没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
Perceptual hashing is a promising solution to image content authentication. However, conventional image hash algorithms only offer a limited authentication level for the protection of overall content. In this work, we propose an image hash algorithm with block level content pro- tection. It extracts features from DFT coefficients of image blocks. Ex- periments show that the hash has strong robustness against JPEG com- pression, scaling, additive white Gaussian noise, and Gaussian smooth- ing. The hash value is compact, and highly dependent on a key. It has very efficient trade-offs between the false positive rate and the true pos- itive rate
资源推荐
资源详情
资源评论
HAL Id: hal-01596205
https://hal.inria.fr/hal-01596205
Submitted on 27 Sep 2017
HAL is a multi-disciplinary open access
archive for the deposit and dissemination of sci-
entic research documents, whether they are pub-
lished or not. The documents may come from
teaching and research institutions in France or
abroad, or from public or private research centers.
L’archive ouverte pluridisciplinaire HAL, est
destinée au dépôt et à la diusion de documents
scientiques de niveau recherche, publiés ou non,
émanant des établissements d’enseignement et de
recherche français ou étrangers, des laboratoires
publics ou privés.
Distributed under a Creative Commons Attribution| 4.0 International License
A Secure Perceptual Hash Algorithm for Image Content
Authentication
Li Weng, Bart Preneel
To cite this version:
Li Weng, Bart Preneel. A Secure Perceptual Hash Algorithm for Image Content Authentication.
Bart Decker; Jorn Lapon; Vincent Naessens; Andreas Uhl. 12th Communications and Multimedia
Security (CMS), Oct 2011, Ghent, Belgium. Springer, Lecture Notes in Computer Science, LNCS-
7025, pp.108-121, 2011, Communications and Multimedia Security. <10.1007/978-3-642-24712-5_9>.
<hal-01596205>

A Secure Perceptual Hash Algorithm for Image
Content Authentication
Li Weng and Bart Preneel
⋆
Katholieke Universiteit Leuven, ESAT/COSIC-IBBT
li.weng@esat.kuleuven.be,bart.preneel@esat.kuleuven.be
Abstract. Perceptual hashing is a promising solution to image content
authentication. However, conventional image hash algorithms only offer
a limited authentication level for the protection of overall content. In this
work, we propose an image hash algorithm with block level content pro-
tection. It extracts features from DFT coefficients of image blocks. Ex-
p eriments show that the hash has strong robustness against JPEG com-
pression, scaling, additive white Gaussian noise, and Gaussian smooth-
ing. The hash value is compact, and highly dependent on a key. It has
very efficient trade-offs between the false positive rate and the true pos-
itive rate.
1 Introduction
In the Internet era, images are massively produced and distributed in digital
form. Although digital images are easy to store and pro cess, they are also sus-
ceptible to malicious modification. Due to widely available image editing soft-
ware, even non-professionals can perform content modification. Consequently,
people begin to suspect what they see from digital images. Sometimes, public
incidents happen, due to fake images. Therefore, the need for protecting content
authenticity is emerging.
Among various techniques, perceptual hashing is a promising solution. Hash-
ing means to compute a digest value from data. This digest value, typically a
short binary string, is called a hash value. Perceptual hash algorithms are a
particular kind of hash algorithms for multimedia data. They have the special
property that the hash value is dependent on the multimedia content, and it re-
mains approximately the same if the content is not significantly modified. Since a
⋆
This work was supported in part by the Concerted Research Action (GOA) AM-
BioRICS 2005/11 of the Flemish Government and by the IAP Programme P6/26
BCRYPT of the Belgian State (Belgian Science Policy). The first author was sup-
p orted by the IBBT/AQUA project. IBBT (Interdisciplinary Institute for Broad-
Band Technology) is a research institute founded in 2004 by the Flemish Govern-
ment, and the involved companies and institutions (Philips, IPGlobalnet, Vital-
sys, Landsbond onafhankelijke ziekenfondsen, UZ-Gent). Additional support was
provided by the FWO (Fonds Wetenschappelijk Onderzoek) within the project
G.0206.08 Perceptual Hashing and Semi-fragile Watermarking.
perceptual hash value is a compact representation of the original content, it can
be used for robust content authentication. Compared with conventional crypto-
graphic hash algorithms [1], perceptual hash algorithms have the advantage that
they can tolerate the difference in quality and format – the binary representation
no longer matters; the same content always maps to the same hash value. This
is particularly useful for the multimedia domain.
In this work, we focus on image content authentication by perceptual hash
algorithms. In a typical application scenario, the authentic hash value is avail-
able; anyone who suspects the image can compute the hash value and compare
it with the authentic one (Fig. 1b). For example, the authentic hash value can
be published online, or electronically signed by digital signature techniques [1].
Although this application is known, there are some unsolved issues. In partic-
ular, there is the minor modification problem: when malicious modification is
perceptually insignificant, the hash algorithm is unable to distinguish it from
legitimate distortion. Most image hash algorithms compute the hash value from
an image’s global features. Since global features are not sensitive to local mod-
ification, these algorithms are generally vulnerable to the minor modification
problem, thus are not suitable for content authentication applications with high
security demand. In this work, a potential solution is provided. We propose an
image hash algorithm with the ability of authenticating image blocks.
