没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论

Solana: A new architecture for a high
performance blockchain v0.8.13
Anatoly Yakovenko
anatoly@solana.io
Legal Disclaimer Nothing in this White Paper is an offer to sell, or the solicitation of an offer
to buy, any tokens. Solana is publishing this White Paper solely to receive feedback and comments from
the public. If and when Solana offers for sale any tokens (or a Simple Agreement for Future Tokens), it
will do so through definitive offering documents, including a disclosure document and risk factors. Those
definitive documents also are expected to include an updated version of this White Paper, which may
differ significantly from the current version. If and when Solana makes such an offering in the United
States, the offering likely will be available solely to accredited investors.
Nothing in this White Paper should be treated or read as a guarantee or promise of how Solanas
business or the tokens will develop or of the utility or value of the tokens. This White Paper outlines
current plans, which could change at its discretion, and the success of which will depend on many factors
outside Solanas control, including market-based factors and factors within the data and cryptocurrency
industries, among others. Any statements about future events are based solely on Solanas analysis of the
issues described in this White Paper. That analysis may prove to be incorrect.
Abstract
This paper proposes a new blockchain architecture based on Proof
of History (PoH) - a proof for verifying order and passage of time
between events. PoH is used to encode trustless passage of time into
a ledger - an append only data structure. When used alongside a
consensus algorithm such as Proof of Work (PoW) or Proof of Stake
(PoS), PoH can reduce messaging overhead in a Byzantine Fault Tol-
erant replicated state machine, resulting inn sub-second finality times.
This paper also proposes two algorithms that leverage the time keep-
ing properties of the PoH ledger - a PoS algorithm that can recover
from partitions of any size and an efficient streaming Proof of Replica-
tion (PoRep). The combination of PoRep and PoH provides a defense
against forgery of the ledger with respect to time (ordering) and stor-
age. The protocol is analyzed on a 1 gbps network, and this paper
shows that throughput up to 710k transactions per second is possible
with todays hardware.
1

