没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
安全的移动数据计费(mdc)对蜂窝网络至关重要 操作。它必须向正确的用户收取正确的音量 (s)他授权使用(即认证要求, 授权和会计(AAA)。在这项工作中,我们 蜂窝网络中mdc系统的安全性分析。我们发现 这三个漏洞在设计和实践中都可能被攻破,并识别出三个具体漏洞:认证绕过、授权欺诈和记帐量不准确。根本原因 蜂窝网络和互联网的技术基础 IP设计,以及轻率的实现。我们设计了三个 Showcase攻击证明,即使是简单的攻击也可以轻松渗透到正在运行的3G/4G蜂窝网络中。我们进一步 提出并评估防御方案。
资源推荐
资源详情
资源评论

Real Threats to Your Data Bills
– Security Loopholes and Defenses in Mobile Data Charging
Chunyi Peng
The Ohio State University
chunyi@cse.ohio-state.edu
Chi-Yu Li, Hongyi Wang, Guan-Hua Tu, Songwu Lu
University of California, Los Angeles
{lichiyu,hywang,ghtu,slu}@cs.ucla.edu
ABSTRACT
Secure mobile data charging (MDC) is critical to cellular network
operations. It must charge the right user for the right volume that
(s)he authorizes to consume (i.e., requirements of authentication,
authorization, and accounting (AAA)). In this work, we conduct
security analysis of the MDC system in cellular networks. We find
that all three can be breached in both design and practice, and iden-
tify three concrete vulnerabilities: authentication bypass, autho-
rization fraud and accounting volume inaccuracy. The root causes
lie in technology fundamentals of cellular networks and the Internet
IP design, as well as imprudent implementations. We devise three
showcase attacks to demonstrate that, even simple attacks can eas-
ily penetrate the operational 3G/4G cellular networks. We further
propose and evaluate defense solutions.
Categories and Subject Descriptors
C.2.0 [Computer-Communication Networks]: General—Se-
curity and protection; C.2.1 [Computer-Communication Net-
works]: Network Architecture and Design—Wireless Communi-
cation
Keywords
Cellular Networks; Mobile Data Services; Authentication, Autho-
rization, Accounting (AAA); attack; defense
1. INTRODUCTION
Mobile data services are getting increasingly popular, thanks to
the proliferation of smartphones and tablets, as well as the rapid
deployment of the third-generation/fourth-generation (3G/4G) cel-
lular networks. Global mobile data traffic grew 81% in 2013 and is
projected to increase 11-fold in the following five-year span [16].
This is contributed by 2.1 billion mobile Internet users world-
wide (by 2013 June), including 299 million 3G/4G broadband sub-
scribers (95% of inhabitants) in the US [25].
Convenient mobile data access does come with cost for users.
Most cellular operators charge mobile users based on their con-
sumed data volume [8, 32]. Mobile users pay for the data usage
Permission to make digital or hard copies of all or part of this work for personal or
classroom use is granted without fee provided that copies are not made or distributed
for profit or commercial advantage and that copies bear this notice and the full cita-
tion on the first page. Copyrights for components of this work owned by others than
ACM must be honored. Abstracting with credit is permitted. To copy otherwise, or re-
publish, to post on servers or to redistribute to lists, requires prior specific permission
and/or a fee. Request permissions from permissions@acm.org.
CCS’14, November 3–7, 2014, Scottsdale, Arizona, USA.
Copyright 2014 ACM 978-1-4503-2957-6/14/11 ...$15.00.
http://dx.doi.org/10.1145/2660267.2660346 .
at a preset price within certain volume cap, or in the pay-per-use
manner. For example, AT&T, a Tier-1 US carrier, charges $20 for
300MB per month for domestic access and about 2¢ per KB during
international travels [10]. This volume-based charging scheme is
not adopted without rationale. The radio spectrum is scarce and ex-
pensive (in spectrum licensing [20]), and wireless speed is bounded
by Shannon channel capacity. The explosive growth of mobile data
traffic further justifies the metered charging.
