
1 典型配置案例 导读
H3C 防火墙典型配置案例集共包括 7 个文档,介绍了防火墙产品常用特性的典型配置案例,包含组
网需求、配置步骤、验证配置和配置文件等内容。
1.1
适用款型及软件版本
本手册所描述的内容适用于防火墙产品的如下款型及版本:
款型 软件版本
M9006/M9010/M9104 Version 7.1.051, Ess 9105
及以上
1.2
内容简介
典型配置案例中特性的支持情况与产品的款型有关,关于特性支持情况的详细介绍,请参见《H3C
SecPath M9000 多业务安全网关配置指导》和《H3C SecPath M9000 多业务安全网关 命令参考》。
手册包含的文档列表如下:
编号 名称
1
H3C 防火墙GRE over IPsec虚拟防火墙典型配置案例(V7)
2
H3C 防火墙IPsec典型配置案例(V7)
3
H3C 防火墙NAT444典型配置案例(V7)
4
H3C 防火墙NAT典型配置案例(V7)
5
H3C 防火墙堆叠冗余口应用典型配置案例(V7)
6
H3C 防火墙基于ACL包过滤策略的域间策略典型配置案例(V7)
7
H3C 防火墙基于对象策略的域间策略典型配置案例(V7)

H3C 防火墙 GRE over IPsec 虚拟防火墙
典型配置案例
Copyright © 2014 杭州华三通信技术有限公司 版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,
并不得以任何形式传播。本文档中的信息可能变动,恕不另行通知。

i
目 录
1 简介 ······················································································································································ 1
2 配置前提 ··············································································································································· 1
3 配置举例 ··············································································································································· 1
3.1 组网需求 ··············································································································································· 1
3.2 配置思路 ··············································································································································· 2
3.3 使用版本 ··············································································································································· 2
3.4 配置注意事项 ········································································································································ 2
3.5 配置步骤 ··············································································································································· 2
3.5.1 M9000 的配置 ···························································································································· 2
3.5.2 FW A的配置 ······························································································································· 6
3.5.3 FW B的配置 ······························································································································· 8
3.6 验证配置 ··············································································································································· 9
3.7 配置文件 ············································································································································· 12
1
1 简介
本文档介绍使用 GRE over IPSec 虚拟防火墙的配置案例。
2 配置前提
本文档不严格与具体软、硬件版本对应,如果使用过程中与产品实际情况有差异,请参考相关产品
手册,或以设备实际情况为准。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺
省配置。如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置
不冲突。
本文档假设您已了解 IPSec 特性。
3 配置举例
3.1
组网需求
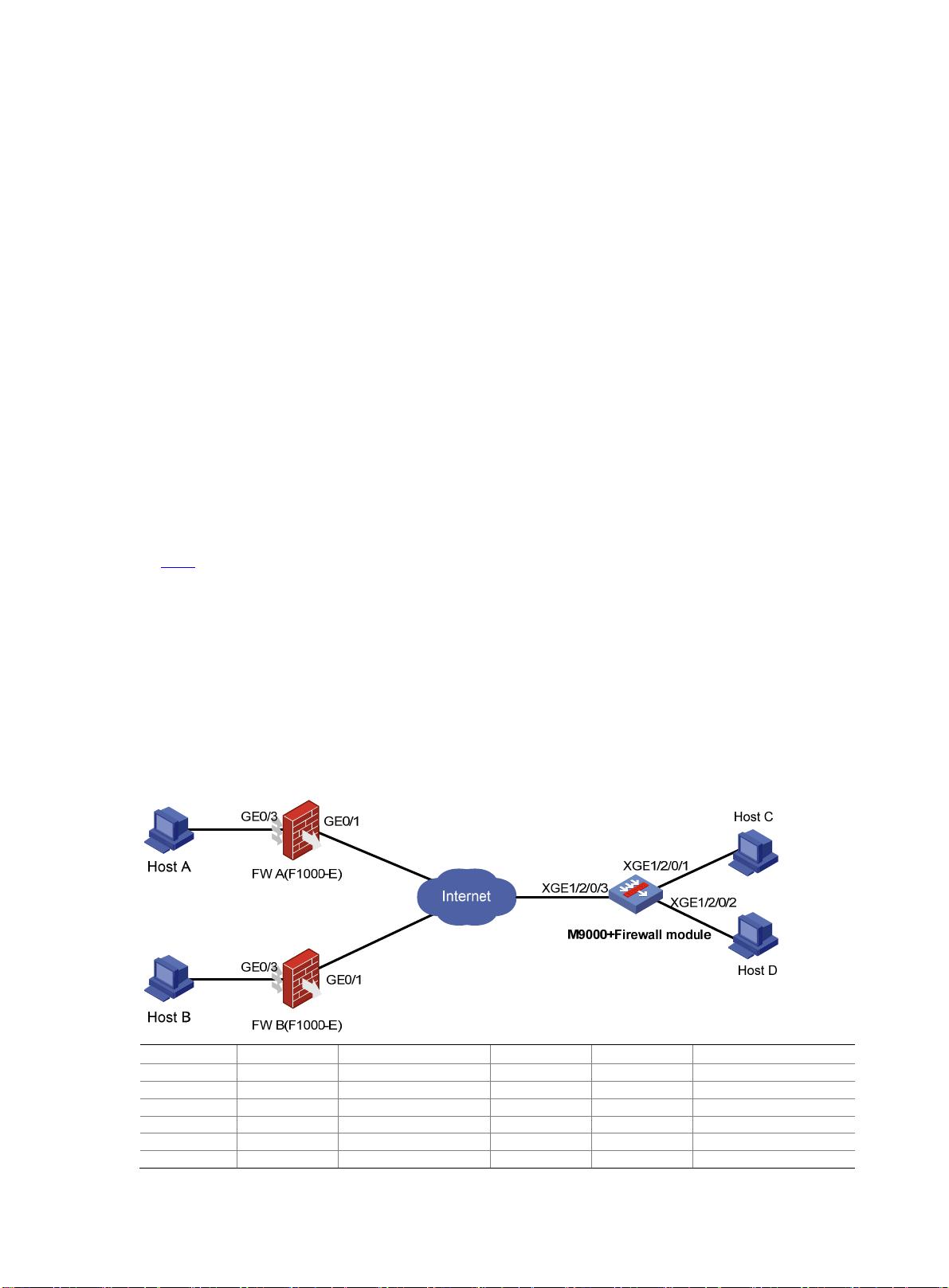
如 图 1 所示,Host A、Host B、Host C和Host D通过防火墙进行互访。Host C和Host D有相同的
内网地址,现要求:
• 在 M9000 和 FW A、FW B 之间建立 GRE over IPSec 隧道。在 M9000 上通过配置虚拟防火
墙实现网络及管理隔离。
• M9000 上有两个 GRE 隧道接口 Tunnel1 和 Tunnel2,分别属于不同的虚拟设备 vd_a、vd_b,
绑定对应虚拟设备的 VPN 实例实现路由隔离,其中 Tunnel1 绑定 vpn_a,Tunnel2 绑定 vpn_b。
Host A 访问 Host C 通过 Tunnel1 走虚拟设备 vd_a, Host B 访问 Host D 通过 Tunnel2 走虚
拟设备 vd_b。
图1 GRE over IPSec 虚拟防火墙组网图
设备 接口 IP地址 设备 接口 IP地址
FW A GE0/1 101.0.0.1/24 M9000 XGE1/2/0/1 10.0.3.1/24
GE0/3 10.0.1.1/24 XGE1/2/0/2 10.0.3.1/24
FW B GE0/1 102.0.0.1/24 XGE1/2/0/3 103.0.0.1/24
GE0/3 10.0.2.1/24 Host C - 10.0.3.2/24
Host A - 10.0.1.2/24 Host D - 10.0.3.2/24
Host B - 10.0.2.2/24

