没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
Two efficient quantum private comparison (QPC) protocols are proposed, employing single photons and collective detection. In the proposed protocols, two distrustful parties (Alice and Bob) compare the equivalence of information with the help of a semi-honest third party (TP). Utilizing collective detection, the cost of practical realization is reduced greatly. In the first protocol, TP gains the result of the comparison. While in the second protocol, TP cannot get the comparison result. In both
资源推荐
资源详情
资源评论

Efficient quantum private comparison employing single photons and
collective detection
Bin Liu, Fei Gao, Heng-yue Jia, Wei Huang, Wei-wei Zhang, Qiao-yan Wen
abstract
Two efficient quantum private comparison (QPC) protocols are proposed, employing single
photons and collective detection. In the proposed protocols, two distrustful parties (Alice and Bob)
compare the equivalence of information with the help of a semi-honest third party (TP). Utilizing
collective detection, the cost of practical realization is reduced greatly. In the first protocol, TP
gains the result of the comparison. While in the second protocol, TP cannot get the comparison
result. In both of our protocols, Alice and Bob only need be equipped with unitary operation
machines, such as phase plates. So Alice and Bob need not to have the expensive quantum devices,
such as qubit generating machine, quantum memory machine and quantum measuring machine.
Security of the protocols is ensured by theorems on quantum operation discrimination.
Keywords: quantum private comparison, single photons, collective detection
1. Introduction
Along with the rapid development of quantum mechanics in recent years, more and more
attentions are paid to the applications of quantum mechanics in communication, such as quantum
information and quantum cryptography. Since Bennett and Brassard designed the first quantum
cryptographic protocol [1] in 1984, various quantum cryptographic protocols have been proposed,
such as quantum key distribution [2-10], quantum coin flipping [11-13], quantum secure
multiparty computation (QSMC) [14-21] and so on.
Secure multiparty computing (SMC), also called secure function evaluation, has been
extensively studied in classical cryptography. Private comparison is an important branch of SMC,
which allows two participants to determine whether they own the same secrets without disclosing
their secrets. Based on the millionaires' problem presented by Yao in 1982 [22], in which two
millionaires determine who is richer without knowing each others' actual property, Boudot
proposed a private comparison protocol [23] used to determine whether two millionaires are
equally rich . However, the security of classical private comparison protocols relies on the
computation complexity, which is susceptible to the strong ability of quantum computation. In fact,
Lo pointed out that it is impossible to construct a secure equality function in a two-party scheme
[24].

Quantum private comparison (QPC) is an attractive application of quantum mechanics. With
the help of a third party (TP), QPC allows two parties (Alice and Bob) to check whether their
secrets are equal without disclosing any information about their secrets. As opposed to classical
private comparison, the security of QPC does not rely on computational assumptions but simply
on the laws of physics such as Heisenberg uncertainty principle and quantum no-cloning theorem.
Yang et al. designed the first QPC protocol [25]. Since then many QPC protocols have been
proposed [26-30]. Most of them employ entangled states [25, 27-30]. In all of the previous QPC
protocols, TP is limited to be semi-honest. A semi-honest TP is a party who always follows the
procedure of the protocol. He/she will take a record of all intermediate computations, and will not
be corrupted by an outside eavesdropper. However, he/she might try to steal the information from
the record. What's more, in all these protocols, detection is taken in every step of the particles'
transmission. However, this detection strategy which is called as the step-by-step detection makes
these protocols intricate and inefficient. On the other hand, the action of detection always requires
the participant to have quantum devices, e.g., the qubit generating machine, or the quantum
memory, or the quantum measuring machine. Considering that these devices are expensive in the
practical situation, it is unrealistic that every participant is equipped with all these quantum
devices. Therefore, QPC protocols would be more efficient and easier to achieve if the detection is
taken after the whole process of the particle transmission, i.e. the collective detection.
