没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
忆阻器是一种非线性的无源两端电气装置,目前在神经网络中得到了广泛的应用。 通过结合Hermite多项式和忆阻器,建立忆阻性Hermite混沌神经网络(MHCNN),提出了一种新的Hermite神经网络突触权重更新学习规则。 混沌序列是由神经网络的权重和混沌初始值生成的。 最终我们可以通过加密明文来获得密文。 忆阻器的使用产生了非常特殊的神经网络,它不仅可以改变神经网络中的多项式,而且可以实现多样性,并且可以有效地提高通信的机密性。
资源推荐
资源详情
资源评论

A novel memristive electronic synapse-based Hermite chaotic neural
network with application in cryptography
Xinli Shi
a
, Shukai Duan
a,
n
, Lidan Wang
a
, Tingwen Huang
b
, Chuandong Li
a
a
School of Electronic and Information Engineering, Southwest University, Chongqing, China
b
Department of Electrical and Computer Engineering Texas A&M University, Doha, Qatar
article info
Article history:
Received 10 August 2014
Received in revised form
30 October 2014
Accepted 5 March 2015
Communicated by He Huang
Available online 28 April 2015
Keywords:
Hermite neural network
Memristor
Chaotic
Encryption
Decryption
abstract
The memristor is a kind of non-linear passive two-terminal electrical device, which is widely applied in
neural networks currently. In this paper, a new synaptic weight update learning rule of Hermite neural
network is proposed by combining Hermite polynomials with memristors to build a memristive Hermite
chaotic neural network (MHCNN). The chaotic series is generated by the weights of the neural network
and chaotic initial value. And ultimately we can obtain the ciphertext by encrypting the plaintext. The
use of memristors results in a very special neural network, which can not only change the polynomial in
neural network but also achieve the diversity, and the confidentiality of communication is also improved
effectively.
& 2015 Elsevier B.V. All rights reserved.
1. Introduction
The concept of memristor was initially proposed by Chua in
1 971 [1]. However, it is until the year of 2008 that HP Lab declared
the physical realization of the memristor [2–4]. Since then, wide
attention around the world was put on this newly-found element.
Several years' researches have witnessed the proposals of a
number of new memristor models [5–13]. Because of its unique
switch mechanism, natural memory function, continuous input
and output characteristics and nanoscale size, the memristor has
shown great potential in nonvolatile memory, artificial neural
networks and intelligent information etc. and aroused lots of
studies in these fields [14–22]. For example, Afifi et al. studied
the realization of STDP learning rules based on the pulsing
neuromorphic networks with memristor cross-array [14]. Sangho
et al. demonstrated that memristors can be used to implement
programmable analog circuits, leveraging memristor's fine-
resolution programmable resistance without causing perturba-
tions due to the parasitic components [15]. Duan et al. proposed
memristor-based resistive random access memory (MRRAM) and
verified its effectiveness in storing ASCII characters and gray-scale
images in binary format [16]. Duan et al. also studied chaotic
circuity [17,27–31] and memristor-based cellular nonlinear/neural
network [18]. Wang et al. maked important studies of memristor
model and chaos generation [19]. Among all the memristor's
properties shown before, the uniqueness of nanoscale size has
attracted much attention and interests. Because of that character-
istic, a small voltage through it will cause strong change in electric
field and then lead to nonlinear ionic drift, which brings about the
proposal of nonlinear memristor models and related research.
As is known, the applications of digital information have made
great contribution to the rapid development of modern technology
and network. The process of gaining information becomes simpler
and easier, however, the secrecy of communication calls forth the
researchers' attention gradually. In secret communication, crypto-
graphy is one of the basic methods, which is about the practice
and study of techniques for secure communication in the presence
of third parties, in other words, it is about constructing and
analyzing protocols that will overcome the influence of adver-
saries and are related to various aspects in information security,
such as data confidentiality, data integrity, authentication and
non-repudiation. Meanwhile, chaos, with the special superiority in
secure communication, is a seemly irregular inner random motion
in a deterministic system and a chaotic system has the properties
of complex pseudo-randomness and extreme sensitivity to initial
values, therefore it is reasonable to incorporate the conception of
chaotic system into communication encryption. Some valuable
work has been done [23–26]. In 1990, Carroll firstly built a
synchronous chaotic circuit [23]. Several years later, Milanovic
proposed the synchronization of chaotic neural networks [24].
Contents lists available at ScienceDirect
journal h omepage: www.else vier.com/locate/neu com
Neurocomputing
http://dx.doi.org/10.1016/j.neucom.2015.03.018
0925-2312/& 2015 Elsevier B.V. All rights reserved.
n
Corresponding author.
E-mail address: duansk@swu.edu.cn (S. Duan).
Neurocomputing 166 (2015) 487–495
After that, scholars started to apply the chaotic series to cryptology
with great enthusiasm. Their research shows that chaotic syn-
chronization encryption algorithm requires keeping highly con-
sistent between the sender and the receiver, otherwise, several
problems will be produced, such as parameters' mismatching,
inconformity between sent time and received time etc., which
makes the scholars embark on the study of asynchronous encryp-
tion algorithm.
