VP2RQ:Efficient Verifiable Privacy-Preserving Range Query Proces...
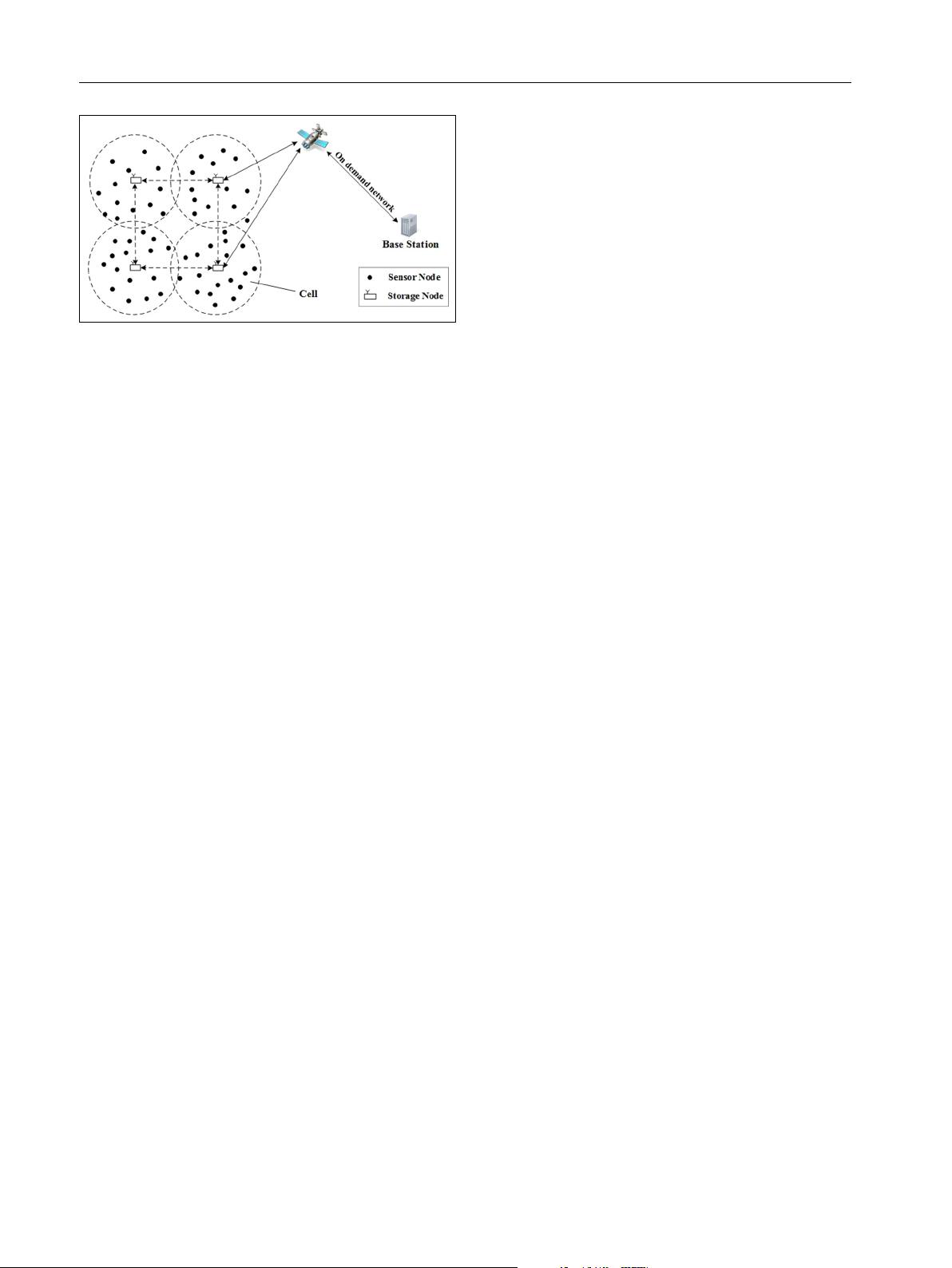
VP2RQ:Efficient Verifiable Privacy-Preserving Range Query Processing in Two-tieredWireless Sensor Networks 在无线传感网络(WSNs)领域,安全范围查询技术一直是一个挑战性问题。尤其是在两级无线传感器网络中,提出了一种基于桶划分、信息身份认证和校验码融合的可验证隐私保护范围查询处理方法。该方法在数据收集过程中,每个传感器节点根据桶划分策略将收集到的数据放入相应的桶中,对非空桶进行加密,为已加密的桶生成校验码,并将校验码与加密后的桶一起提交给父节点,直至这些数据送达存储节点。在查询处理期间,基站将查询范围转换为感兴趣的桶标签集,并发送到存储节点。存储节点确定候选的加密桶,通过代码融合生成校验码,并将它们发送到基站。基站获得查询结果并使用校验码验证结果的完整性。理论分析和实验结果均表明,可验证隐私保护范围查询能够保护传感器数据、查询结果和查询范围的隐私,同时支持查询结果的完整性验证。与其他现有方法相比,可验证隐私保护范围查询在通信成本上有更好的性能。 关键词:两级无线传感器网络、隐私保护、完整性验证、范围查询、桶划分 引言部分提到,随着互联网技术、云计算、图像识别和视频处理等新兴技术的快速发展,无线传感器网络作为物联网技术中的关键技术之一,已被广泛应用于各个领域。隐私保护在这些应用中至关重要,因为网络中传输的敏感数据可能会受到未经授权的访问和使用,导致严重的安全问题和隐私泄露。为了保证数据的安全性和用户隐私,就需要研究高效的隐私保护范围查询技术。 文章中提到的桶划分是一种数据组织技术,它允许将数据集按某种规则分配到多个桶(或容器)中。通过这种方式,数据被分组和存储,使得查询可以更加高效和安全地执行。在加密桶内数据时,采用了加密技术来保护数据的机密性。对于那些空桶,虽然它们不包含实际的数据,但生成校验码的目的是为了确保数据的完整性,即保证数据没有在传输过程中被篡改。 信息身份认证是一种安全机制,用于验证数据在存储或传输过程中的真实性,确保数据是由合法的传感器节点发送的,未经篡改。检查码融合则是将多个校验码合并成一个综合校验码,用于在数据查询时快速验证数据的完整性和一致性。 在该论文的研究中,一个完整的查询处理流程包括数据收集、数据加密、数据发送、查询转换、查询结果获取和结果验证等多个步骤。而在实验结果中,作者对比分析了提出的查询处理方法与现有技术的性能,尤其是在通信成本上取得的改进。 该研究的理论分析部分详细探讨了所提出方法的安全性、隐私保护和完整性验证等关键技术特性。而实验结果部分则通过具体的性能指标,如通信成本、处理时间等,展示了该方法相比现有技术的效率和实用性。该研究的结论强调了安全、隐私保护和效率是实现可靠无线传感网络应用所必须综合考虑的因素,并指出了未来研究可能的发展方向,如对更复杂场景和更多样化数据类型的支持。