In this paper, we propose two QPC protocols employing single photons and collective
detection, which is more efficient and easier to realize than the previous QPC protocols. More
details on the proposed protocols and the security analysis are discussed in later sections. Section
2 describes the two protocols. The security is analyzed in Section 3. Finally, a short conclusion is
given in Section 4.
2. The proposed QPC protocols employing single photons and
collective detection
In this section, two efficient QPC protocols are described in steps. In the first protocol, TP
learns the result of the comparison. While in the second protocol, TP has no idea of the
comparison result. In both the two protocols, Alice and Bob only need be equipped with phase
plates. Here is our first QPC protocol (See Fig 1.).
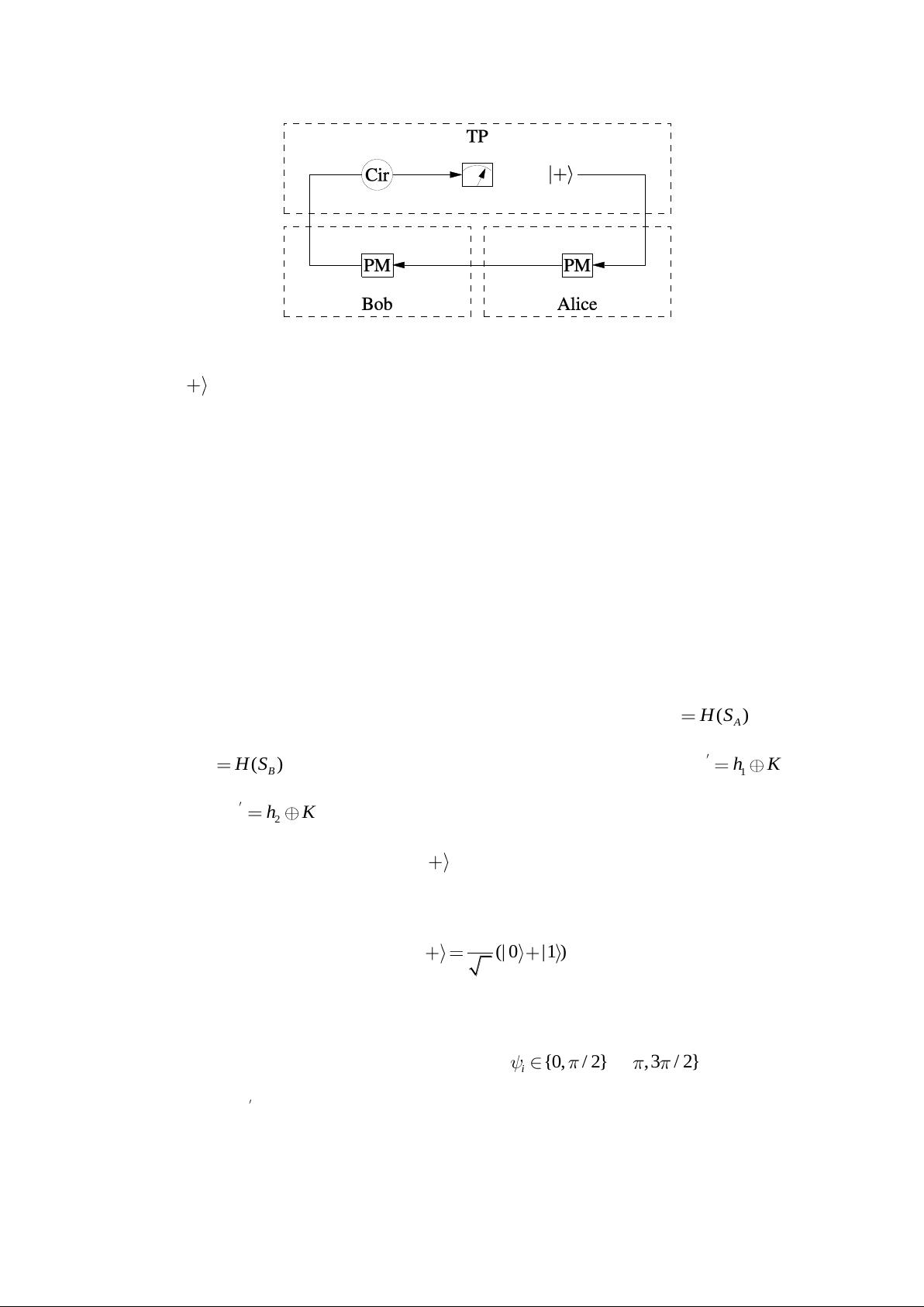
Fig.1. The simple diagram of Protocol I. Cir, circulator; PL, phase plate. TP generates photons in
state
|
and sends them to Alice. After the encoding action by applying different phase shifts,
Alice sends them to Bob. Bob also applies phase shifts on the photons and sends them back to TP.