This paper realizes the Hermite neural network's synaptic
weight update by memristors and obtains a special neural net-
work, which not only changes the polynomial in neural network
but also achieves diversity. Specifically, we trained the memristive
Hermite neural network (MHNN) by using Logistic chaotic series
and obtained memristive Hermite chaotic neural network
(MHCNN), whose structure is special and meets the requirements
of encryption, for the receiver to decrypt the plaintext asynchro-
nously. It must be stated here that encryption and decryption in
this paper use the same network which must be sent secretly.
Moreover, both the cross-correlation function values between
different chaos initial values tend to be zero and the entirely
different ciphertexts improve the security of communication.
The rest of the paper is organized as follows. In Section 2, the
nonlinear memristor model is introduced. The relationships
between the main variables are given by numerical simulation.
The changed rate of memristive conductance is described as the
synapse weight update rule based on theoretical derivation. In
Section 3, memristive Hermite neural network and learning
algorithm are described. Section 4 gets a MHCNN by using a
chaotic series to train the proposed MHNN. Then the MHCNN is
applied to encrypt one paragraph of secretary-general's message
on World Water Day in 2013. Section 5 uses another memristor
model with forgetting effects to build a memristive Hermite neural
network, which is applied to encrypt the same plaintext. The
results under different memristor models are compared. Finally,
the conclusions are given in Section 6.
2. The memristive electronic synapse
The physical model of the memristor consists of a two-layer
thin film of TiO
2
sandwiched between two platinum electrodes.
One of the layers is a thin film of TiO
2
which is doped with oxygen
vacancies. It is described as TiO
2x
and called as doped layer. The
other layer is described as TiO
2
, which is a pure thin film of TiO
2
and called as undoped layer. Generally, an external excitation v(t)
applied across the memristor may cause oxygen vacancies drift
under the action of electric field and the boundary between the
two regions would be moved correspondingly with the total
memristance changed eventually.
The resistance of the memristor can be calculated [21]
M ðtÞ¼R
on
ω tðÞ
D
þR
of f
1
ω tðÞ
D
ð1Þ
When ω¼D or ω¼0,thememristanceequalsR
on
or R
off
respec-
tivel y . Setting x ¼ðω=DÞA 0; 1
½
, (1) can be described as follows:
MtðÞ¼R
