没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论

TrendLabs

Below is an overview of the most significant findings of the files from the compromised FTP
related to the operation.
The compromised FTP contained various files and tools the attackers used. The first files found
were configuration files for some toolsets. From part of one script, we recovered code that we
used to obtain a list of 80 million IP addresses. Further research suggested it was the way to
generate a randomized target list, which would make uncovering the real target within the
decoy systems more difficult.
".d.php" returned all the parameters. Submitting each parameter to the URL
/128[.]199[.]255[.]180/src/[.]xpf/ips/$param returns a list of IP addresses for each particular
parameter.
Figure 1. Parameter returns an IP address
All the IP addresses were saved on the lists, called by the invoking parameter with the
following script:
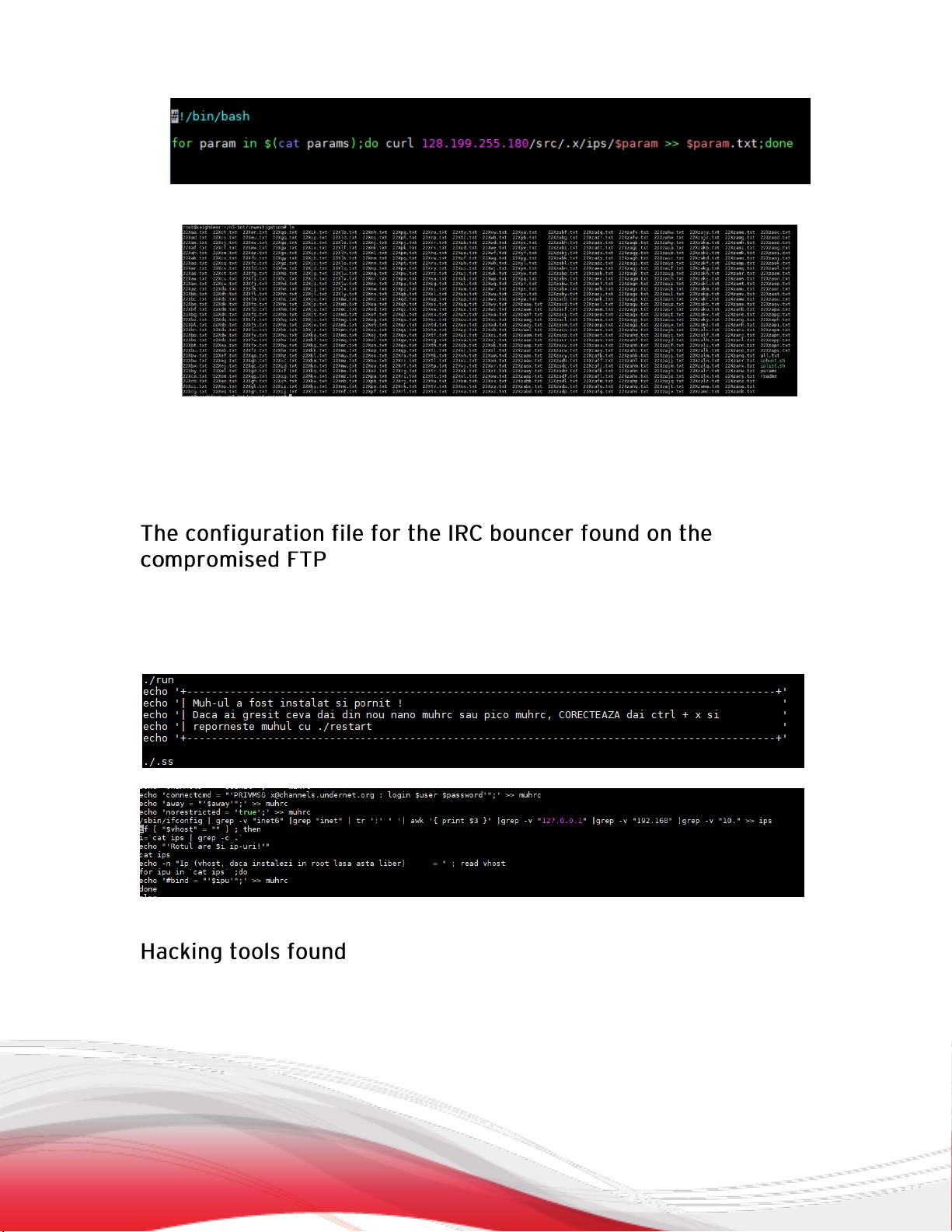
Figure 2. Script saving all the listed IP addresses into a text file
Figure 3. All the downloaded files
The supposed studio or the site itself has no business relevance, with no domain name
linked to its business. It is likely that the whole website is just a covert page used to
confuse the researchers and to disguise their operations.
This was the only seemingly working version of the toolset in development. It had various
parts of open-source codes from other operations, and its initial purpose was to build an
IRC-operated XMR miner with the ability to mask itself as another process. The Linux
hacking tool “Shark” was found within these files.
Figure 4 and 5. Comments in the Romanian language re: the IRC bouncer
We also found open-source hacking tools with custom wrap-up bash scripts with
comments written in the Romanian language. Among the files, there was a new toolkit
剩余18页未读,继续阅读
资源评论

虫虫搜奇
- 粉丝: 2
- 资源: 1
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功