无线人体传感器网络的模式调节器
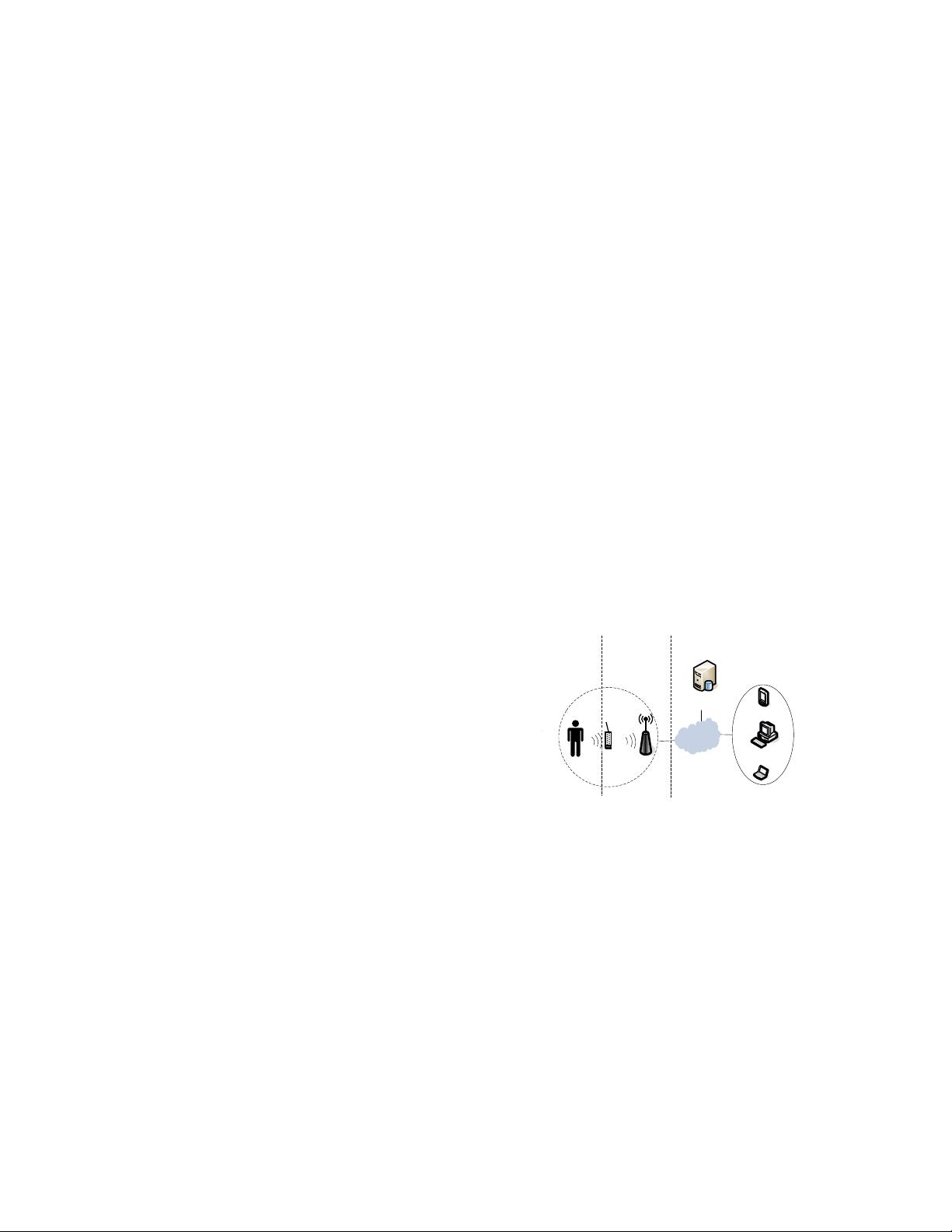
摘要—在无线人体区域传感器网络(WBAN)中,生物传感器被植入或穿戴在个人身上以获取用于临床诊断或物理监测的医学数据。 传统上,身份验证和加密技术是用于实现WBAN系统的数据机密性和隐私性。 但是,对于WBAN系统,除了数据本身之外,数据传输的模式还可能泄漏有关用户的关键信息。 例如,各种医疗传感器以不同的模式传递数据,这些模式泄漏了许多关键事实,例如,使用了什么传感器(这意味着个人可能患有疾病)以及传感器采样的频率(这意味着某些异常观察的紧急程度)关于一个病人)。 在这项工作中,为了应对这一挑战,我们设计了一个调节器,该调节器将实际数据会话打包到传输层中与类型无关的传输模型中。 所有有效数据包均以调节器定义的频率和相同长度平等发送,以使有效数据传输和传输的固有速度变得混乱。 其他参数。我们还提出了一种策略PAS,以最大程度地减少开销,同时防止攻击者找到患者所在的位置。 我们广泛的实验验证了我们的调节器和PAS设计。 ### 无线人体传感器网络的模式调节器 #### 摘要 随着生物计量传感器和移动计算技术的发展,一种称为无线人体区域传感器网络(Wireless Body Area Network, WBAN)的可穿戴医疗保健系统已被广泛应用于从个体收集并传输医学数据至数据中心。WBAN在疾病诊断与治疗中扮演着辅助角色,尤其是在慢性病患者或老年人群中,能够提升实时数据采集效率、降低成本及减少医院就诊次数。然而,在保障数据保密性和隐私性的传统方法如身份验证与加密技术之外,WBAN中的数据传输模式同样可能泄露关于用户的敏感信息。为解决这一问题,本文设计了一种模式调节器,该调节器能够在传输层将真实数据会话封装进一种类型无关的传输模型中,并通过统一的数据包频率与长度来混淆实际数据传输的固有节奏及其他参数。此外,还提出了一种策略(Pattern Anonymization Strategy, PAS),旨在最小化开销的同时阻止攻击者定位患者位置。 #### 引言 随着生物计量传感器技术和移动计算技术的进步,WBAN作为一种能够监测与记录个人生理数据并通过无线通信方式将数据传输至服务器的可穿戴健康护理系统,已经被广泛应用。此类数据在疾病的诊断与治疗过程中起着至关重要的辅助作用。特别是对慢性病患者和老年人来说,WBAN能够显著提高实时数据收集效率,减少医疗成本和医院就诊次数。近年来,许多关于WBAN在医疗保健领域的创新方法也相继问世。 然而,在WBAN系统中,除了数据本身之外,数据传输模式也可能泄露关键信息。例如,不同类型的医疗传感器会以不同模式发送数据,这些模式可能会暴露传感器的种类(这可能暗示患者患有某种疾病)以及传感器的采样频率(这反映了某个异常观察结果的紧急程度)。面对这些挑战,研究团队设计了一种模式调节器来解决这些问题。该调节器通过将实际数据会话封装到类型无关的传输模型中,确保所有有效数据包都按照预定义的频率和平等的长度进行传输,从而混淆了实际数据传输的速度和其他参数。此外,还提出了一种名为PAS(Pattern Anonymization Strategy)的策略,旨在最小化开销的同时防止攻击者确定患者的地理位置。 #### 关键知识点详解 **1. 