
An Attribute Based Access Control Model with
POL Module for Dynamically Granting and
Revoking Authorizations
Gang Liu, Huimin Song, Can Wang, Runnan Zhang, Lu Fang
Abstract—Currently, resource sharing and system security are
critical issues. This paper proposes a POL module composed of
PRIVILEGE attribute (PA), obligation and log which improves
attribute based access control (ABAC) model in dynamically granting
authorizations and revoking authorizations. The following describes
the new model termed PABAC in terms of the POL module
structure, attribute definitions, policy formulation and authorization
architecture, which demonstrate the advantages of it. The POL
module addresses the problems which are not predicted before and
not described by access control policy. It can be one of the subject
attributes or resource attributes according to the practical application,
which enhances the flexibility of the model compared with ABAC.
A scenario that illustrates how this model is applied to the real world
is provided.
Keywords—Access control, attribute based access control, granting
authorizations, privilege, revoking authorizations, system security.
I. INTRODUCTION
A
CCESS control [1] is a technology used in almost every
system, such as a computer system or an enterprise
management system. It permits legally authorized subjects
to access protected resources; prohibits legal subjects from
unauthorized access to protected resources; prevents illegal
subjects from accessing protected resources. Nowadays, the
mainstream access control models are mandatory access
control (MAC) [2], discretionary access control (DAC) [3],
role based access control (RBAC) [4], task based access
control (TBAC) [5] and attributed based access control
(ABAC) [6].
Many researchers have investigated ABAC model, which
is applied in web service, cloud computing, collaborative
environment and so on. Reference [7] utilizes the characteristic
that security information is spread over a number of attribute
and policy authorities in ABAC model and compares ABAC
model with RBAC model to further elaborate on the
advantages of ABAC model. Reference [8] takes advantage
of the characteristic that policy authorization based attributes
can protect the user privacy. In [9], the access control policies
are made based the users previous behavior. The much
contribution a user makes, the more permission he or she
is granted. ABAC is not only applied in different fields but
also more flexible than other access control models. ABAC
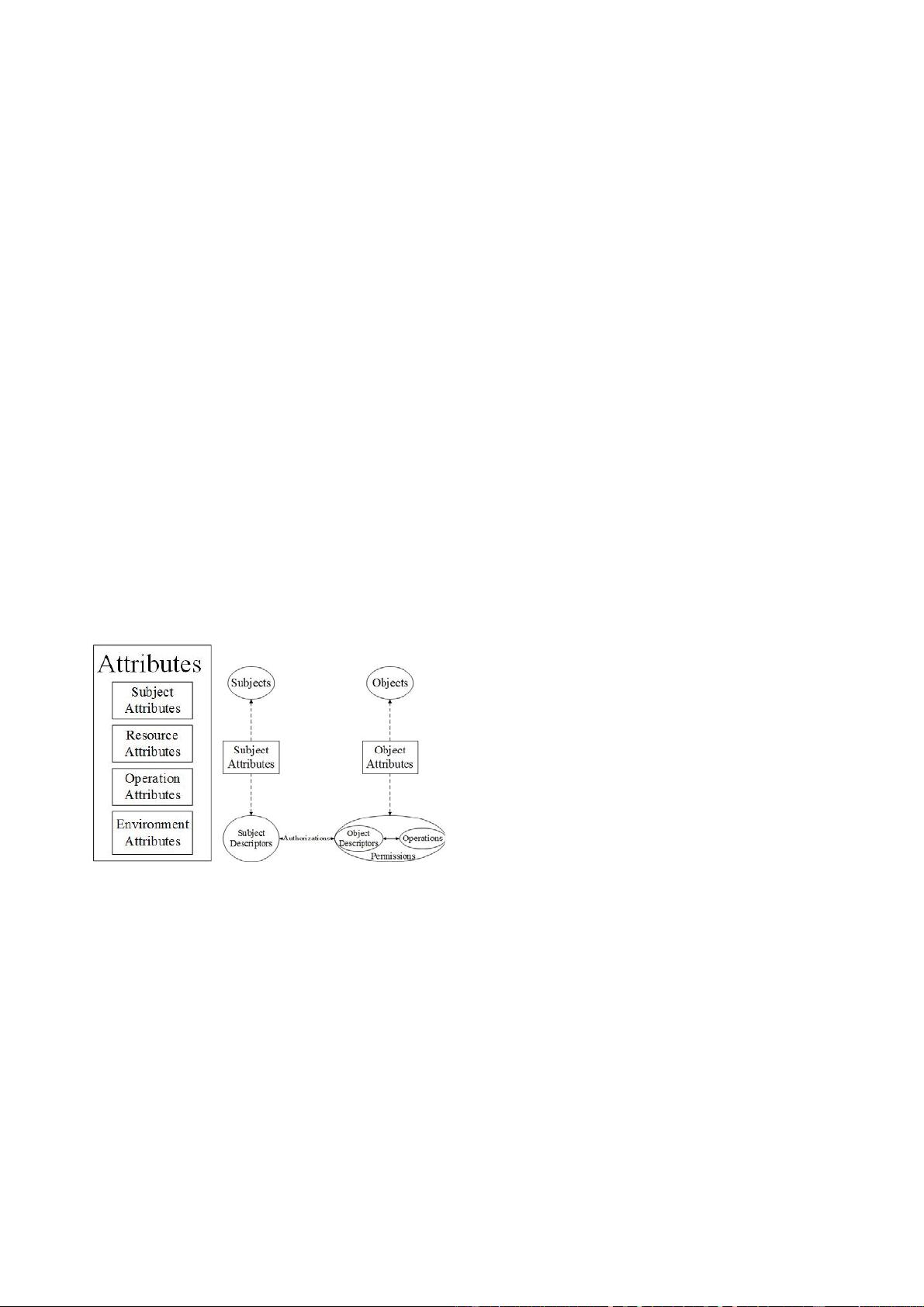
describes the subject, resource, operation and environment
Huimin Song is with the School of Computer Science and Technology,
XIDIAN University, Xi’an, 710071 China (corresponding author, e-mail:
gliu
xd@163.com).
Gang Liu, Can Wang, Runnan Zhang, Lu Fang are with XIDIAN University.
with attributes. Each attribute is defined according to the
practical application which improves the flexible of ABAC
