没有合适的资源?快使用搜索试试~ 我知道了~
资源推荐
资源详情
资源评论
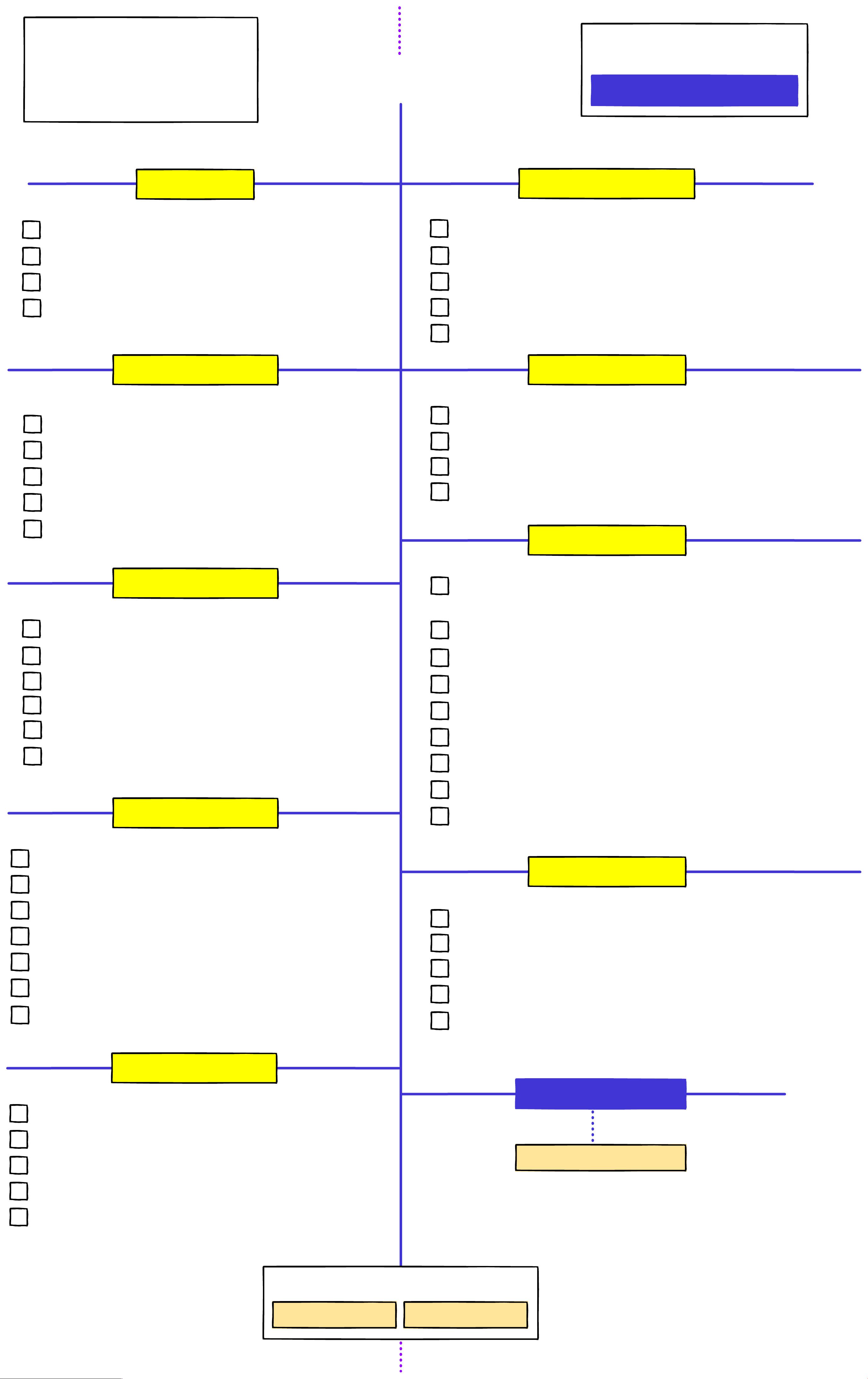
Avoid ‘Basic Authentication’, use standard (e.g. JWT)
API Security
Find the detailed version of this checklist
With details on how to implement these
https://roadmap.sh
Backend Roadmap
DevOps Roadmap
Related Roadmaps
Authentication
OAuth
More Resources
Recommended Resources
Continue Learning with following relevant tracks
DevOps RoadmapBackend Roadmap
Do not reinvent the wheel in authentication mechanisms.