1 Introduction
Blockchain is an implementation of a fault tolerant replicated state machine.
Current publicly available blockchains do not rely on time, or make a weak
assumption about the participants abilities to keep time [4, 5]. Each node in
the network usually relies on their own local clock without knowledge of any
other participants clocks in the network. The lack of a trusted source of time
means that when a message timestamp is used to accept or reject a message,
there is no guarantee that every other participant in the network will make
the exact same choice. The PoH presented here is designed to create a ledger
with verifiable passage of time, i.e. duration between events and message
ordering. It is anticipated that every node in the network will be able to rely
on the recorded passage of time in the ledger without trust.
2 Outline
The remainder of this article is organized as follows. Overall system design is
described in Section 3. In depth description of Proof of History is described
in Section 4. In depth description of the proposed Proof of Stake consensus
algorithm is described in Section 5. In depth description of the proposed
fast Proof of Replication is described in Section 6. System Architecture and
performance limits are analyzed in Section 7. A high performance GPU
friendly smart contracts engine is described in Section 7.5
3 Network Design
As shown in Figure 1, at any given time a system node is designated as
Leader to generate a Proof of History sequence, providing the network global
read consistency and a verifiable passage of time. The Leader sequences user
messages and orders them such that they can be efficiently processed by other
nodes in the system, maximizing throughput. It executes the transactions
on the current state that is stored in RAM and publishes the transactions
and a signature of the final state to the replications nodes called Verifiers.
Verifiers execute the same transactions on their copies of the state, and pub-
lish their computed signatures of the state as confirmations. The published
confirmations serve as votes for the consensus algorithm.
2
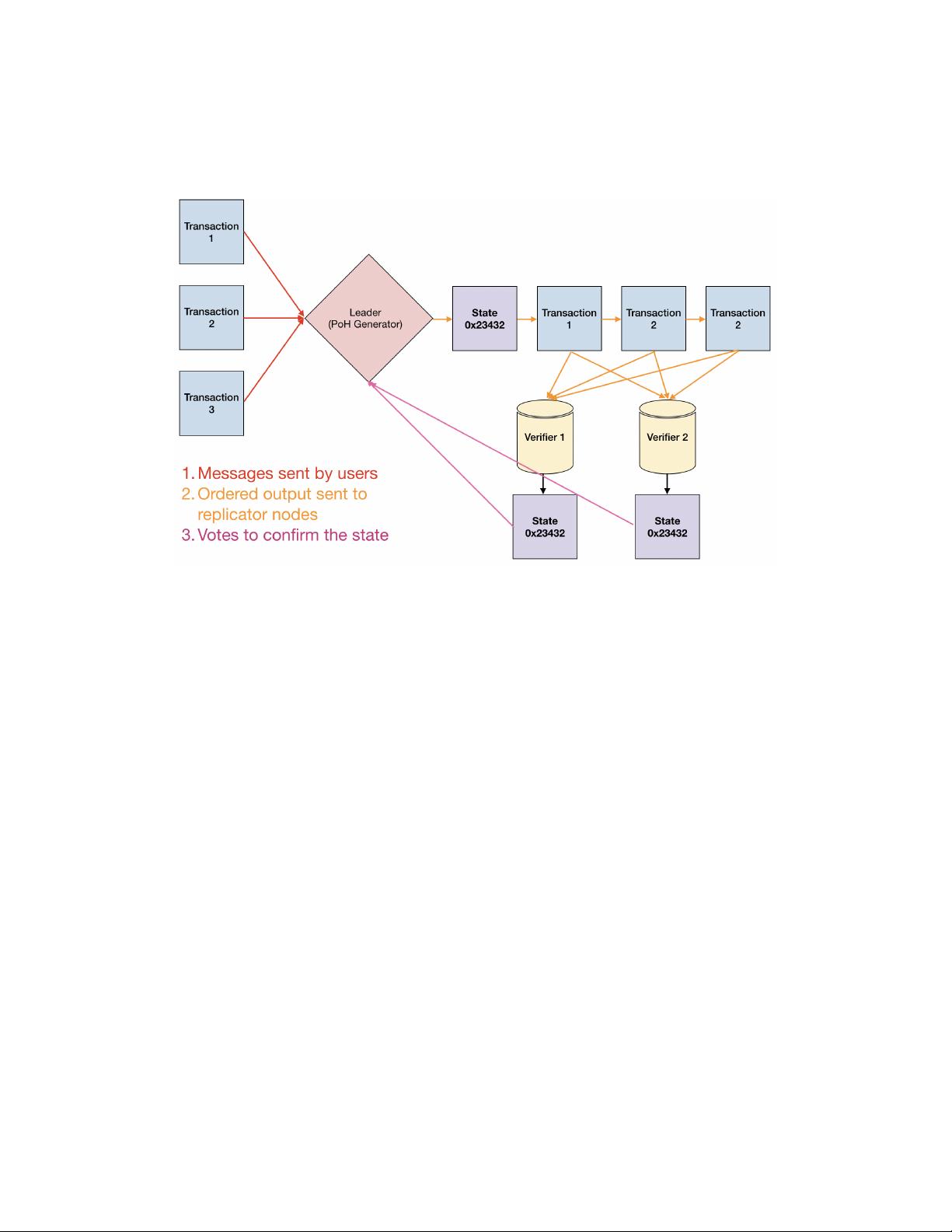
Figure 1: Transaction flow throughout the network.
In a non-partitioned state, at any given time, there is one Leader in the
network. Each Verifier node has the same hardware capabilities as a Leader
and can be elected as a Leader, this is done through PoS based elections.
Elections for the proposed PoS algorithm are covered in depth in Section 5.6.
In terms of CAP theorem, Consistency is almost always picked over Avail-
ability in an event of a Partition. In case of a large partition, this paper
proposes a mechanism to recover control of the network from a partition of
any size. This is covered in depth in Section 5.12.
4 Proof of History
Proof of History is a sequence of computation that can provide a way to
cryptographically verify passage of time between two events. It uses a cryp-
tographically secure function written so that output cannot be predicted
from the input, and must be completely executed to generate the output.
The function is run in a sequence on a single core, its previous output as the
3

