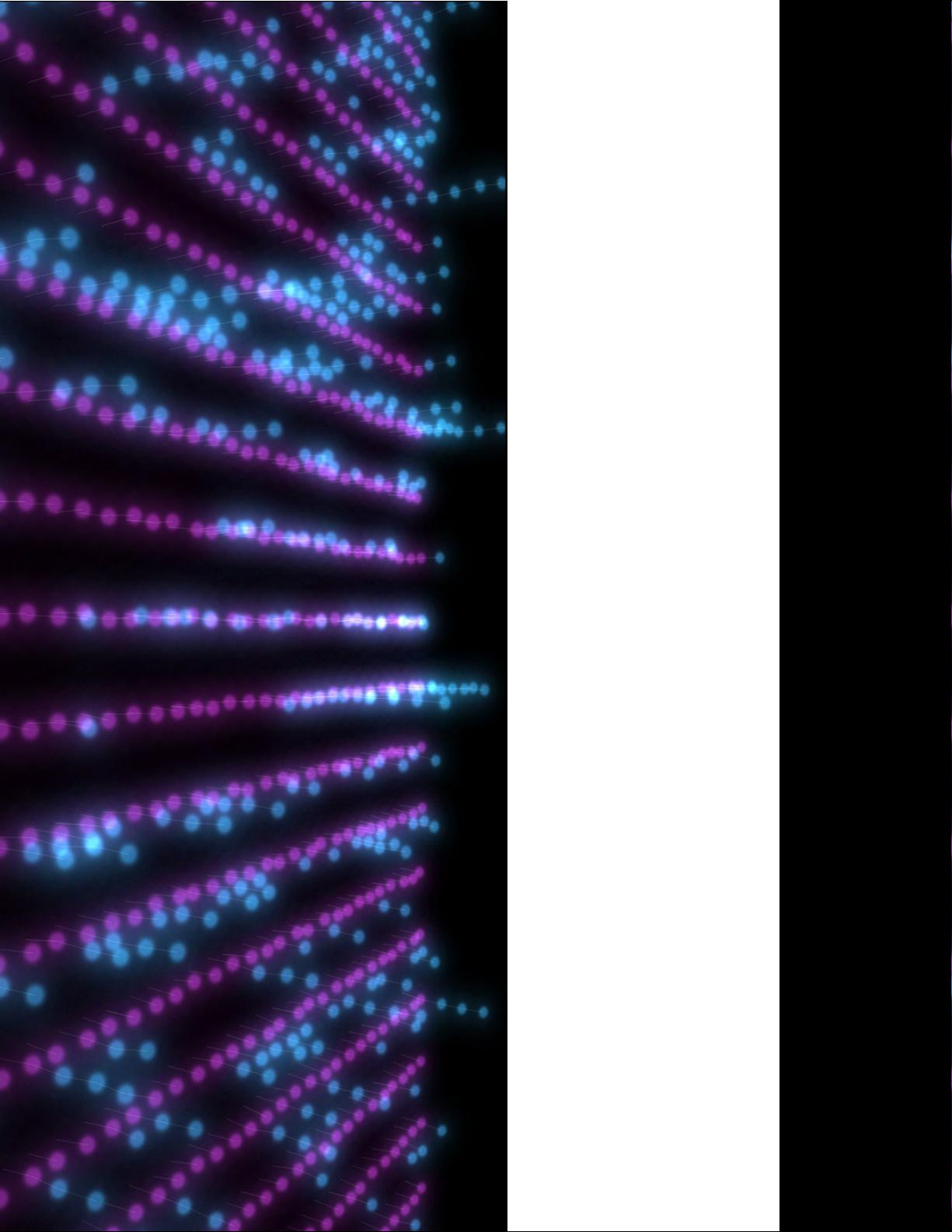
Network Science
Albert-László Barabási
Data Visualization by Mauro Martino
Data Analysis by Márton Pósfai

PDF Version:
November 2012

CHAPTER 1
Introduction
From Saddam Hussein to network
theory
Vulnerability due to interconnec-
tivity
Networks at the heart of complex
systems
Two forces helped the emergence
of network science
The characteristics of network
science
The impact of network science
Scientific impact
Summary
Bibliography
INTRODUCTION
SECTION 1
INTRODUCTION
This book aims to help teach network science to an inter-
disciplinary audience. Many of the choices I made in pre-
senting the material were guided by the desire to offer an
enjoyable, yet systematic introduction to the field. I kept in
mind that those entering the field are just as interested in
learning about the genesis of the concepts network science
introduced, as the tools they can use to study real networks
and interpret the obtained results.
