710 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 23, NO. 2, FEBRUARY 2014
Image Quality Assessment for Fake Biometric
Detection: Application to Iris, Fingerprint,
and Face Recognition
Javier Galbally, Sébastien Marcel, Member, IEEE, and Julian Fierrez
Abstract—To ensure the actual presence of a real legiti-
mate trait in contrast to a fake self-manufactured synthetic
or reconstructed sample is a significant problem in biometric
authentication, which requires the development of new and
efficient protection measures. In this paper, we present a novel
software-based fake detection method that can be used in multiple
biometric systems to detect different types of fraudulent access
attempts. The objective of the proposed system is to enhance the
security of biometric recognition frameworks, by adding liveness
assessment in a fast, user-friendly, and non-intrusive manner,
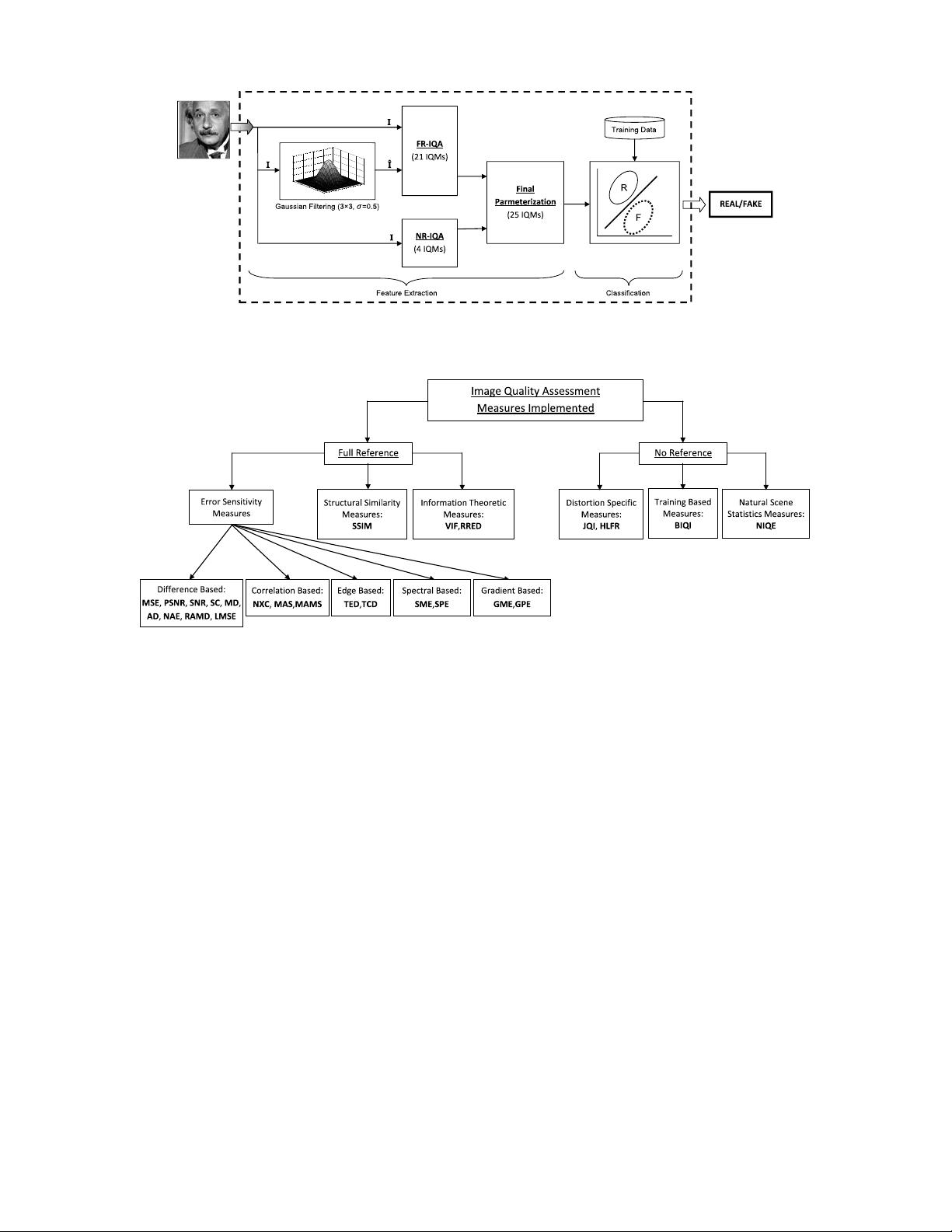
through the use of image quality assessment. The proposed
approach presents a very low degree of complexity, which makes
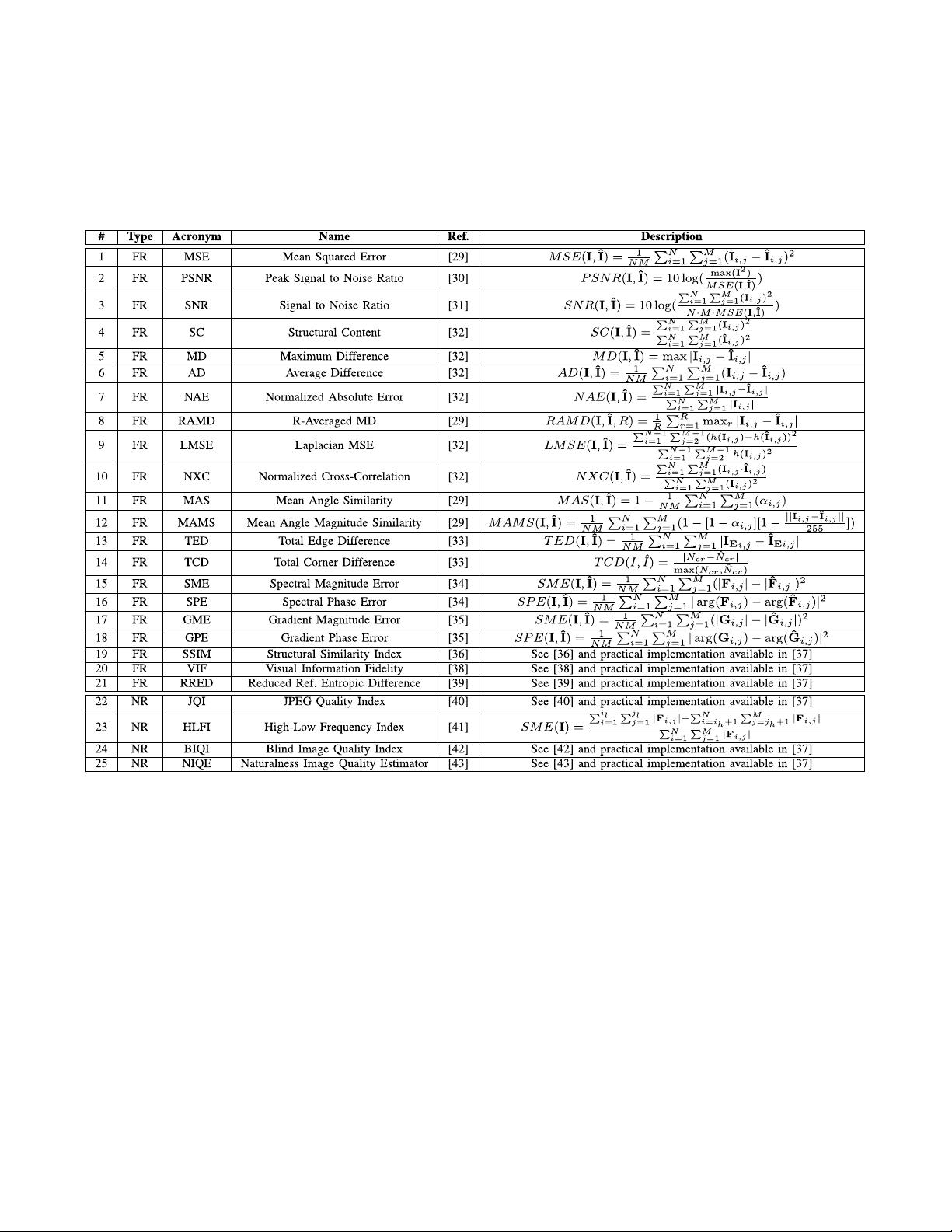
it suitable for real-time applications, using 25 general image
quality features extracted from one image (i.e., the same acquired
for authentication purposes) to distinguish between legitimate
and impostor samples. The experimental results, obtained on
publicly available data sets of fingerprint, iris, and 2D face,
show that the proposed method is highly competitive compared
with other state-of-the-art approaches and that the analysis of
the general image quality of real biometric samples reveals
highly valuable information that may be very efficiently used
to discriminate them from fake traits.
Index Terms—Image quality assessment, biometrics, security,
attacks, countermeasures.
