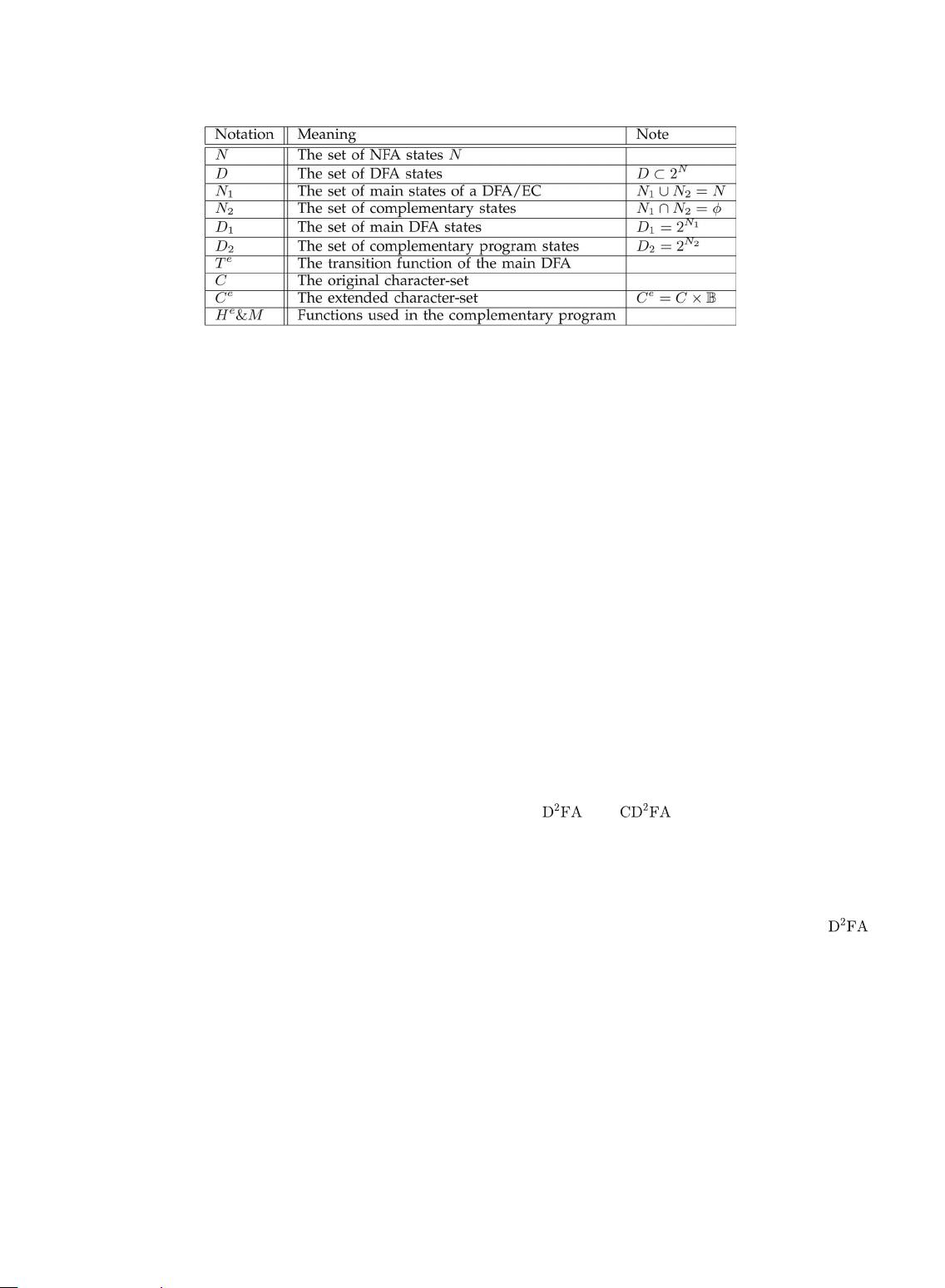
A DFA with Extended Character-Set for
Fast Deep Packet Inspection
Cong Liu, Yan Pan, Ai Chen, and Jie Wu, Fellow, IEEE
Abstract—Deep packet inspection (DPI), based on regular expressions, is expressive, compact, and efficient in specifying attack
signatures. We focus on their implementations based on general-purpose processors that are cost-effective and flexible to update. In this
paper, we propose a novel solution, called deterministic finite automata with extended character-set (DFA/EC), which can significantly
decrease the number of states through doubling the size of the character-set. Unlike existing state reduction algorithms, our solution
requires only a single main memory access for each byte in the traffic payload, which is the minimum. We perform experiments with several
Snort rule-sets. Results show that, compared to DFAs, DFA/ECs are very compact and are over four orders of magnitude smaller in the
best cases; DFA/ECs also have smaller memory bandwidth and run faster. We believe that DFA/EC will lay a groundwork for a new type of
state compression technique in fast packet inspection.