Several over-arching themes are present in this book,
helping to offer an effective introduction:
(i) Given the empirical roots of network science, there is
strong emphasis on empirical data. We have therefore
assembled a set of ‘canonic’ databases, representing net-
works that are frequently analyzed in network science to
test various network characteristics. Whenever possible,
we use these datasets to illustrate the tools we introduce.
(ii) Given the potential diversity of the students interested
in the field that may be familiar with one domain of inqui-
ry but not other, we devote special sections to each data-
set. The goal is to offer some degree of familiarity with the
range of datasets explored in network science, and through
this diversity to learn about the issues pertaining to data
collection and curation.
This book is not a finished product but a work in progress.
Hence we continue to update it, adding additional chap-
ters as they are finished.
There is a dedicated website to this project (Image 1.1),
http://barabasilab.com/networksciencebook
that contains not only the chapters, but also the slides I
used in my classes to teach the material. Those who are in-
terested in teaching any part of the book are welcome to
use these slides. The website also offers tools to provide
feedback on the material, from comments to suggestions
for improvement.
Image 1.1 http://barabasilab.com/networksciencebook
2 | NETWORK SCIENCE
SECTION 2
FROM SADDAM HUSSEIN TO NETWORK THEORY
American forces encountered relatively little military re-
sistance as they took control of Iraq during the invasion
that started in March 19, 2003. Yet, many of the regime’s
high ranking officials, including Saddam Hussein, avoid-
ed capture.
Hussein was last spotted kissing a baby in Baghdad some
time in April 2003, and then his trace went cold. To aid
awareness of the officials they sought, the coalition forc-
es designed a deck of cards, each card engraved with the
image of one of the 55 most wanted. It worked. By May
1st 15 men on the cards were captured and by the end of
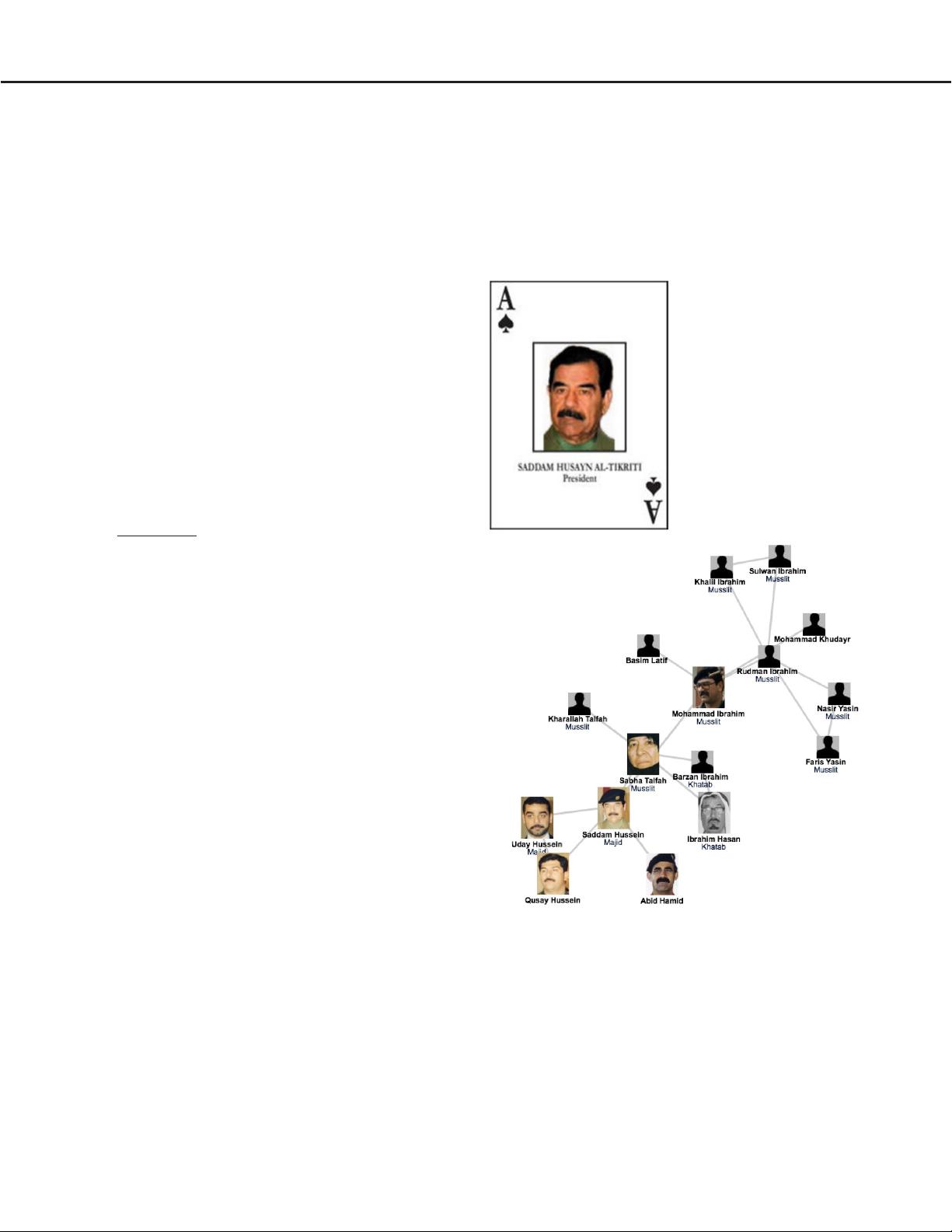
the month another 12 were under custody. Yet, the ace of
spades (Image 1.2a), i.e. Hussein himself, remained at
large.
Intelligence officials hoped that some of the high ranking
officials would surely know Hussein’s whereabouts. Yet,
it was not to be. This became painfully obvious after the