Undoubtedly, a well-designed and properly-operated mobile data
charging (MDC) system is critical to cellular networks. It not only
safeguards the multi-trillion revenue of global operators, but also
protects the monetary rights of billions of mobile users. To enable
metered charging, the key is to collect how much data is actually
used by which mobile user when (s)he agrees to. A secure MDC
should meet three requirements:
1. [Authentication] The user being billed for the given data
transfer must be the one who actually does the transfer.
MDC must authenticate the user who consumes the actual
data usage.
2. [Authorization] The data usage and its associated charge
should be with the user’s consent. A user should only pay
for those authorized data services, but not the spam from at-
tackers.
3. [Accounting volume] The volume should be accurate. The
recorded volume should be identical to that transferred at the
user device.
At first glance, it appears straightforward to meet the above re-
quirements. The MDC method is officially stipulated by the 3GPP
specification [3]. It is performed inside the cellular core network.
Whenever a data session is initiated with the mobile device, the
traffic from/to the mobile device traverses the cellular gateways
(akin to edge routers or switches in the Internet) to reach the des-
tination. The gateway counts the payload of observed data packets
for each mobile data session as the volume. It further associates
this volume with the user who initializes and uses this data ses-
sion. Given user authentication, the network is capable of inferring
who uses this data session. To prevent unauthorized access, cellu-
lar operators also deploy firewalls and network address translators
(NATs) to shield mobile devices from the traffic types of no inter-
est. While recent studies [21, 22, 27, 28, 36] have reported various
cases on accounting volume inaccuracy, the two aspects of authen-
tication and authorization still look bullet-proof. They seem almost
impossible to go wrong. Anyway, authentication and authorization
have been well studied in the security community, and their solu-
tions to cellular networks have been generally successful to date.
However, MDC is not as secure as anticipated. We discover that,
it is also vulnerable in authentication and authorization. Charging
actions may be taken upon the wrong user, or on data that the cellu-
Dimension Threat Loophole Attack Root Cause Defense solution
Authenti-
cation(§3.1)
A user is billed for
other’s data traffic.
Authentication
Bypass
Free-uplink-attack via IP
spoofing
No cross-layer secure
binding (§3.4)
Cross-layer secure binding
in the data plane(§4.1)
Authori-
zation(§3.2)
Unwanted data is
allowed and billed.
Authorization
Fraud
Cloak-and-dagger attacks
via MMS and IP spoofing
Network-based authorization; Explicit de-authorization on
demand in the control plane(§4.2)
IP push model (§3.4)
Accounting
volume(§3.3)
A user is billed for
data never received.
Accounting
Vol. Inaccuracy
Hit-but-no-touch
TTL-based attack
open-loop accounting; Feedback from the end/network;
Independent PS delivery(§3.4) explicit de-authorization(§4.2,§4.3)
Table 1: Summary of results.
lar user does not want. Consequently, all AAA components can be
breached in both technology and practice. The deployed defense
measures fail to protect them. Specifically, we identify three loop-
holes: authentication bypass, authorization fraud, and accounting
volume inaccuracy. All threats may impose real monetary loss to
the victim user(s).
Moreover, to our surprise, no sophisticated attack models are
needed. Simple attacks may work in operational 3G/4G cellular
networks! By significantly limiting the capability of the adver-
sary and applying variations of well-known attack methods (e.g., IP
spoofing), we have devised a few showcase attacks to test all three
AAA dimensions. All can pass the defense measures deployed by
cellular operators. The attacks can be against an individual or a
group of victims of any size, without requiring control or access to
the victim phone or the carrier. Our experiments further indicate
that the incurred charging damage exhibits no sign of limit.
