
Fei Z S, et al. Sci China Inf Sci October 2014 Vol. 57 102302:2
artificial noise. Considering cooperative communication employing relays, ref. [13] established the utility
of cooperation for secret communication and derived an outer-bound on the optimal rate-equivocation
region based on a four-terminal relay-eavesdropper channel. In [14], the optimization of cooperative
jamming (CJ) was examined to enhance the physical-layer security of a wiretap fading channel via
distributed relays. In addition, He et al. [15] provided a secrecy rate region with an untrusted relay.
This paper is focused on a two-user interference channel with confidential messages (IFC-CM) where
each receiver is to decode its own message but could eavesdrop the message intended for the other user.
Ref. [16] presented the achievable secrecy rate region and an outer bound for the IFC-CM, while ref. [17]
derived the inner and the outer bounds of a one-sided IFC-CM and analyzed their gap. For a K-user
time-varying Gaussian IFC with secrecy constraints, ref. [18] revealed that a nonzero secure degree of
freedom (DoF) can be achieved by using an interference alignment scheme with secrecy precoding at
each transmitter. Additionally, ref. [19] investigated the K-user Gaussian many-to-one IFC in which the
achievable secrecy sum-rate over all users was proved to be achievable by using nested lattice codes.
To summarize, progress is being made from the information-theoretic perspective regarding secure (or
secret) communication channels. However, optimization in signal processing for delivering secret com-
munications is much less understood, which has motivated us to address the beamforming optimization
problem for the two-user Gaussian multiple-input single-output (MISO) IFC-CM in this paper. Recently,
for the two-user symmetric IFC-CM without multiple antennas, ref. [20] has studied the power control
problem and artificial noise parameter optimization for both the max-min point and the single-user point.
As for the two-user MISO IFC-CM, ref. [21] characterized the Pareto boundary of the secrecy rate region
by a parameterization based on maximal-ratio combining (MRC) and zero-forcing (ZF) beamformers
and further showed the existence and uniqueness of the Nash equilibrium (NE), which is similar to the
traditional IFC without secrecy consideration [22]. Moreover, for MIMO Gaussian IFC-CM, ref. [23]
illustrated a game-theoretic approach to permit the transmitters to compromise on an operating point
which balanced the network performance.
The secrecy model of our work is greatly motivated by the downlink scenario where two base stations
(BSs) communicate with two local mobile stations (MSs) simultaneously on the same radio channels but
each MS may be a threat to decode the message intended for the other MS. This network model is a
step-up of the conventional downlink channel by allowing coordination between two trusted BSs which are
electrically connected by a fiber network but do not permit data sharing to minimize processing overhead
and complexity of the backhaul.
In this paper, we first show that artificial noise is unable to improve the secrecy rate performance for
the two-user MISO IFC-CM. Secondly, using the parameterization in [21] as a tool, we analyze specific
points on the Pareto-boundary of the secrecy rate region for the two-user MISO IFC-CM and then propose
methods to reach those points. Our emphasis is on secrecy-rate balancing which provides a secrecy-rate-
fair operating point and we achieve this by searching only a real-valued parameter in the feasible set.
The analysis is done assuming that the transmitters only know the channel covariance matrices (i.e.,
statistical CSI [24,25]). We derive the ergodic secrecy rates in closed form and obtain the beamforming
vectors corresponding to the Pareto-optimal ergodic secrecy rate points in this case.
Notations—Throughout the paper, vectors are written in boldface small letters while matrices are in
boldface capital letters. We use the superscripts (·)
∗
,(·)
T
and (·)
H
to denote, the complex conjugate,
transpose and Hermitian transpose operations, respectively. An identity matrix is denoted by I.The
matrix Π
X
X(X
H
X)
−1
X
H
represents the orthogonal projection onto the column space of X,and
Π
⊥
X
I − Π
X
gives the orthogonal complement of the column space of X.Also,v(A, B) denotes the
principal generalized eigenvector corresponding to the largest generalized eigenvalue.
