population, rep-
resenting 1.3 billion users around the world. In
the meantime, fueled by the dramatic advance-
ments of smartphones and the ubiquitous con-
nections of Internet networks, social networking
further becomes available for mobile users and
keeps them posted on up-to-date worldwide
news and messages from their friends and fami-
lies anytime anywhere. The convergence of
social networking, advanced smartphones, and
stable network infrastructures brings us a perva-
sive and omnipotent communication platform,
mobile social networking (MSN), helping us stay
connected better than ever.
The boom of mobile applications is one of the
important factors in MSN development. It is
reported from WiKi that Apple Inc. has greatly
increased the number of mobile applications from
800 in July 2008 to over 825,000 in April 2013.
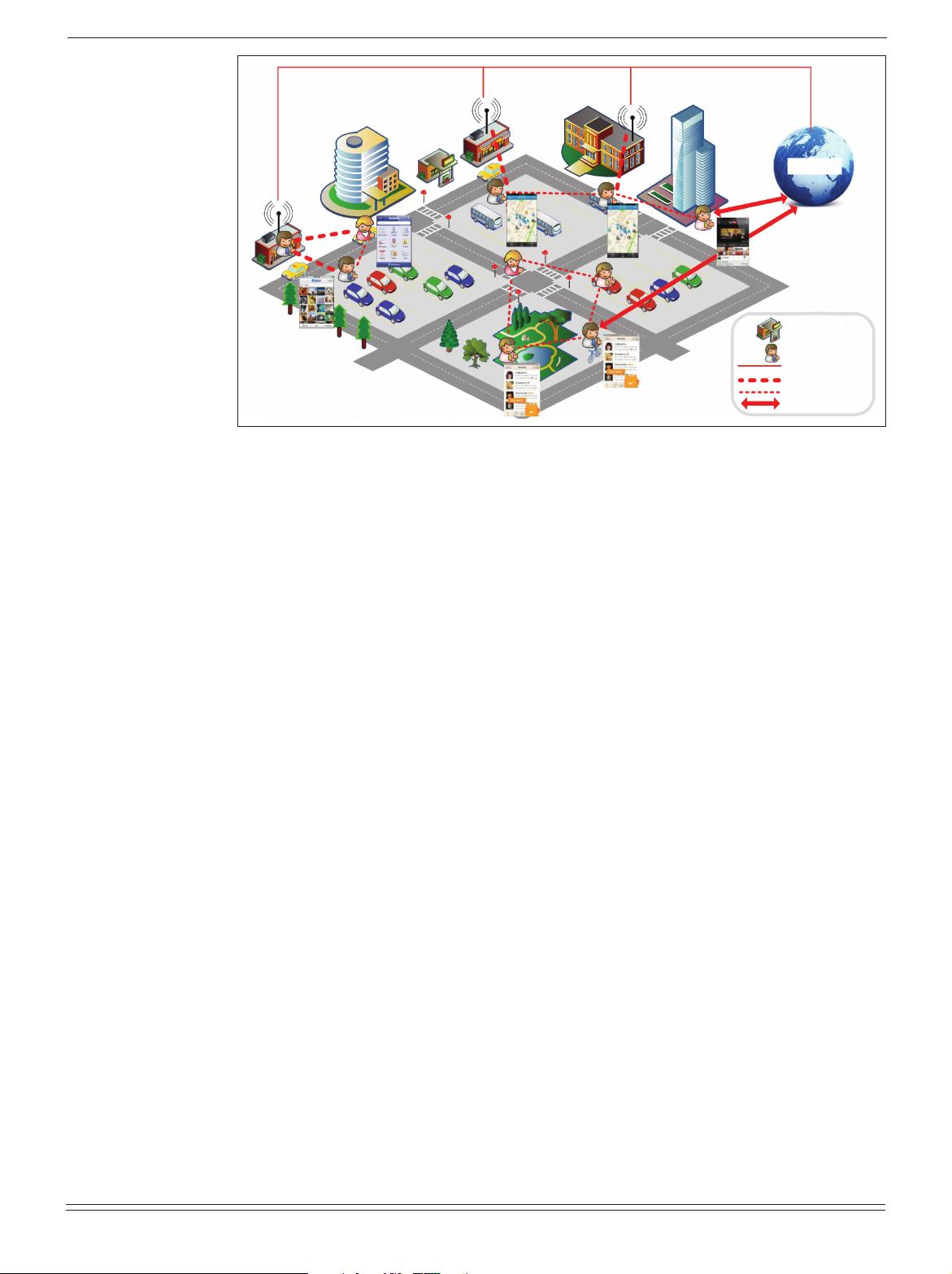
Generally, these mobile applications can be divid-
ed into three categories. The first category is
mobile versions of online social applications
(OSAs), which enable users to check social
updates, share photos, and watch online videos in
a mobile environment. The communications
remain between smartphone users (SUs) and
Internet service providers (ISPs). Web-based/
password-based authentication can be continuous-
ly applied to prevent SUs’ content from being
accessed by unauthorized entities. Security and
privacy are not difficult to solve because the ISPs
are fully trusted by the SUs. In addition to voice
service available for any cellular telephone, smart-
phones distinguish themselves by powerful com-
puting resources and, most significantly, their
capability to understand their surrounding envi-
ronments through many sensors that are built into
them. As a result, the second category, location-
based applications, becomes one of the most pop-
ular. It utilizes the information downloaded from
the Internet to assist location-based activities.
Such applications are widely supported by either
social network giants like Facebook or specialized
service providers like Foursquare and Loopt. The
main idea is as follows: The GPS chips detect the
location coordinates of the SUs, who then report
the coordinates to the ISPs for downloading the
information related to local services. However, it
raises a serious privacy issue; the continuously dis-