We further analyze their root causes. They are beyond our initial
thoughts of being induced by implementation bugs from vendors
and imprudent practice by operators. Factors rooted in the technol-
ogy basics stipulated in the 3G/4G standards also share the respon-
sibility. They include lack of cross-layer secure binding in authen-
tication, network-based decision in authorization, and open-loop
operation and IP push delivery model in accounting. To fix these
loopholes, we further propose defense solutions, which apply three
guidelines of cross-layer security binding, coordinated control-
plane and data-plane operations for security, and infrastructure-
assisted end-user feedback.
Table 1 summarizes our main results. Before we delve into the
details, we rush to clarify what this work is not about. We exam-
ine the technical side of MDC security, but have not looked into
the issue of attack incentives. We focus on how (rather than why)
adversaries attack the system. While our proposed solution offers
one feasible approach, other alternatives (e.g., deterrence by detect-
ing and punishing attackers) are also possible as elaborated later.
Specifically, we make four following contributions:
• We uncover security threats in the MDC system, and confirm
that mobile users are vulnerable to unconstrained monetary loss.
• We expose and validate security loopholes in all three AAA
dimensions. We show that all AAA components can be breached
in both technology and operations. The deployed security mea-
sures fail to protect them.
• We further sketch novel attacks that exploit such loopholes
and validate them through experiments in operational 3G/4G cel-
lular networks.
• We deduce direct causes rooted in both the technology basics
and imprudent practice by operators. We propose and evaluate
defense solutions.
The rest of the paper is organized as follows. §2 introduces the
MDC background, the threat model and the experimental method-
ology. §3 elaborates our security analysis on each AAA dimension.
§4 proposes defense solutions and §5 evaluates them. §6 compares
with related work and §7 concludes the paper.
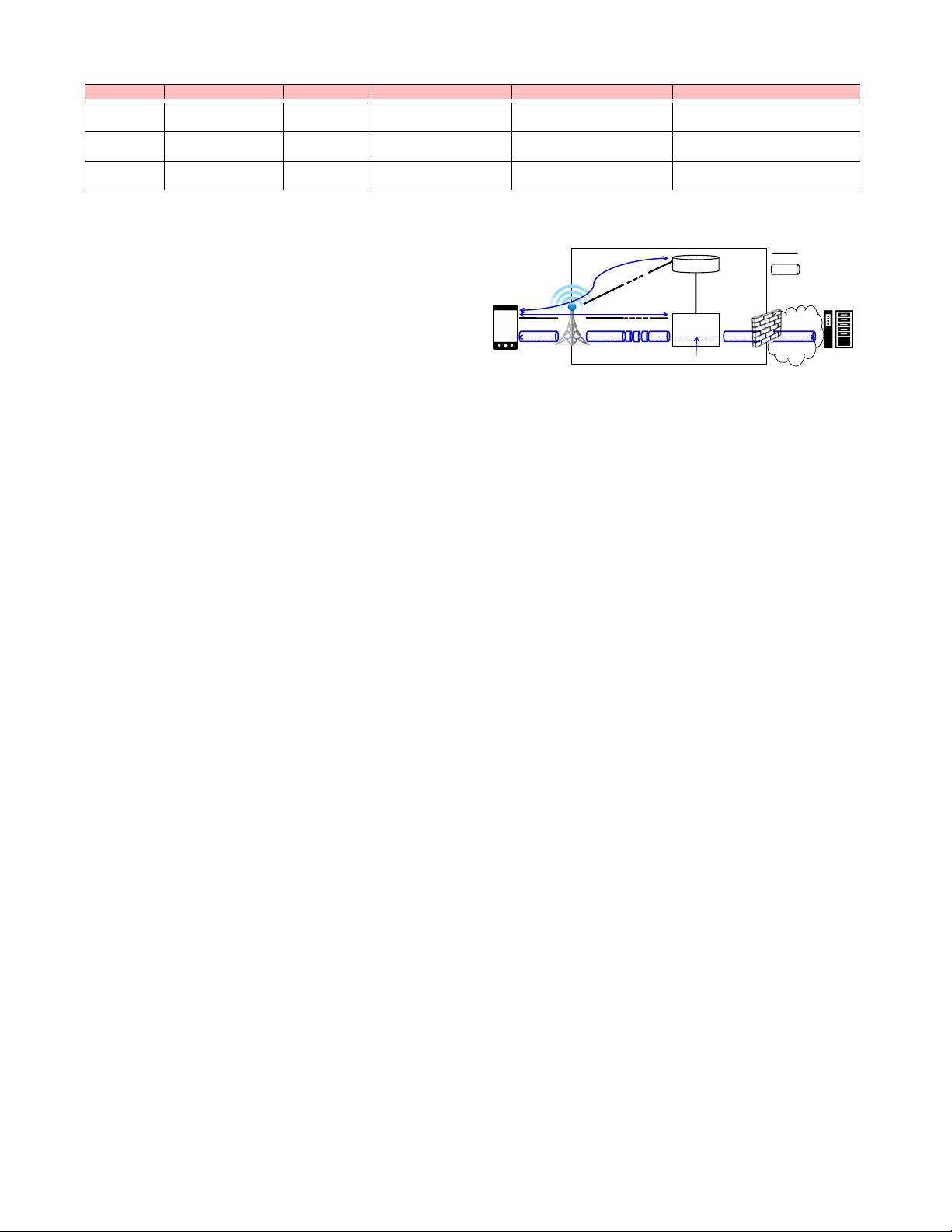
HSS!
P-GW!
Internet!
Data plane!
Control plane!
4G Network!
(1) User authentication!
(2) Bearer setup!
(3) Data transfer!
(4) Accounting!
Figure 1: Main operations for mobile data transfer and charg-
ing in 4G LTE networks.
§3 elaborate our security analysis on each AAA dimension. §4