2
3.2
配置思路
• 为了使主机能够通过安全隧道互访,需要在防火墙之间创建隧道,并绑定相应的 VPN 实例。
• 在各个防火墙上配置 IPSec 安全提议及策略,并在对应出接口上进行应用。
3.3
使用版本
本文档基于 M9000 的 Version 7.1.051, Ess 9105 版本和 F1000-E 的 F3174P07 版本为例进行说明。
3.4
配置注意事项
• 在应用 VPN 实例的设备上,IPSec 保护的流,源 IP 和目的 IP 分别对应 Tunnel 口相应的源 IP
和目的 IP。
• 在应用 VPN 实例的设备上,如果要实现跨 VPN 实例的转发,要配置跨 VPN 实例的路由,并
且路由网关应为出接口下一跳地址。
3.5
配置步骤
3.5.1 M9000 的配置
(1) 创建 VPN 实例 vpn_a 和 vpn_b,并配置 RD 属性。
<Sysname> system-view
[Sysname] ip vpn-instance vpn_a
[Sysname-vpn-instance-vpn_a] route-distinguisher 1:1
[Sysname-vpn-instance-vpn_a] quit
[Sysname] ip vpn-instance vpn_b
[Sysname-vpn-instance-vpn_b] route-distinguisher 2:2
[Sysname-vpn-instance-vpn_b] quit
(2) 为接口 Ten-GigabitEthernet1/2/0/1、Ten-GigabitEthernet1/2/0/2、
Ten-GigabitEthernet1/2/0/3 配置 IP 地址,将 Ten-GigabitEthernet1/2/0/1、
Ten-GigabitEthernet1/2/0/2 分别绑定 vpn_a 和 vpn_b。
[Sysname] interface ten-gigabitethernet 1/2/0/1
[Sysname-Ten-GigabitEthernet1/2/0/1] ip binding vpn-instance vpn_a
[Sysname-Ten-GigabitEthernet1/2/0/1] ip address 10.0.3.1 255.255.255.0
[Sysname-Ten-GigabitEthernet1/2/0/1] quit
[Sysname] interface ten-gigabitethernet 1/2/0/2
[Sysname-Ten-GigabitEthernet1/2/0/2] ip binding vpn-instance vpn_b
[Sysname-Ten-GigabitEthernet1/2/0/2] ip address 10.0.3.1 255.255.255.0
[Sysname-Ten-GigabitEthernet1/2/0/2] quit
[Sysname] interface ten-gigabitethernet 1/2/0/3
[Sysname-Ten-GigabitEthernet1/2/0/3] ip address 103.0.0.1 255.255.255.0
[Sysname-Ten-GigabitEthernet1/2/0/3] quit
(3) 创建 Tunnel 1,绑定 VPN 实例并配置 IP 地址及 GRE Tunnel 参数。
[Sysname] interface Tunnel 1
[Sysname-Tunnel1] ip binding vpn-instance vpn_a



