剩余14页未读,继续阅读

- 粉丝: 6
- 资源: 941
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 基于java+ssm+mysql的可视化高校公寓管理系统 源码+数据库+论文(高分毕设项目).zip
- "高压直流输电仿真(HVDC)研究:双侧调谐器与双闭环控制策略的优化及MATLAB仿真结果报告",高压直流输电仿真(HVDC),AD-DC-AC双侧均采用调谐器 整流侧采用电压电流双闭环控制,逆变侧
- 基于java+ssm+mysql的量化积分管理系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的绿色蔬菜销售管理系统 源码+数据库+论文(高分毕设项目).zip
- Python自动化办公源码-03一键抓出PPT中所有文字
- 基于java+ssm+mysql的敏捷工贸公司销售管理系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的农家乐内部管理系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的农产品质量安全检测网站 源码+数据库+论文(高分毕设项目).zip
- 电子凸轮位置跟随区间运动Ver1.2.1:精准主轴伺服与从轴伺服联动控制,电子凸轮-区间运动Ver1.2.1(位置跟随,去程) 0.一个主轴伺服(定速)+一个从轴伺服 1.主轴伺服定速运动(主轴启动时
- 基于java+ssm+mysql的社区团购网站 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的商城系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的软件开发团队管理网站 源码+数据库+论文(高分毕设项目).zip
- IEEE69节点系统Simulink仿真模型:潮流计算与故障分析及分布式电源影响观察,IEEE69节点系统Simulink仿真 1.基础功能:基于Matlab simulink平台搭建IEEE33节点
- 基于java+ssm+mysql的实验室管理与排课系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的社区再就业培训管理系统 源码+数据库+论文(高分毕设项目).zip
- 基于java+ssm+mysql的生鲜在线销售系统 源码+数据库+论文(高分毕设项目).zip


 信息提交成功
信息提交成功