I. INTRODUCTION
I
N RECENT years, the increasing interest in the evaluation
of biometric systems security has led to the creation of
numerous and very diverse initiatives focused on this major
field of research [1]: the publication of many research works
disclosing and evaluating different biometric vulnerabilities
[2], [3], the proposal of new protection methods [4], [5],
related book chapters [6], the publication of several stan-
dards in the area [7], [8], the dedication of specific tracks,
Manuscript received May 24, 2013; revised September 16, 2013;
accepted November 13, 2013. Date of publication November 21, 2013;
date of current version December 24, 2013. This work was sup-
ported in part by the Projects Contexts under Grant S2009/TIC-1485
from CAM, in part by Bio-Shield under Grant TEC2012-34881 from
Spanish MECD, in part by TABULA RASA under Grant FP7-ICT-
257289, in part by BEAT under Grant FP7-SEC-284989 from EU, and
in part by Cátedra UAM-Telefónica. The associate editor coordinating
the review of this manuscript and approving it for publication was
Prof. Stefano Tubaro.
J. Galbally is with the Joint Research Centre, European Commission, Ispra
21027, Italy (e-mail: javier.galbally@jrc.ec.europa.es).
S. Marcel is with the IDIAP Research Institute Centre du Parc, Martigny
1920, Switzerland (e-mail: sebastien.marcel@idiap.ch).
J. Fierrez is with the Biometric Recognition Group-ATVS, EPS, Universidad
Autonoma de Madrid, Madrid 28049, Spain (e-mail: julian.fierrez@uam.es).
Color versions of one or more of the figures in this paper are available
online at http://ieeexplore.ieee.org.
Digital Object Identifier 10.1109/TIP.2013.2292332
sessions and workshops in biometric-specific and general
signal processing conferences [9], the organization of competi-
tions focused on vulnerability assessment [10], [11], the acqui-
sition of specific datasets [12], [13], the creation of groups
and laboratories specialized in the evaluation of biometric
security [14], or the existence of several European Projects
with the biometric security topic as main research interest
[15], [16].
All these initiatives clearly highlight the importance given
by all parties involved in the development of biometrics
(i.e., researchers, developers and industry) to the improvement
of the systems security to bring this rapidly emerging technol-
ogy into practical use.
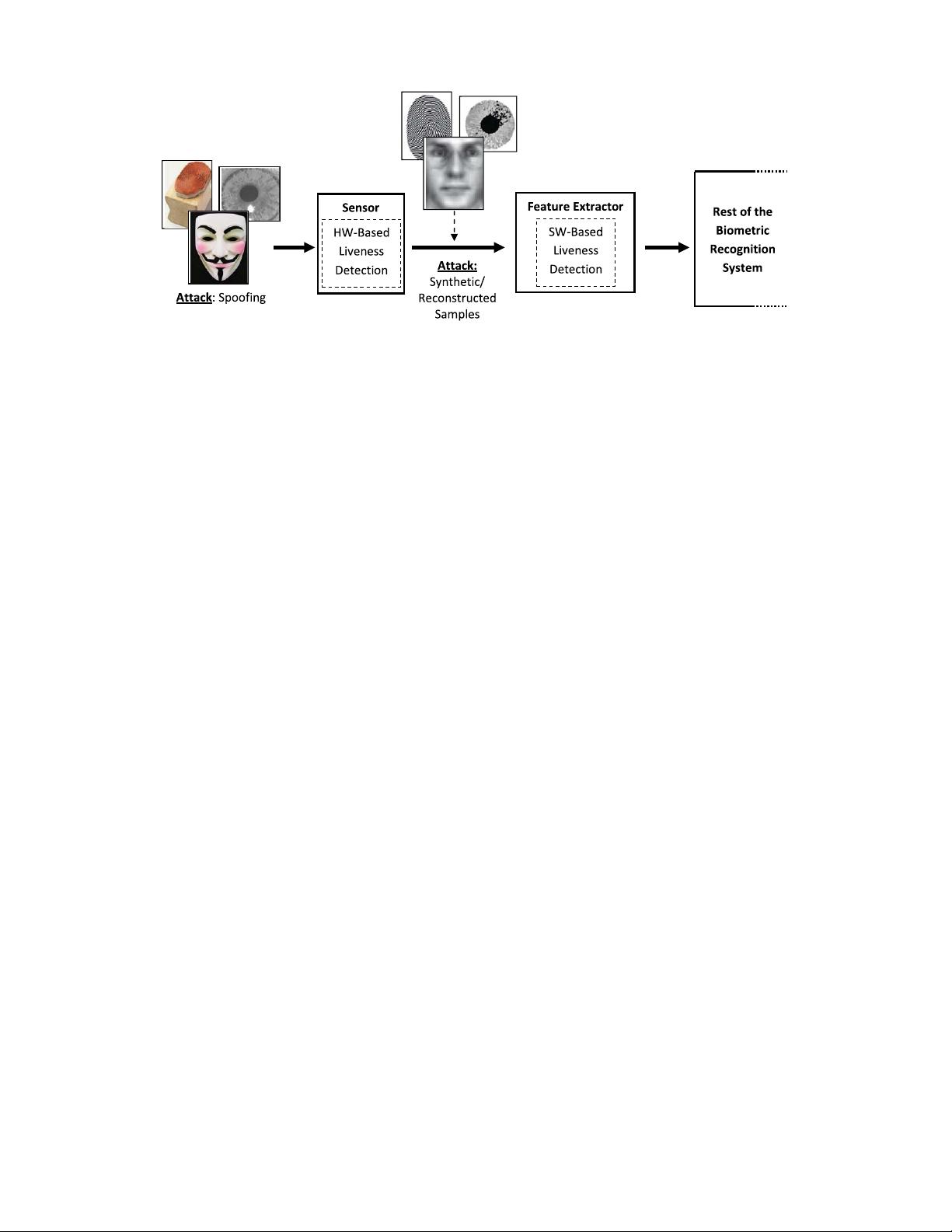
Among the different threats analyzed, the so-called direct
or spoofing attacks have motivated the biometric community
to study the vulnerabilities against this type of fraudulent
