
Integrity CAAM Driver
Documentation and User's Guide
December 2017, version 1
Table of Contents wolfSSL
3.12.2
1.0 INTRO
2.0 Building
2.1 Building The Driver
2.2 Building wolfSSL
3.0 Use
3.1 Initialization
3.2 Sending the Driver a Command
3.3 AES
3.3.1 AES-ECB
3.3.2 AES-CBC
© Copyright 2017 wolfSSL

1.0 INTRO
This driver was created to make use of iMX.6 hardware acceleration with the Integrity
OS. The driver operates from the kernel space where permission is granted to access
addresses needed to operate the CAAM. Permission to access these addresses are
restricted by the OS in a users application. The general flow for use is that a kernel with
the driver is made, then the user's application running on the created kernel makes a
request for the IODevice resource. After the application gets the IODevice it then sends
commands along with buffers to be processed. Section 3.0 about “Use” goes into more
detail about the commands and buffers passed to the IODevice. All code for the driver is
located at wolfssl-root/wolfcrypt/src/port/caam/caam_driver.c with a header file located
at wolfssl-root/wolfssl/wolfcrypt/port/caam/caam_driver.h.
The driver supports:
● AES-CCM
● AES-ECB
● AES-CBC
● AES-CTR
● MD5
● SHA1
● SHA-224
● SHA-256
● TRNG
● Blob creation and opening
NOTE: The same logic used for SHA-256/224 can be used for SHA-384/512 and is in place but has not completely been tested due
to hardware support.
2.0 Building
This covers two sections. First, building the kernel to incorporate the driver and second,
building wolfSSL to use the driver.
2.1 Building The Driver
● To build a kernel with the driver add the file caam_driver.c to the kernel build.
© Copyright 2017 wolfSSL
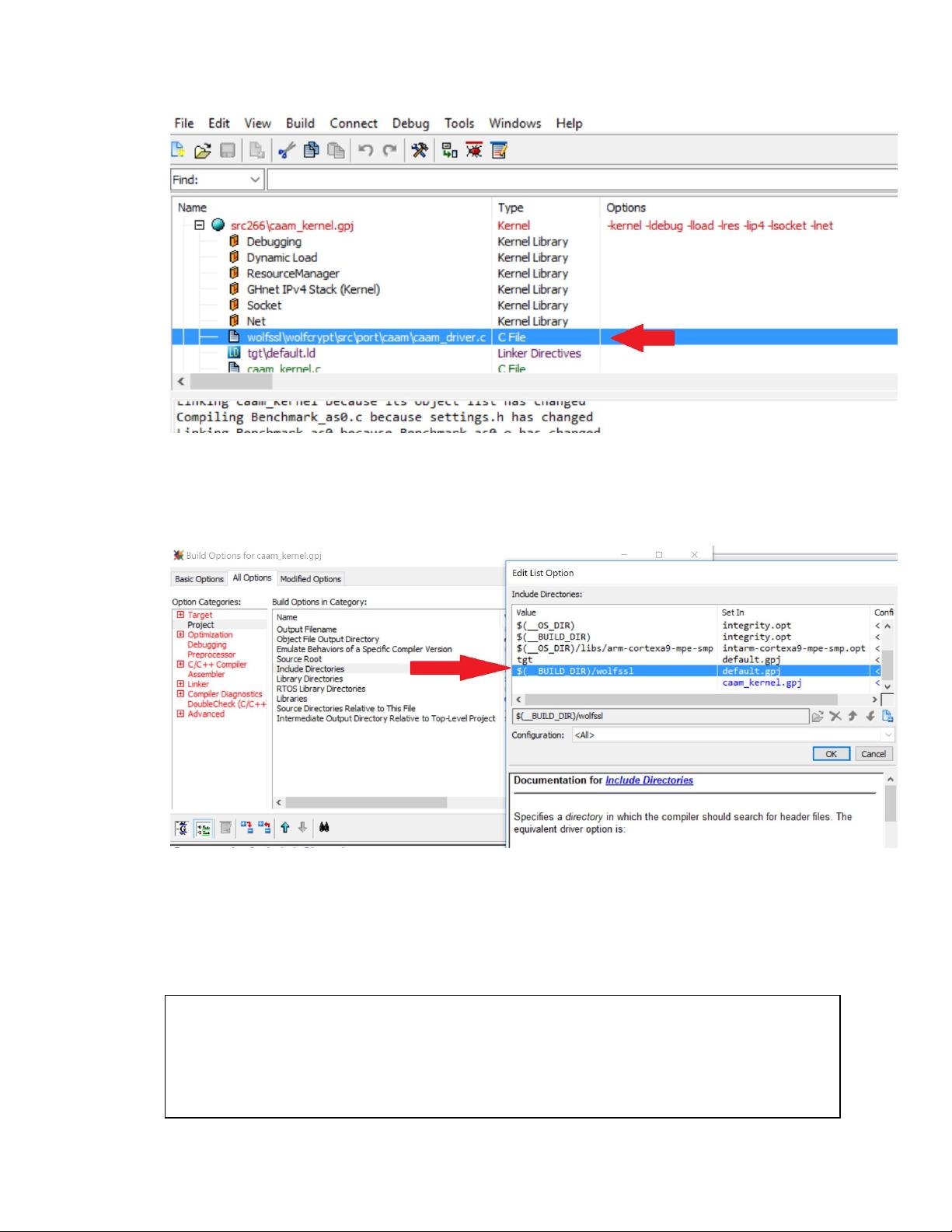
● The next step is to include the path to wolfssl-root for including the file
wolfssl/wolfcrypt/port/caam/caam_driver.h. This include path must be added to
the project.