Use `Max Retry’ and jail features in Login.
Use encryption on all sensitive data.
JWT (JSON Web Token)
Use good `JWT Secret` to make brute force attacks di!cult
Do not extract the algorithm from the header, use backend
Make token expiration (TTL, RTTL) as short as possible
Avoid storing sensitive data in JWT payload
Keep the payload small to reduce the size of the JWT token
Access Control
Limit requests (throttling) to avoid DDoS / Brute Force
Use HTTPS on server side and secure ciphers
Use HSTS header with SSL to avoid SSL Strip attacks.
Turn o" directory listings
Private APIs to be only accessible from safe listed IPs
Always validate `redirect_uri’ on server-side
Avoid `response_type=token’ and try to exchange for code
Use `state’ parameter to prevent CSRF attacks
Have default scope, and validate scope for each application
Input
User proper HTTP methods for the operation
Validate `content-type` on request header
Validate user input to avoid common vulnerabilities
Use standard Authorization header for sensitive data
Use only server-side encryption
Use an API Gateway for caching, Rate Limit policies etc
Processing
Check if all the endpoints are protected behind authentication
to avoid broken authentication process
Avoid user’s personal ID in the resource URLs e.g. users/242/orders
Prefer using UUID over auto-increment IDs
Disable entity parsing if you are parsing XML to avoid XXE attacks
Disable entity expansion if using XML, YML or any other language
Use CDN for file uploads
Avoid HTTP blocking if you are using huge amount of data
Make sure to turn the debug mode o" in production
Use non-executable stacks when available.
Output
Send `X-Content-Type-Options: nosni"` header
Send `X-Frame-Options: deny` header.
Send `Content-Security-Policy: default-src 'none'` header.
Remove fingerprinting headers (i.e. x-powered-by etc)
Force `content-type` for your response.
Avoid returning sensitive data (credentials, sec. tokens etc)
Return proper response codes as per the operation
CI & CD
Audit your design and implementation with unit/integration tests.
Use a code review process and disregard self-approval.
Continuously run security analysis on your code.
Check your dependencies for known vulnerabilities.
Design a rollback solution for deployments.
Monitoring
Use centralized logins for all services and components.
Use agents to monitor all requests, responses and errors.
Use alerts for SMS, Slack, Email, Kibana, Cloudwatch, etc.
Ensure that you aren't logging any sensitive data.
Use an IDS and/or IPS system to monitor everything.
资源评论

天涯学馆
- 粉丝: 2658
- 资源: 440
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- 创意精美的手机维修企业网站模板下载.rar
- 创意精美风的咖啡研磨机企业网站模板下载.zip
- 创意精美的网站设计师主页模板展示网站模板下载.zip
- 创意精美风的结婚婚礼倒计时网站模板下载.zip
- 创意精美通用的个性网站模板下载.zip
- 创意精美干净的休闲午后咖啡时光网站模板下载.zip
- 创意精美风的星巴克下午茶小店网站模板下载.rar
- 创意精致大气风的绘画企业整站模板下载.zip
- 创意精致粉色的设计企业整站模板下载.zip
- 创意精致风的办公家具设计网站模板下载.zip
- 创意精致风的互联网设计公司网站模板下载.zip
- 创意精致风的摄影工作室作品案例官网模板下载.zip
- 创意精致风的设计服务网页模板下载.zip
- 创意精致风的时尚设计网站模板下载.zip
- 创意精致效果的个性网站模板下载.zip
- 创意精致效果的博客网页模板下载.zip
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功