actions in modalities such as the iris [2], the fingerprint [17],
the face [13], the signature [18], or even the gait [19] and
multimodal approaches [20]. In these attacks, the intruder uses
some type of synthetically produced artifact (e.g., gummy
finger, printed iris image or face mask), or tries to mimic
the behaviour of the genuine user (e.g., gait, signature), to
fraudulently access the biometric system. As this type of
attacks are performed in the analog domain and the interaction
with the device is done following the regular protocol, the
usual digital protection mechanisms (e.g., encryption, digital
signature or watermarking) are not effective.
The aforementioned works and other analogue studies, have
clearly shown the necessity to propose and develop specific
protection methods against this threat. This way, researchers
have focused on the design of specific countermeasures that
enable biometric systems to detect fake samples and reject
them, improving this way the robustness and security level of
the systems.
Besides other anti-spoofing approaches such as the use
of multibiometrics or challenge-response methods, special
attention has been paid by researchers and industry to the
liveness detection techniques, which use different physiolog-
ical properties to distinguish between real and fake traits.
Liveness assessment methods represent a challenging engi-
neering problem as they have to satisfy certain demanding
requirements [21]: (i) non-invasive, the technique should in
no case be harmful for the individual or require an excessive
contact with the user; (ii) user friendly, people should not be
reluctant to use it; (iii) fast, results have to be produced in a
1057-7149 © 2013 IEEE

 毕业设计MATLAB_虚假生物特征检测的图像质量评估.zip (20个子文件)
毕业设计MATLAB_虚假生物特征检测的图像质量评估.zip (20个子文件)  soft
soft  psnr.m 258B
psnr.m 258B Train
Train  False
False  DSC_0098.bmp 1.32MB
DSC_0098.bmp 1.32MB DSC_0099.bmp 1.32MB
DSC_0099.bmp 1.32MB True
True  1369711_angles_05_ft_H_5_L.bmp 451KB
1369711_angles_05_ft_H_5_L.bmp 451KB 1369711_angles_05_ft_H_5_R.bmp 451KB
1369711_angles_05_ft_H_5_R.bmp 451KB False.mat 1KB
False.mat 1KB md.m 186B
md.m 186B snr.m 289B
snr.m 289B sc.m 202B
sc.m 202B main.m 6KB
main.m 6KB nae.m 199B
nae.m 199B main.fig 5KB
main.fig 5KB ad.m 210B
ad.m 210B mse.m 222B
mse.m 222B True.mat 862B
True.mat 862B test_lda.m 254B
test_lda.m 254B add_train.m 1KB
add_train.m 1KB ignore.txt 1B
ignore.txt 1B Image quality assesment.pdf 2.85MB
Image quality assesment.pdf 2.85MB license.txt 1KB
license.txt 1KB





 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助 
 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜

 信息提交成功
信息提交成功