current input, periodically recording the current output, and how many times
its been called. The output can then be re-computed and verified by external
computers in parallel by checking each sequence segment on a separate core.
Data can be timestamped into this sequence by appending the data (or a
hash of some data) into the state of the function. The recording of the state,
index and data as it was appended into the sequences provides a timestamp
that can guarantee that the data was created sometime before the next hash
was generated in the sequence. This design also supports horizontal scaling
as multiple generators can synchronize amongst each other by mixing their
state into each others sequences. Horizontal scaling is discussed in depth in
Section 4.4
4.1 Description
The system is designed to work as follows. With a cryptographic hash func-
tion, whose output cannot be predicted without running the function (e.g.
sha256, ripemd, etc.), run the function from some random starting value
and take its output and pass it as the input into the same function again.
Record the number of times the function has been called and the output at
each call. The starting random value chosen could be any string, like the
headline of the New York times for the day.
For example:
PoH Sequence
Index Operation Output Hash
1 sha256(”any random starting value”) hash1
2 sha256(hash1) hash2
3 sha256(hash2) hash3
Where hashN represents the actual hash output.
It is only necessary to publish a subset of the hashes and indices at an
interval.
For example:
4
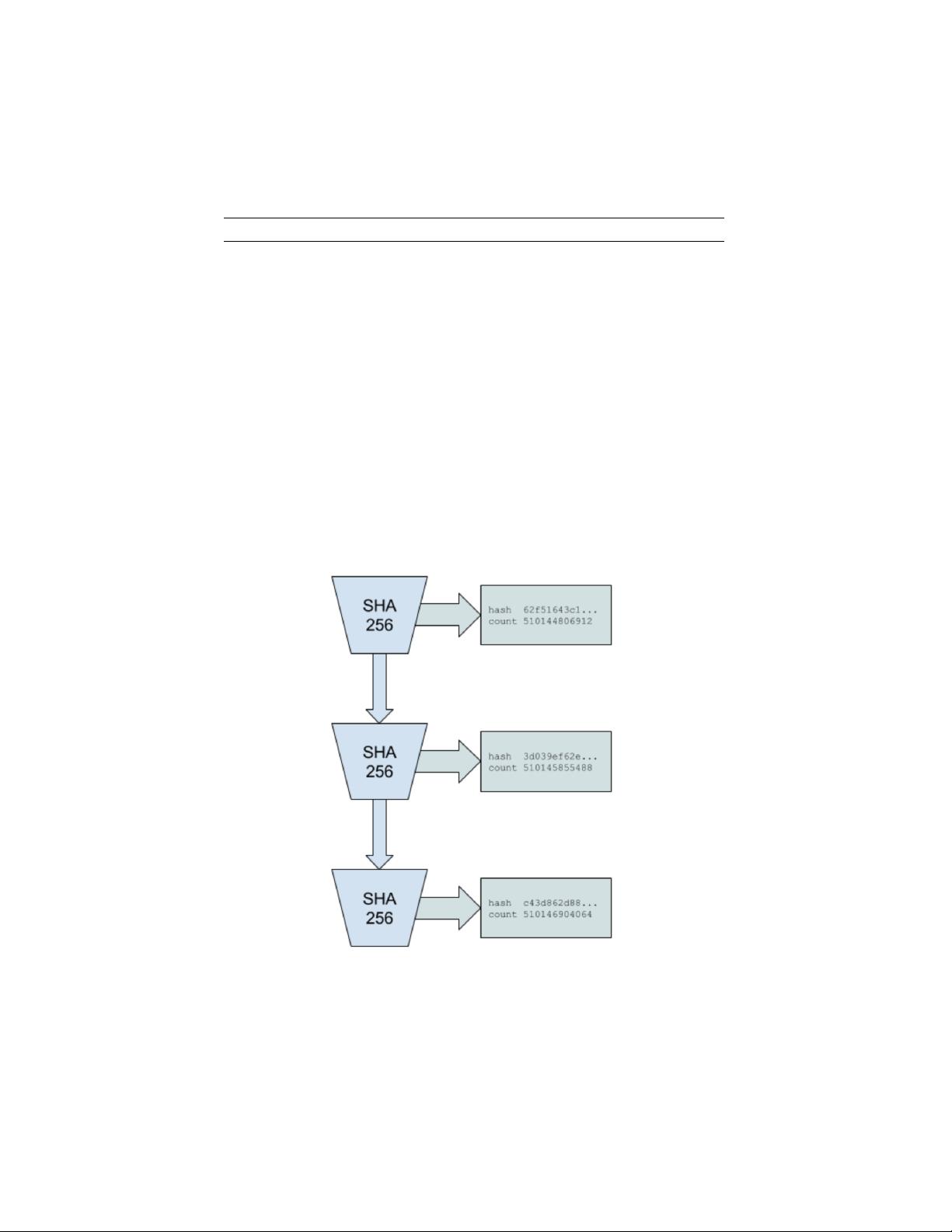
PoH Sequence
Index Operation Output Hash
1 sha256(”any random starting value”) hash1
200 sha256(hash199) hash200
300 sha256(hash299) hash300
As long as the hash function chosen is collision resistant, this set of hashes
can only be computed in sequence by a single computer thread. This follows
from the fact that there is no way to predict what the hash value at index
300 is going to be without actually running the algorithm from the starting
value 300 times. Thus we can thus infer from the data structure that real
time has passed between index 0 and index 300.
In the example in Figure 2, hash 62f51643c1 was produced on count
510144806912 and hash c43d862d88 was produced on count 510146904064.
Following the previously discussed properties of the PoH algorithm, we can
trust that real time passed between count 510144806912 and count 510146904064.
Figure 2: Proof of History sequence
5
剩余31页未读,继续阅读
资源评论

百态老人
- 粉丝: 6946
- 资源: 2万+

下载权益

C知道特权

VIP文章

课程特权
开通VIP
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功