Index Terms—Deep packet inspection (DPI), regular expression, deterministic finite automata (DFA), extended character-set (EC)
1INTRODUCTION
D
EEP packet inspection (DPI) processes packet payload
content in addition to the structured information in
packet headers. DPI is becoming increasingly important in
classifying and controlling network traffic. Well-known in-
ternet applications of DPI include: network intrusion detec-
tion systems that identify security threats given by a rule-set of
signatures, content-based traffic management that provides
quality of service and load balancing, and content-based
filtering and monitoring that block unwanted traffic. Due to
their wide application, there is a substantial body of research
work [1]–[5] on high-speed DPI algorithms, in which different
automata for single-pass high-speed inspection are proposed
based on either software or hardware implementations.
Traditional packet inspection algorithms have been limited
to comparing packets to a set of strings. Newer DPI systems,
such as Snort [6], [7] and Bro [8], use rule-sets consisting of
regular expressions, which are more expressive, compact, and
efficient in specifying attack signatures. Hardware-based
approaches exploit parallelism and fast on-chip memory, and
are able to create compact automata. However, it is more cost-
effective and flexible to update when small on-chip lookup
engines or general-purpose processors are used together with
automata stored in off-chip commodity memory. In this
paper, we focus on a general-purpose processor approach.
The throughput of the general-purpose processor
approaches is limited by the memory bandwidth of the
processors. Therefore, to improve inspection speed, it is
critical to minimize the number of main memory (off-chip
memory) accesses per byte in the traffic payload. Some im-
plementations of the regular expressions, such as the non-
deterministic finite automata (NFAs), have a nondeterminis-
tic number of main memory accesses per byte. Another critical
issue is reducing the size of the automata stored in memory in
order to reduce the cost of memory, improving the scalability
for a larger number of rules, and increasing the inspection
speed (with the use of cache memory). While deterministic
finite automata (DFAs) implementations of regular expressions
take only one main memory accesses per byte, they often
require very large memory space to store their transition
tables, which undermines their scalability in real applications.
Therefore, conventional DFA and NFA are not ideal in real
systems.
Recent research efforts have been focused on reducing the
memory storage requirement of DFAs, and they can be
divided into the following categories: (1) reducing the number
of states [1], [9], [10], (2) reducing the number of transitions [2],
(3) reducing the bits encoding the transitions [3], [11], and
(4) reducing the character-set [12]. Unfortunately, all of these
approaches compress DFAs at the cost of increased main
memory accesses. The amount of compression in transition
reduction and character-set reduction is bounded by the size
of the character-set (e.g., the maximum reduction is
if
ASCII is used) due to the fact that there is at least one transition
in each state. We focus on state reduction, which is not limited
by the maximum reduction ratio of 256, and we manage to
reduce the storage size of DFAs by up to 4 orders of magni-
tude in our experiment. Moreover, our approach can be
incorporated into the other approaches to achieve further
memory reduction.
This paper proposes a novel state reduction solution, called
deterministic finite automata with extended character-set (DFA/
EC). We first introduce DFA/EC as a general model of DFA.
This general model removes part of each DFA state and
incorporates it with the next input character. This results in
an extended the set of input characters. However, simply
•
C. Liu and Y. Pan are with Sun Yat-sen University, Guangzhou 510006,
China. E-mail: panyan5@mail.sysu.edu.cn. (corresponding author: Y. Pan.)
•
A. Chen Shenzhen Institutes of Advanced Technology, Chinese Academy of
Sciences.
•
J. Wu is with the Temple University, Philadelphia, PA 19122.
Manuscript received 14 Mar. 2012; revised 27 Oct. 2012; accepted 16 Apr. 2013.
Date of publication 18 Apr. 2013; date of current version 15 July 2014.
Recommended for acceptance by H. Shen.
For information on obtaining reprints of this article, please send e-mail to:
reprints@ieee.org, and reference the Digital Object Identifier below.
Digital Object Identifier no. 10.1109/TC.2013.93
IEEE TRANSACTIONS ON COMPUTERS, VOL. 63, NO. 8, AUGUST 2014 1925
0018-9340 © 2013 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功