
SESSION ID:
#RSAC
Dr. Luke Mather
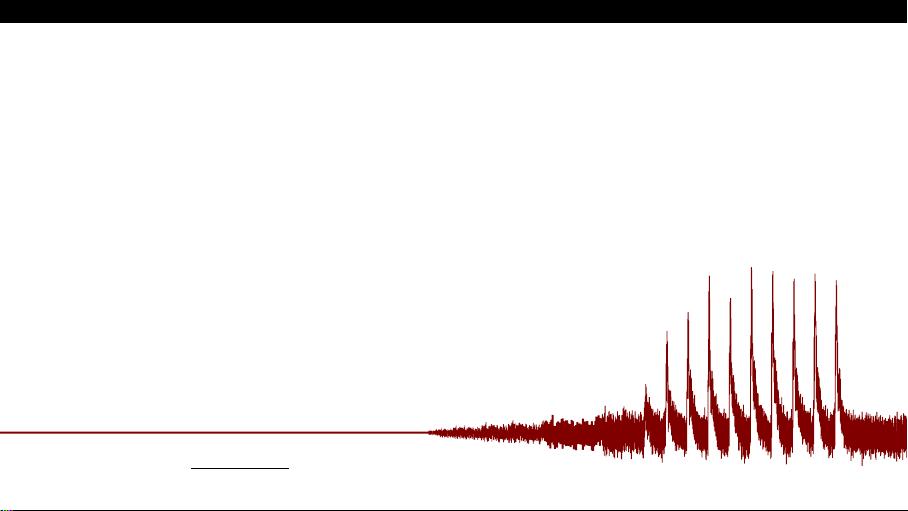
TWO SIDES OF THE SAME COIN:
COUNTING AND ENUMERATING KEYS
POST SIDE-CHANNEL ATTACKS
REVISITED
CRYP-F01
Research Associate
University of Bristol
 「安全运营」cryp-f01-side-channels-2 - 访问管理.zip (1个子文件)
「安全运营」cryp-f01-side-channels-2 - 访问管理.zip (1个子文件)  cryp-f01-side-channels-2.pdf 2.9MB
cryp-f01-side-channels-2.pdf 2.9MB



 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益
我的收益  我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功
评论0