closed location coordinates may reveal where,
when, or even what SUs have done. To prevent
abuse of their location coordinates, SUs have to
often manually switch localization on and off to
control access to their location information. The
third category is autonomous mobile applications,
where SUs are able to connect to neighboring
SUs and local service providers (LSPs) through
short-range wireless communications such as near
field communication (NFC), Bluetooth, and WiFi
Direct. For example, a nearby information search
application [2] helps an SU consult her nearby
friends, who in turn will ask their friends, and so
on, until the information is found. In this applica-
tion, the SUs are not required to have an Internet
connection. Besides, navigating for information
via neighboring SUs could be better than Internet
search because the information from a neighbor-
hood is often more personalized, localized, and
up-to-date. Autonomous mobile applications can
also be applied to facilitate car pool [3] and
healthcare purposes. However, the security and
privacy of such applications are very challenging.
In fact, SUs are unlikely to share their privacy-
sensitive destinations or healthcare symptoms
with strangers. Without a trust mediator, the pri-
vacy is easily violated, and thus the SUs are prob-
ably uncooperative.
XIAOHUI LIANG, KUAN ZHANG, AND XUEMIN SHEN, UNIVERSITY OF WATERLOO
XIAODONG LIN, UNIVERSITY OF ONTARIO INSTITUTE OF TECHNOLOGY
ABSTRACT
Mobile social networking is a pervasive com-
munication platform where users with smart-
phones can search over the Internet and query
neighboring peers to obtain the desired informa-
tion. In this article, we examine the architecture,
communication patterns, and especially the secu-
rity and privacy of MSN. We first study three
categories of mobile applications with a focus on
two autonomous mobile applications, business
card and service review. We then explore the
possible methods to deal with the associated
security and privacy challenges. By discussing the
shortages of the methods, we finally provide sev-
eral promising research directions.
SECURITY AND PRIVACY IN MOBILE SOCIAL
NETWORKS: CHALLENGES AND SOLUTIONS
LIANG_LAYOUT_Layout 2/25/14 3:37 PM Page 33


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功