无线人体区域传感器网络(WBAN):** - **定义**:WBAN是一种由可植入或可穿戴在个人身上的生物传感器组成的网络,用于收集医学数据以进行临床诊断或物理监测。 - **应用场景**:广泛应用于远程健康监护、运动训练监测、军事应用等多个领域。 - **优势**:能够提供连续的生理参数监控,提高诊断准确性,降低医疗成本。 **2. 数据传输模式的隐私风险:** - **传输模式**:指传感器数据的传输频率、数据包大小、传输时间间隔等特征。 - **隐私泄露**:不同类型的医疗传感器以特定的模式传输数据,攻击者可以通过分析这些模式推断出患者的健康状况、活动习惯等个人信息。 - **案例分析**:如果一个特定频率的信号持续出现,攻击者可能猜测到患者正在使用某类特定的医疗传感器,进而推测其健康状况。 **3. 模式调节器的设计:** - **目标**:通过改变数据传输模式来保护患者隐私。 - **实现方式**:将实际数据会话封装到一种类型无关的传输模型中,并确保所有有效数据包都以相同的频率和平等的长度发送,以此混淆实际数据传输的固有速度和其他参数。 - **优势**:有效避免了通过分析数据传输模式而泄露用户隐私的风险。 **4. Pattern Anonymization Strategy (PAS) 策略:** - **目的**:最小化额外开销,同时防止攻击者定位患者的具体位置。 - **实现原理**:通过对传输的数据进行适当的处理,如添加噪声、调整数据包的大小等,来掩盖患者的地理位置信息。 - **有效性验证**:通过广泛的实验验证了模式调节器和PAS策略的有效性。 #### 结论 无线人体区域传感器网络(WBAN)为医疗保健领域带来了革命性的变化,但在数据传输模式方面仍存在隐私泄露的风险。为了解决这一问题,研究人员设计了一种模式调节器,它通过改变数据传输模式来保护患者隐私。此外,还提出了一种名为PAS的策略,旨在最小化开销的同时防止攻击者确定患者的地理位置。这些研究成果不仅有助于提高WBAN的安全性和隐私保护水平,也为未来WBAN的应用提供了重要的参考价值。

剩余7页未读,继续阅读

- 粉丝: 3
- 资源: 922
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- java项目之图书馆借阅系统的设计与实现源代码.zip
- C++ 控制台模拟ATM自动取款机 程序设计课程期末实验项目,.zip
- PHP实现多服务器session共享之memcache共享中文最新版本
- (OC)MQTT信息收发
- Win7下配置ApachePHPMySQL中文最新版本
- MFC使用MSXML2解析XML文件.zip
- Python大作业封面.doc
- 2d956ffda1551121.png
- RuoYi-Vue3.7z
- rf-practice
- CentOS搭建LAMP平台Web控制面板管理中文最新版本
- 量产HX711电子秤采集模块全套资料 1.串口波特率19200; 2.上电后直接串口打印称重数据; 3.可以发指令校零传感器,读取称重数值; 4.默认使用的是40Kg的传感器,其它传感器需要重新修正参
- LAMP详解及源码编译安装过程中文最新版本
- 广州大学人工智能原理实验(一)代码包
- TWIG模板设计快速入门手册中文最新版本
- 数据库连接工具dbeaver ARM版本


 信息提交成功
信息提交成功