When TP receives the photons Bob sends to him/her, he/she stores them in the circulator. After
Alice and Bob publish their phase shifts or classical bits, TP chooses the correct basis to measure
the states stored in the circulator.
1. Alice and Bob generate an
n
-bit secret key
K
with the help of TP by executing a
three-party QKD protocol with an honest center designed by Shil et al. [8] and improved
by us [9, 10]. (In our improved three-party protocol with an honest center, Alice and Bob
encode their secret by performing unitary operation on the single photon they receive. So
Alice and Bob only need be equipped with phase plates. See the Appendix.)
2. Alice and Bob compute the
n
-bit hash values of their secrets,
1
()
A
h H S
and
2
()
B
h H S
, respectively. Then Alice and Bob calculate the bit strings
11
h h K
and
22
h h K
.
3. TP generates
n
photons in state
|
and sends this sequence (denoted as
Q
) to Alice.
Here
1
| (|0 |1 )
2
. (1)
4. When Alice receives the
i
-th photon in sequence
Q
, she uses a tilt-adjustable phase
plate to apply a randomly selected phase shift
{0, / 2}
i
(
{ ,3 / 2}
) if the
i
-th
bit in
1
h
is 0 (1) [31]. The state of the
i
-th photon in
Q
after Alice's operation is
剩余13页未读,继续阅读
资源评论

weixin_38653687
- 粉丝: 3
- 资源: 973
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 基于cruise的燃料电池功率跟随仿真,按照丰田氢能源车型搭建,在wltc工况下跟随效果好,最高车速175,最大爬坡30,百公里9s均已实现 1.模型通过cruise simulink联合仿真,策略
- C#源码 上位机 联合Visionpro 通用框架开发源码,已应用于多个项目,整套设备程序,可以根据需求编出来,具体Vpp功能自己编 程序包含功能 1.自动设置界面窗体个数及分布 2.照方式以命令触
- 程序名称:悬架设计计算程序 开发平台:基于matlab平台 计算内容:悬架偏频刚度挠度;螺旋弹簧,多片簧,少片簧,稳定杆,减震器的匹配计算;悬架垂向纵向侧向力学、纵倾、侧倾校核等;独立悬架杠杆比,等效
- 华为OD+真题及解析+智能驾驶
- jQuery信息提示插件
- 基于stm32的通信系统,sim800c与服务器通信,无线通信监测,远程定位,服务器通信系统,gps,sim800c,心率,温度,stm32 由STM32F103ZET6单片机核心板电路、DS18B2
- 充电器检测9-YOLO(v5至v11)、COCO、Create充电器检测9L、Paligemma、TFRecord、VOC数据集合集.rar
- 华为OD+考试真题+实现过程
- 保险箱检测51-YOLO(v5至v11)、COCO、CreateML、Paligemma、TFRecord、VOC数据集合集.rar
- 五相电机邻近四矢量SVPWM模型-MATLAB-Simulink仿真模型包括: (1)原理说明文档(重要):包括扇区判断、矢量作用时间计算、矢量作用顺序及切时间计算、PWM波的生成; (2)输出部分仿
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功