proposes defense solutions and §5 evaluates them. §6 compares
with related work and §7 concludes the paper.
2. MOBILE DATA CHARGING IN 4G/3G
Figure 1 illustrates major operations for mobile data delivery and
its charging in cellular networks. We use 4G Long Term Evolution
(LTE) as the default network setting. The case for 3G networks is
similar. Specifically, there are four main steps. The first step is to
verify whether the user equipment (UE) is legitimate to use cellular
networks. It is mandatory except for dialing 911 calls. This is done
through user authentication when the UE initially attaches to cellu-
lar networks (e.g., the phone powers on). Second, the authenticated
UE establishes data bearers for subsequent transfer. It is a prereq-
uisite to obtain granted data access (i.e., IP connectivity) from the
cellular carrier before running data services.
Afterwards, it is ready to start any data service (e.g., web brows-
ing and video streaming) (Step 3). The data packets are delivered
from the UE to the base station, and then forwarded to the gateway
(i.e., P-GW in LTE), and finally to the external host, or vice verse.
At the border to the Internet, cellular operators deploy border gate-
ways and middleboxes, including firewalls and NATs [5, 38].
Volume accounting (Step 4) is performed in parallel with data
transfer. Usage volume is collected when data packets traverse the
gateway along both inbound (i.e., phone-destined) and outbound
(i.e., phone-originated) directions. To infer who should pay the
bill, the gateway uses a unique charging ID on a per-flow basis, or
on a per-IP basis. Each charging ID is correlated with a registered
user via the first two steps, as elaborated later.
2.1 Threat Model
We expose security vulnerabilities of the MDC system without
giving the adversary too much attack power. This is done by assum-
ing that all other components in the cellular networks and mobile
phone victims are not compromised and via limiting the exploits to
be used by the adversary.
Specifically, the adversary can be a mobile user or a static host
on the Internet, whereas the victim is typically another mobile user
and loses money due to attacks from the adversary. The victim user
can be chosen on purpose (given a specific phone number) or at
random. In some scenarios, the operator might become the victim
剩余11页未读,继续阅读
资源评论

mylyes
- 粉丝: 0
- 资源: 1
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功