没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论

Errata Sheet for the Official (ISC)² Guide to the CISSP® CBK®
Error #1 -
Page 217, Question 15
Q. Which of the following is incorrect when considering privilege management?
a. Privileges associated with each system, service, or application, and the defined roles within
the organization to which they are needed, should be identified and clearly documented.
b. Privileges should be managed based on least privilege. Only rights required to perform a job
should be provided to a user, group, or role.
c. An authorization process and a record of all privileges allocated should be maintained.
Privileges should not be granted until the authorization process is complete and validated.
d. Any privileges that are needed for intermittent job functions should be assigned to multiple
user accounts, as opposed to those for normal system activity related to the job function.
Textbook Answer – B (Referenced on page 727)
Correction to text – After editor review, answer D is the correct answer since "privileges that are needed
for intermittent job functions should be assigned to a different user account, etc." Reference located on
page 123, last bullet on the page.
Error #2 -
Page 279, Question 20.
Q. Measures protected by steganography can be transmitted to:
a. Picture files
b. Music files
c. Video files
d. All of the above
Textbook Answer – C (Referenced on page 731)
Correction to text – After editor review, answer D is the correct answer.
Error #3 –
Incorrect Diagram
It has been brought to our attention that the figures labeled 3.7 and 3.8 on pages 242-243 are identical.
The correct figure for pg. 243 or Figure 3.8 is below:
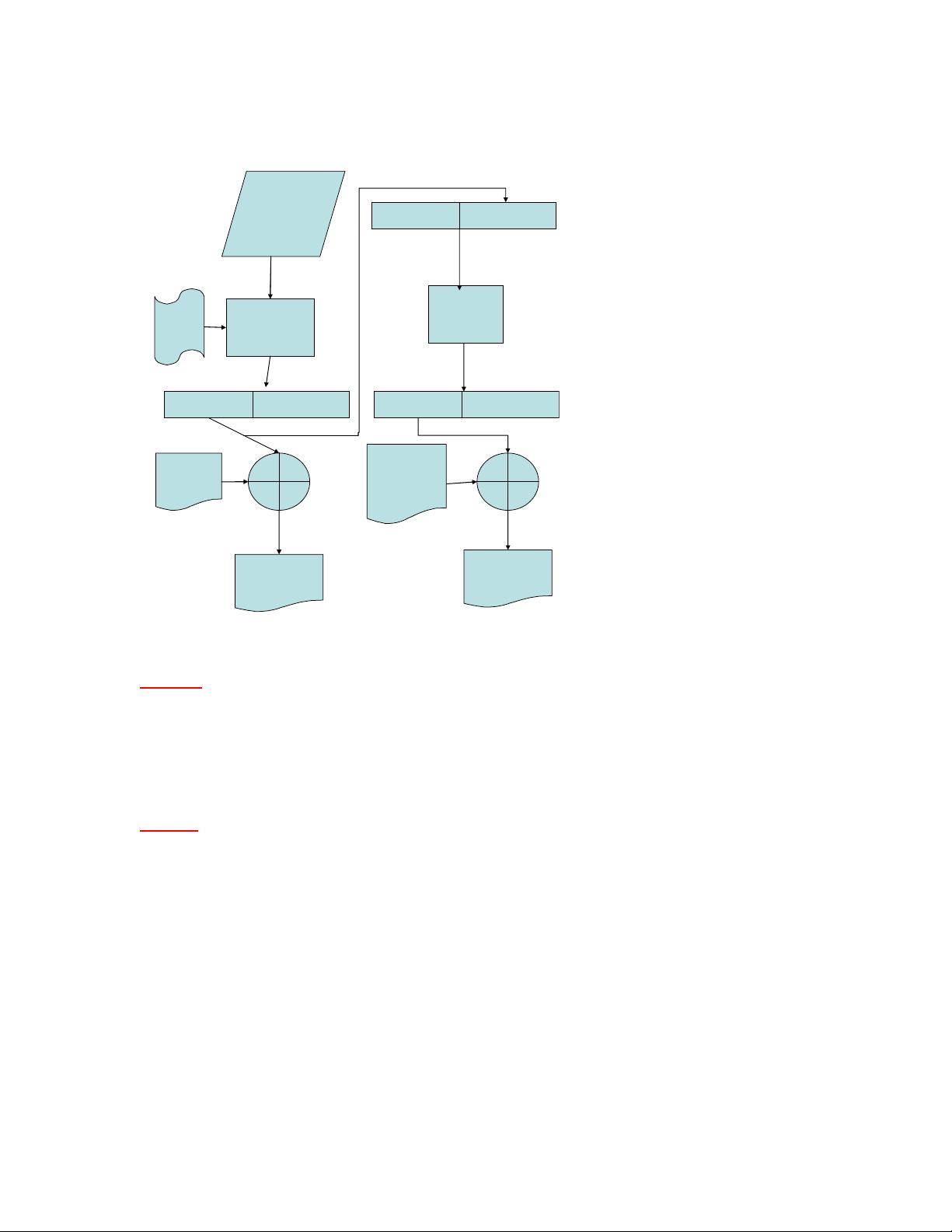
Initialization
Vector
loaded into
Shift Register
Key
DES
Algorithm
DES
Algorithm
Discard 64 - s bitsSelect s bitsDiscard 64 - s bitsSelect s bits
XOR
S bits of
Plaintext
Next s bits
of
Plaintext
XOR
Next S bits
of ciphertext
S bits of
ciphertext
s bits64 - sbits
Error #4
- Typo
On page 329, following the header of Trusted Computer Security Evaluation. The second line of this
paragraph states, “ITSEC defines four main levels (A, B, C, D)."
Correction to text – This sentence contains a typo and should read, “TCSEC defines four main levels (A,
B, C, D).”
Error #5
- Incorrect Listing of TCSEC
Page 329: The text lists the TCSEC levels as:
A Verified protection
A1 Verified design
B Mandatory protection
B3 Labeled security
B2 Structured protection
B1 Labeled security.
C Discretionary protection
C2 Discretionary protection
C1 Controlled access
Correction to text – It should state (corrections are bolded):
A Verified protection
A1 Verified design
剩余7页未读,继续阅读
资源评论

 x550022013-01-30挺一般的,有些断句。
x550022013-01-30挺一般的,有些断句。
Tlcf0168
- 粉丝: 0
- 资源: 1
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功