● Next, build the project and create a .uimage from the output. This can be done in many
different ways, for the digiConnectCore6 board it was done using the elfloader.exe and
arm_elfloader.exe sent with Integrity along with using mkimage. The following is an
example of the commands that would be used if the kernel’s name in the MULTI project
was caam_kernel.
$ C:\ghs\comp_201516\elfloader.exe -l
C:\ghs\int1144\digiConnectCore6\arm_elfloader.bin -o
kernel.elf caam_kernel
$ mkimage -n wolfSSL -A arm -O Linux -C none -a 0x18000000 -d
kernel.elf kernel.uimage
© Copyright 2017 wolfSSL
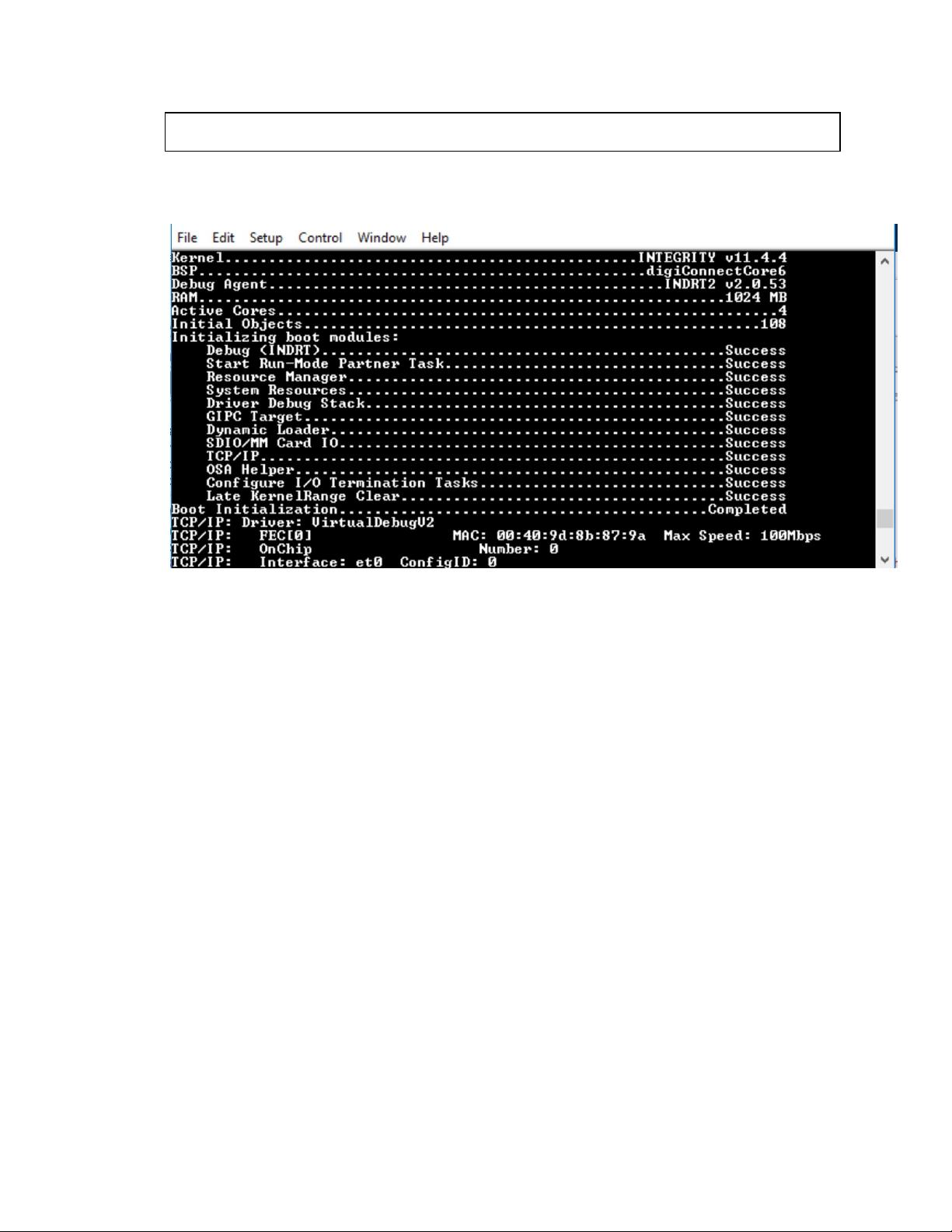
● After the uimage has been created place it in the root directory of an SD card and start
the board up with the SD card inserted.
● It is now ready for an application to be loaded.
2.2 Building wolfSSL
● This section covers building wolfSSL to make use of the driver. To build wolfSSL
source files from wolfssl-root/wolfcrypt/src/*.c (except misc.c if using INLINE),
source files from wolfssl-root/src/*.c and source files from
wolfssl-root/wolfcrypt/src/port/caam/*.c (except caam_driver.c) should be
compiled.
© Copyright 2017 wolfSSL

