of f
þ R
on
R
of f
xtðÞ ð2Þ
M 0ðÞ¼R
of f
þ R
on
R
of f
x
0
; when t ¼ 0: ð3Þ
The movement rate of boundary between doped and undoped
regions
dx
dt
¼ ki tðÞfxðÞ; k ¼
μ
v
R
on
D
2
: ð4Þ
The a verag e ionic mobility is μ
v
E 10
14
m
2
s
1
V
1
. Real mem-
ristor is a nanoscale device, and enormous electric fields will be
produced when it is applied with a small voltage. And it can produce
significant nonlinearities in the ionic transport, so a pr oper window
function f(x)ontherightsideofEq.(4) is mult iplied to simulate the
nonlinear ionic drift. In general, classic window functions include
Joglekar window function and Biolek window function. Here, we
choose Joglekar window function, which can be described as
fxðÞ¼1 2x1ðÞ
2p
where p is a positi ve integer. The relationships between the memris-
tor's main variables vary with the change of parameter p,whichare
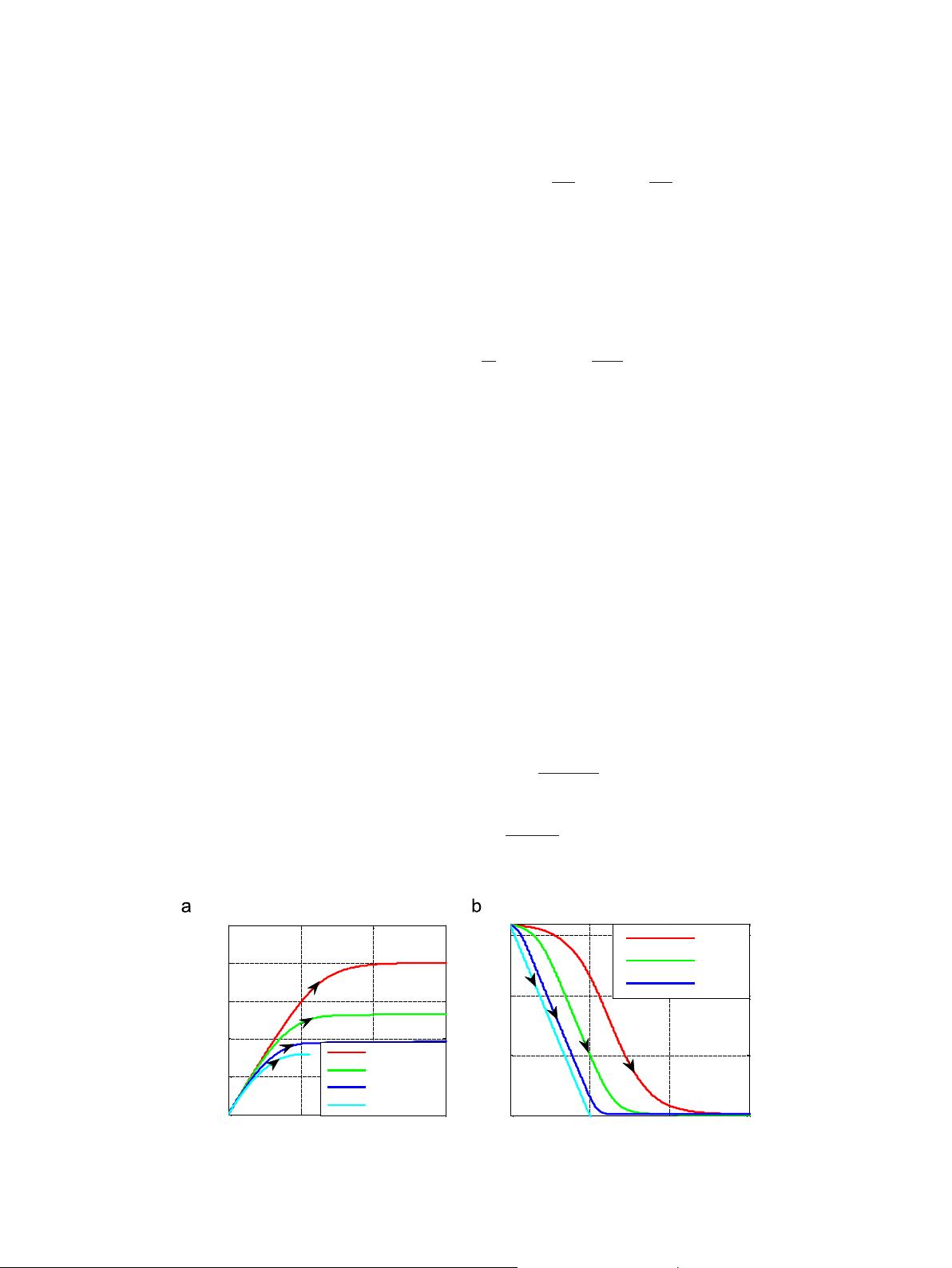
exhibited in Fig. 1.
The memristor model tends to be linear as the value of parameter
p becomes bigger. The nonlinearity of a memristor becomes the most
obvious when p¼ 1, which simulat es the nonlinear beha viors of
memristors better than other values. So we choose the window
function of p¼1.
fxðÞ¼4x 4x
2
ð5Þ
Substitute Eq. (5) into Eq. (4), and assume that there is no input
when t¼0, q
0
¼0. Finally, x(t) can be described by
xtðÞ¼1
1
Ae
4kq tðÞ
þ1
ð6Þ
where
A ¼
R
of f
R
on
R
0
R
on
: ð7Þ
0 1 2 3
x 10
-4
0
0.5
1
1.5
2
2.5
Charge ( c )
Flux ( Wb )
p=1
p=2
p=5
Linear Model
0 1 2 3
x 10
-4
0
5
10
15
Charge ( c )
Memristance ( K
Ω
)
p=1
p=2
p=5
Fig. 1. (a) Relationships between the charge and the flux for different values of parameter p. (b) Relationships between the charge and the memristance for different values
of parameter p.
X. Shi et al. / Neurocomputing 166 (2015) 487–495488
剩余8页未读,继续阅读
资源评论

weixin_38719643
- 粉丝: 7
- 资源: 941
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- YOLO算法-禾本科杂草数据集-4760张图像带标签.zip
- YOLO算法-无人机俯视视角动物数据集-10140张图像带标签-斑马-骆驼-大象-牛-羊.zip
- YOLO算法-挖掘机与火焰数据集-8129张图像带标签-挖掘机.zip
- YOLO算法-塑料数据集-3029张图像带标签-塑料制品-白色塑料.zip
- PyKDL库源码,编译安装PyKDL库
- YOLO算法-红外探测数据集-10573张图像带标签-小型车-人-无人机.zip
- 基于 C++和TCP和WebSocket的即时通信系统设计与实现(源码+文档)
- 电商管理系统项目源代码全套技术资料.zip
- 全国2022年04月高等教育自学考试02326操作系统试题及答案
- YOLO算法-垃圾数据集-3818张图像带标签-可口可乐-百事可乐.zip
- YOLO算法-瓶纸盒合并数据集-1317张图像带标签-纸张-纸箱-瓶子.zip
- YOLO算法-杂草检测项目数据集-3970张图像带标签-杂草.zip
- YOLO算法-杂草检测项目数据集-3853张图像带标签-杂草.zip
- YOLO算法-挖掘机与火焰数据集-7735张图像带标签-挖掘机.zip
- 文旅项目源代码全套技术资料.zip
- YOLO算法-罐头和瓶子数据集-1531张图像带标签-鲜奶-瓶子.zip
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功