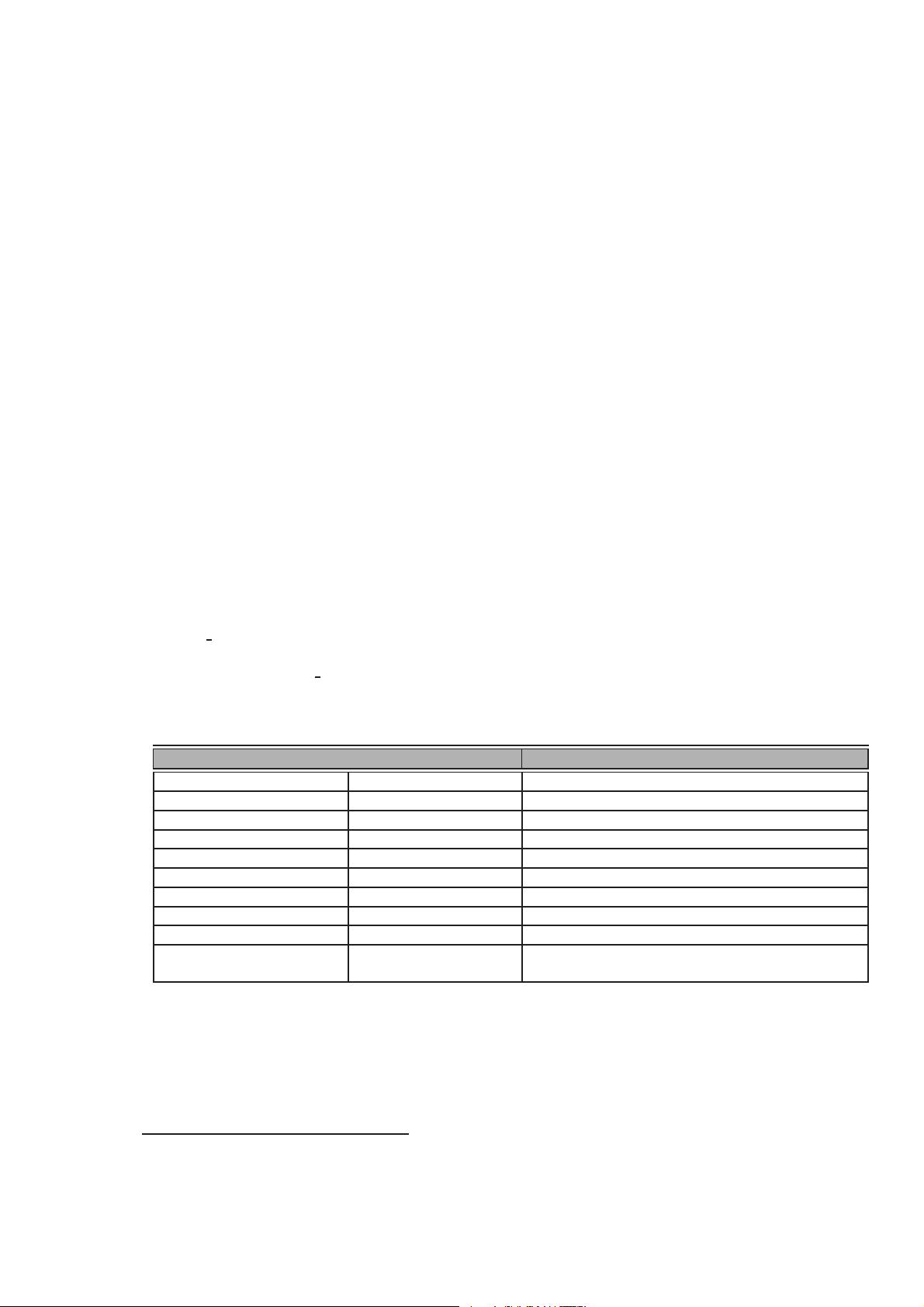
Cleartext Passwords in Linux Memory
Sherri Davidoff
alien@mit.edu
July 26, 2008
Abstract
Upon examination, the memory of a popular Linux distribution contained many cleartext
passwords, including login, SSH, Truecrypt, email, IM and root passwords. These passwords
are retained by running applications and stored as plain text in memory for extended periods
of time. The author investigated the source of these passwords and presents a proof-of-concept
method for recovering passwords from memory. Recently, cold boot researchers demonstrated
that memory is not as volatile as commonly expected, and that data from memory can be
recovered with physical access to systems in a very short period of time. This has open ed up
a new class of attacks in physical IT security, and significantly raised the risk associated with
cleartext passwords in memory.
1 Introduction
Memory contains a concentrated wealth of information, such as usernames , passwords, encryption
keys, and personal data. This information can be used by attackers to gain access to related
systems, or by forensic investigators to unlock encrypted files and partitions. The author of this
paper examined the contents of Linux memory, identified clea rtext passwords, investigated their
source, and determined a proof-of-concept signature-based method for recovering them.
The Linux test system consistently left cleartext passwords in memory, including the login, SSH,
email, IM, Truecrypt and root passwords. While cleartext passwords in memory have been a
known, relatively low security risk for many years, the issue has taken on new importance in
light o f the recent research o n cold boot data remnance in memory. In February 20 08, a team
led by Ed Felten of Princeton University discovered that DRAM is not a s volatile as commonly
exp ected. Felten’s team studied the lifetime of data in DRAM, and demonstrated that, “[c]ontrary
to po pular assumption, DRAMs used in most modern computers retain their contents for seconds
to minutes after power is lo st, even at room tempera tur e and even if removed from a motherboard.”
Felten’s team leveraged this discovery to retrive encryption keys from memory. In their paper, they
commented that “[r]esidual da ta can be recovered using simple, nondestructive techniques that
require only momentary physical access to the machine.”
1
In other words, in little more than the time it takes to reboot a system, attacke rs can dump
a system’s memory. Memory can be dumped onto a USB key or other device, such as the iPod
dumper demonstrated by William Paul and Jacob Appelbaum at the 2008 Cansec West conference.
It can also be dumped over the network. When memory conta ins cleartext passwords, the attacker
can retrieve these and use them to gain access to encrypted data, email accounts, servers and other
networked systems. Cold boot attacks significantly increas e the risk posed by cleartext passwords
and other sensitive data in memory.
To demonstrate tha t cleartext password recovery is achie vable, the author of this paper identified
bytes which consistently surrounded the cleartext Truecrypt password in memory and used these as
a signature to retrieve unknown Truecrypt passwords from memory on another L inux system. This
was accomplished using the Memsniff memory s e arching tools, which were originally developed and
released by Sherri Davidoff and Tom Liston at the 2008 Cansec West confer e nce .
2
1
Felten, Ed et al. “Lest We Remember: Col d Boot Attacks on Encryption Keys.” February, 2008
2
Davidoff and Liston, “Cold Boot Forensics Workshop,” Cansec West 2008,
1