The rest of the work is organized as follows: Section 2 introduces image hash-
ing and its limitation; Section 3 describes the proposed image hash algorithm;
Section 4 shows some experiment results; Section 5 concludes the work.
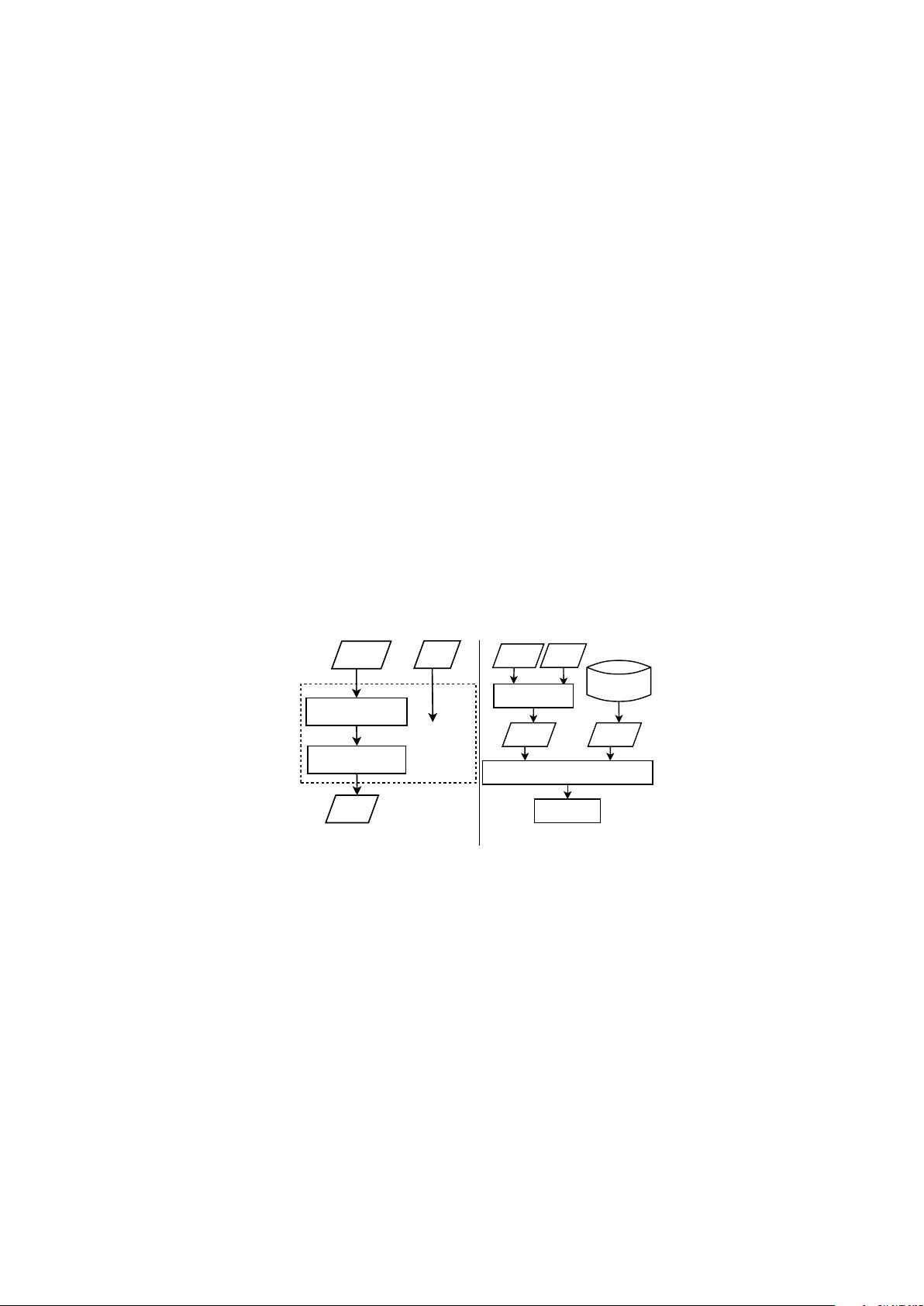
Feature extraction
Feature reduction
Hash
Image
Key
Randomization
Hash 2
Hash source
Hash 1
Similarity comparison
Decision
Key
Hash generation
Image
(a) Hash generation. (b) Hash comparison.
Fig. 1. Diagrams of perceptual hash generation (a) and comparison (b).
2 Perceptual Hashing and Its Limitation
The basic components of a perceptual hash algorithm are feature extraction,
feature reduction, and randomization (Fig. 1a). During feature extraction, ro-
bust features are extracted from the input signal. Typically, these features are
剩余14页未读,继续阅读
资源评论

wbxcww
- 粉丝: 3
- 资源: 6
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功