capture of Saddam’s trusted personal secretary and the ace
of diamonds. Newspapers trumpeted his mid-June cap-
ture as the war’s biggest feat, as this could lead to Sadd-
am’s whereabouts. Yet, the dictator parted ways with his
ally soon after the invasion, sending a clear signal to the
investigators: relying on the traditional lines of power was
of little help in trying to find him. Instead, they decided to
turn to a tool that had little presence in military thinking
before: network theory [1].
In 2003 network theory was an already burgeoning re-
search field, but the soldiers in the war zone had little ac-
cess to the exploding advances in this area. Instead, they
arrived to it through a healthy dose of common sense and
intuition. Col. James Hickey, in charge of a series of raids
known as Operation Desert Scorpion, wanted to know the
relationship between everyone killed or captured. The task
fell to Lt. Col. Steve Russell, who was in direct charge of the
raids, and Brian Reed, the operations officer under Hick-
ey, who was exposed to social networks during his studies
at West Point. Reed started to systematically reconstruct
the social network of Saddam’s inner circle. He did not rely
on government documents and decrees, but rather gossip
and family trees. As they meticulously pieced together an
extensive diagram of who is related to whom in the Tikrit
region, where Saddam was from, they started to use net-
work diagrams to guide the raids. In one of those raids they
found over $8 million in US currency, about $1 million in
Iraqi currency, jewelry worth over $2 million, rifles, and
ammunition. Yet, the biggest prize was Saddam’s family
photo album, providing the faces of those that the family
Image 1.2a
The network
of Saddam Hussein.
Ace of Spades. One of the 55 cards
the US military has handed out to the
coalition forces in Iraq, each listing a
top official to be captured following
the country’s 2003 invasion. The card
shows the ace of spades, with the im-
age of Saddam Hussein, Iraq’s deposed
president and dictator, the top prize of
the hunt.
Image 1.2b
The network of Saddam Hussein.
The Social Network. A small region of the social network reconstructed by
the US forces in the process of searching for Saddam Hussein. The map
represents the relationship between individuals in Saddam’s inner circle.
FROM SADDAM HUSSEIN TO NETWORK THEORY | 3















- 1
- 2
前往页