model. ABAC makes the access control policies based one
or more attributes and evaluates the value of them to judge
whether the subject can access the resource or not. That is to
say, the subject can access the resource only through parts of
his or her attributes which is different from the other access
control models and protects the subject privacy. Besides, the
way of authorization based attributes in ABAC model also
achieves large-scale authorization and the policies can be
modified dynamically.
However, though ABAC model has many merits in
application, it is also necessary to take revoking authorization
flexibly into consideration. If the authorization cannot be
revoked in time, it may carry significant security risks to the
system. In the real world, a lot of authorizations are used only
once or several times. If these authorizations are stored in the
policy repository not revoked for a long time, the problem of
the policy repository explosion and policy conflict may occur.
Thus, how to revoke the authorizations in time is the research
contents in this paper.
This paper proposes a POL module and combines it with
ABAC model, termed PABAC model. PABAC is also based
on attributes, including subject attribute, resource attribute,
operation attribute and environment attribute. The environment
attribute has been used to judge the current situation state
of the system. POL module is composed of PRIVILEGE
attribute (PA), obligation and log. POL module can be one
of the subject attributes or resource attributes. This paper
takes the POL module as one of the resource attributes as an
example to illustrate the structure of PABAC. Due to it, each
resource has been managed by the only one subject, termed
PRIVILEGE manager (PM). However, a PM manages one
or more resources and has the permission to modify the
PA value of these resources. When the environment attribute
detects that the current system state is abnormal, POL module
allows the PM to authorize based one or more subject attributes
with modifying the PA. Once the subject has been authorized
access, the subject executes the obligation before or after
the authorized access. Thus, obligation is used to revoke the
PRIVILEGE directly or gives the information feedback of
the authorized access. The PA can also be used to address
the problems including the unforeseeable problem and the
problem not described by access control policies. That is
to say, PABAC makes use of the PA to authorize access
and the obligation to revoke it which achieves granting and
World Academy of Science, Engineering and Technology
International Journal of Computer and Information Engineering
Vol:11, No:6, 2017
759International Scholarly and Scientific Research & Innovation 11(6) 2017 scholar.waset.org/1307-6892/10007354
International Science Index, Computer and Information Engineering Vol:11, No:6, 2017 waset.org/Publication/10007354


 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功