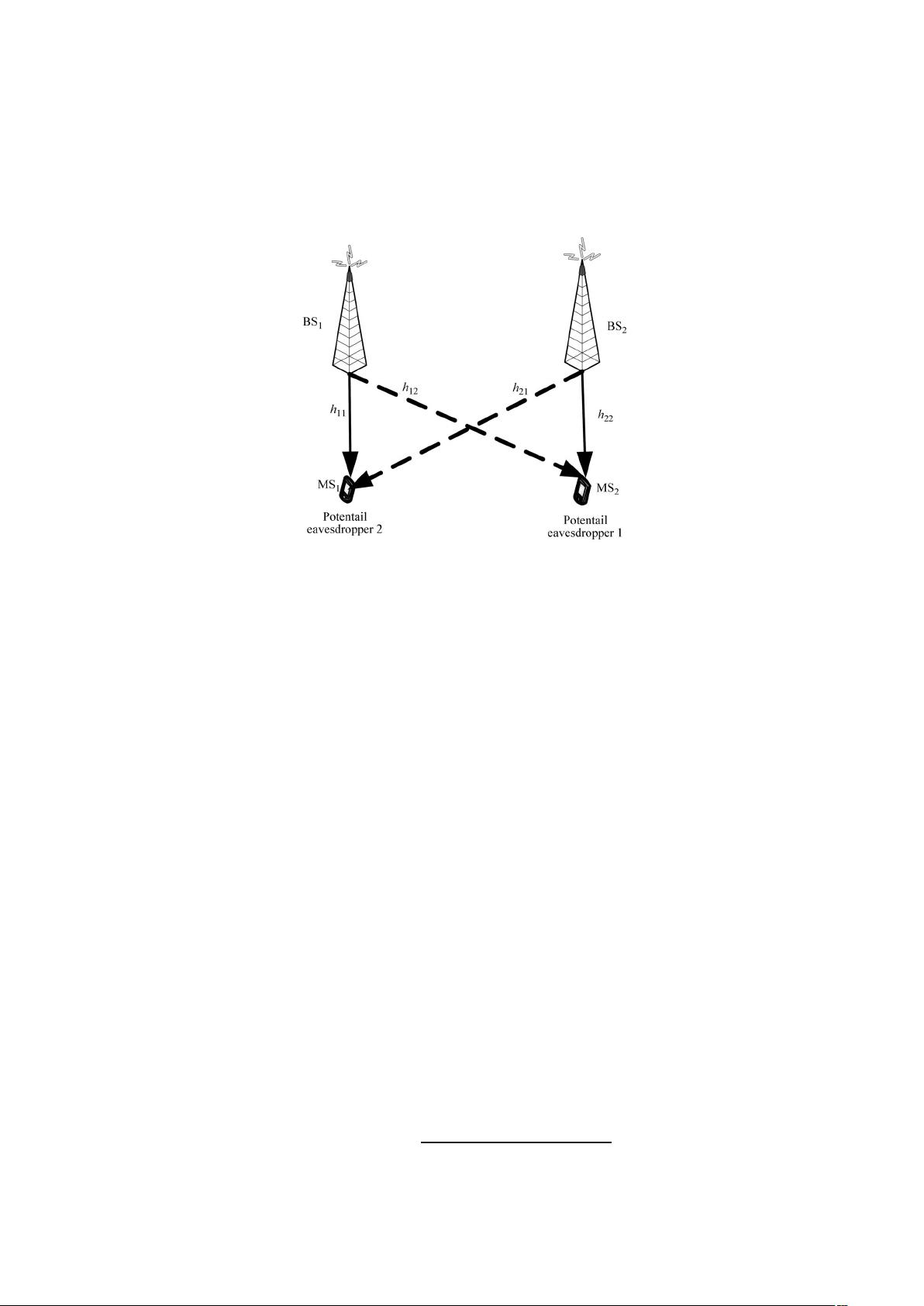
2Systemmodel
We consider a two-user MISO IFC-CM which is motivated by a downlink cellular network with two
multi-antenna BSs each transmitting to one desirable MS. We assume that the message sent by each BS



 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功